usd-2025-0026 | Agorum core open 11.9.1.3-1857 - Improper Neutralization of Input During Web Page Generation (Cross-site Scripting)
Product: Agorum core open
Affected Version: 11.9.1.3-1857
Vulnerability Type: Improper Neutralization of Input During Web Page Generation (Cross-site Scripting) (CWE-79)
Security Risk: High
Vendor: Agorum
Vendor URL: https://www.agorum.com/
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE Number: Requested
CVE Link: Requested
Advisory ID: usd-2025-0026
Description
agorum core is an open-source Enterprise Content Management (ECM) system developed by agorum Software GmbH in Germany. It offers a modular, highly customizable platform for document management, workflow automation, and digital collaboration.
Proof of Concept
agorum core is affected by numerous reflected cross-site scripting (XSS) vulnerabilities across a wide range of parameters, indicating a lack of proper input sanitization and output encoding. These flaws can be exploited by attackers to inject malicious scripts, potentially compromising user sessions, stealing credentials, or defacing content. The widespread nature of the vulnerabilities suggests systemic issues in the application's input handling architecture.
The following request can be crafted and sent to a victim. When opened, it executes JavaScript within the context of the victim’s browser session:
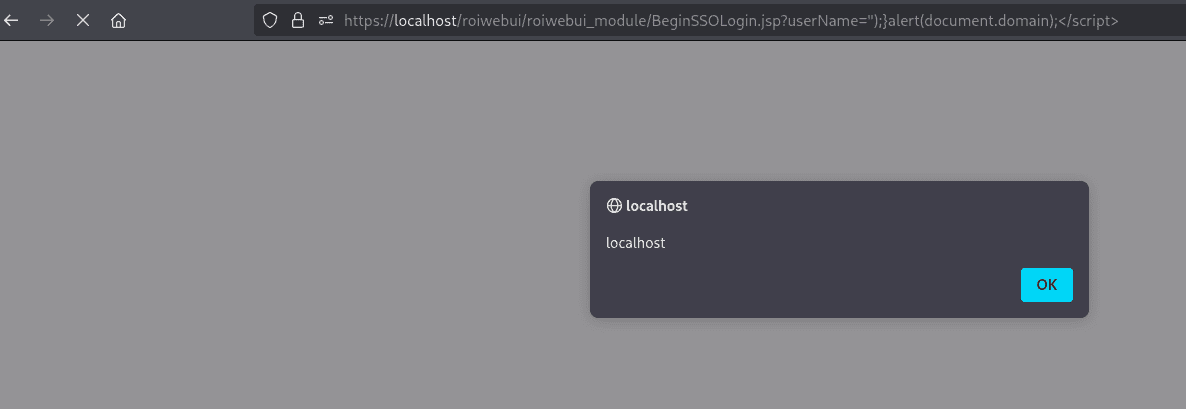
GET /roiwebui/roiwebui_module/BeginSSOLogin.jsp?userName=%22);}alert(document.domain);%3C/script%3E HTTP/1.1
Host: localhost
[...]
In the server's response, the user-supplied JavaScript is reflected and executed, resulting in an alert dialog, as demonstrated in the screenshot below:
As previously mentioned, the payload above is provided as an example. There are numerous other endpoints that exhibit the same vulnerability. A non-exhaustive list includes:
- OpenDocumentMessage.jsp
- ShowSSOMessageBox.jsp
- SSO.jsp
- SSOConvertToPdf.jsp
- SSOFileListStart.jsp
- SSOPageStart.jsp
- SSOKeepAlive.jsp
- SSOPortal.jsp
- SSOPortalWindow.jsp
- SSOPortalTabFrameSet.jsp
- SSOSearchMask.jsp
- SSOSearchMaskStart.jsp
- ReExtendedSearch.jsp
- ClientNewWindowsLoader.jsp
- RSSReader.jsp
- ReportingFrameSet.jsp
Fix
It is strongly recommended to implement robust input validation and output encoding across all user-supplied parameters. Adopt a security-focused development framework or library that provides built-in protections against XSS, and ensure that all dynamic content rendered in the browser is properly escaped based on context (e.g., HTML, JavaScript, URL).
Users of agorum core open can upgrade to versions 11.9.2 and 11.10.1.
References
Timeline
- 2025-05-05: First contact request via mail.
- 2025-05-05: The vendor has confirmed the delivery and has begun investigating the matter.
- 2025-05-07: The vendor has begun addressing and fixing the issue.
- 2025-05-15: The vendor has addressed and fixed the vulnerability within the cloud instances.
- 2025-05-30: The vendor released fixed versions 11.9.2 and 11.10.1.
- 2025-06-27: This advisory is published.
Credits
This security vulnerability was identified by Jakob Steeg, Roman Hergenreder, Florian Kimmes, Kai Glauber, DR and Ole Wagner of usd AG.