usd-2022-0030 | Jellyfin 10.8.1 - Cross-Site Scripting
Advisory ID: usd-2022-0030
Product: Jellyfin
Affected Version: 10.8.1
Vulnerability Type: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') (CWE-79)
Security Risk: CRITICAL
Vendor URL: https://jellyfin.org
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE Number: CVE-2023-23636
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-23636
Description
The playlist name in Jellyfin 10.8.1 is vulnerable to a stored XSS which allows a low privileged user to steal access tokens from high privileged users.
The injected code is triggered everytime a user visits the playlist page. Since access tokens are stored in the localStorage an attacker is able to take over accounts by reading their values.
Proof of Concept
The following screenshot shows the executed JavaScript payload in the victim's browser.
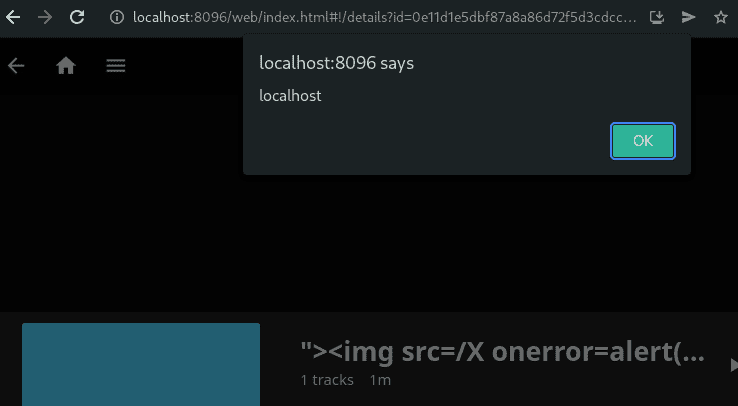
The following request creates a payload with injected name.
POST /Playlists?Name=%22%3E%3Cimg%20src%3D%2FX%20onerror%3Dalert(document.domain)%3E&Ids=0358e400bf19a370e7f2e4e69f2af64d&userId=e9239683c3384717810a900f1c2c7eb5 HTTP/1.1 Host: localhost:8096 Content-Length: 0 sec-ch-ua: "Chromium";v="97", " Not;A Brand";v="99" accept: application/json Content-Type: application/json [...]
Fix
It is recommended to treat all input on the website as potentially dangerous.
Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
The majority of programming languages support standard procedures for encoding meta characters.
References
- https://owasp.org/www-community/attacks/xss/
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-23636
Timeline
- 2022-07-18: First contact request via security@jellyfin.org
- 2022-08-02: Vulnerability details submitted
- 2022-08-16: Fixed by Vendor
- 2023-01-16: Requested CVE assigned
- 2023-01-19: The advisory is published
Credits
This security vulnerability was found by Christian Pöschl of usd AG.