usd-2020-0054 | Gophish v0.10.1
Advisory ID: usd-2020-0054
CVE Number: CVE-2020-24710
Affected Product: Gophish
Affected Version: v0.10.1
Vulnerability Type: Stored Cross-Site Scripting
Security Risk: Medium
Vendor URL: https://getgophish.com/
Vendor Status: Fixed
Description
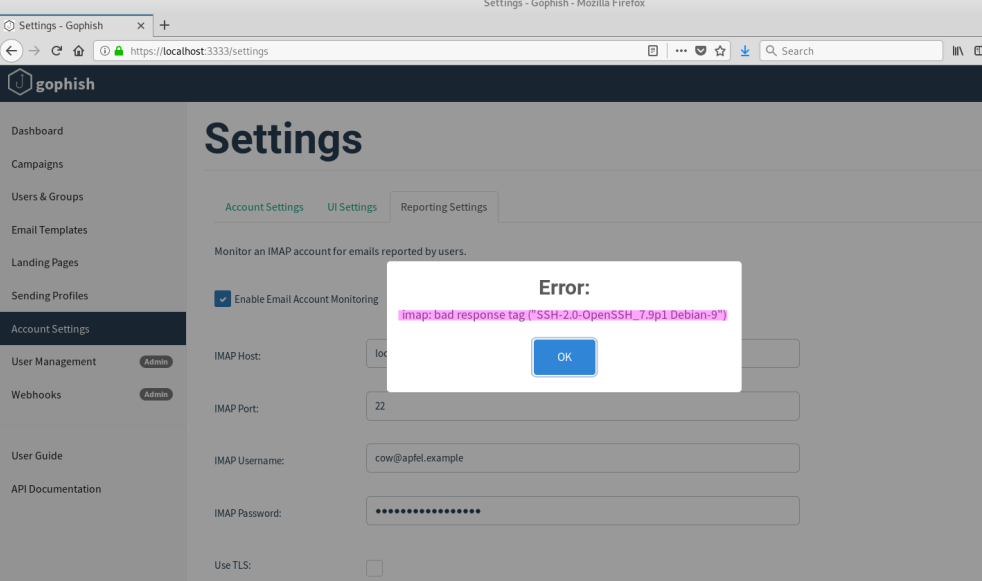
Several occurrences of server-side request forgery were found during the pentest. These could be used to perform port scans of the server that hosts Gophish. In the majority of cases the error message resulting from querying the local server, with localhost or a loopback address, discloses the banner of the tested service. And in one case, where the banner was not visible, long response times indicated that the port was available. The screenshot below illustrates a successful port scan of the local host.
Proof of Concept (PoC)
URL: /webhooks
Comment: It is possible for a remote user to scan the open ports of the server that hosts the gophish admin application. Furthermore, the error messages reveals parts of the available service’s banners. For example SSH’s “Debian-9“.
URL: /sending_profiles
Comment: It is possible for a remote user to scan the open ports of the server that hosts the gophish admin application. Open ports are disclosed by long response times after pressing the “Send“ button of the “Send Test Email“ feature.
URL: /landing_pages
Comment: It is possible for a remote user to scan the open ports of the server that hosts the gophish admin application. Furthermore, the error messages reveals parts of the available service’s banners. For example SSH’s “Debian-9“.
URL: /settings
Comment: It is possible for a remote user to scan the open ports of the server that hosts the gophish admin application. Furthermore, the error messages reveals parts of the available service’s banners. For example SSH’s “SSH-2.0-OpenSSH_7.9p1 Debian-9“.
Fix
A whitelist approach is not a valid solution when a user can make the application send requests to any external IP address or domain name. Despite knowing that the blacklist approach is not an impenetrable wall, it is the best solution in this scenario since it would inform the application to not send any requests to the server’s loopback addresses or to private IP address ranges.
Timeline
- 2020-06-18 First contact request via security@getgophish.com
- 2020-06-22 Vendor responds to initial contact
- 2020-08-20 Vendor publishes a fix https://github.com/gophish/gophish/commit/e3352f481e94054ffe08494c9225d3878347b005
- 2020-09-29 Security advisory released
Credits
This security vulnerability was found by Marcus Nilsson of usd AG.