usd-2025-0019 | d.3one 1.14.16 - Reflective Cross-Site Scripting
Product: d.3one
Affected Version: 1.14.16
Vulnerability Type: Cross-Site Scripting (CWE-79)
Security Risk: High
Vendor: d-velop
Vendor URL: https://www.d-velop.de/
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed in version 7.30.13 and 7.33.3
CVE Number: Requested
CVE Link: -
Advisory ID: usd-2025-0019
Description
By activating a malicious link, it is possible to execute JavaScript in the victim's browser. This can be exploited to call functions in the web interface on behalf of the victim and extract the content of the application. This compromises the confidentiality and integrity of the processed data.
Proof of Concept
The following URL opens an alert box with the current domain name as an example:
https://d3one-int.[...].local/shell/ng/#?pentest=1"><img]() src=x onerror=alert(document.domain)>
Screenshot of the alert box opened via JavaScript:
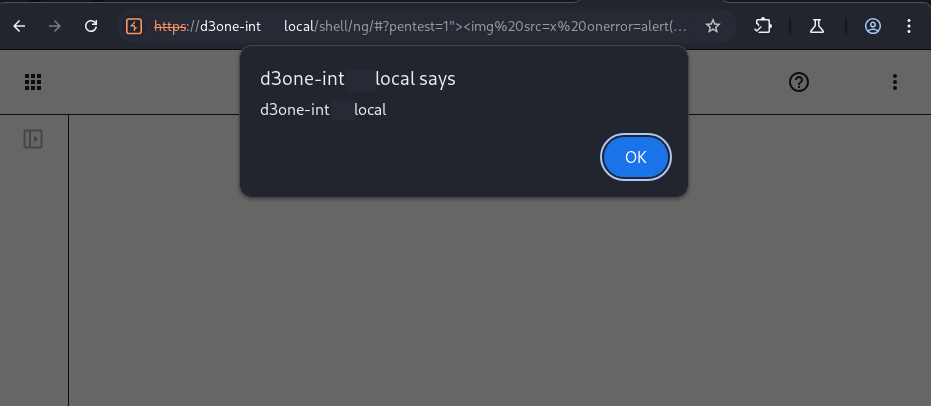
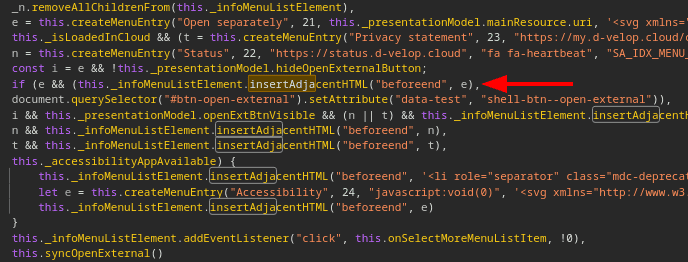
The cause of the vulnerability is the use of the insecure function Element.insertAdjacentHTML without prior parameter clearing. The following screenshot shows an excerpt of the vulnerable code:
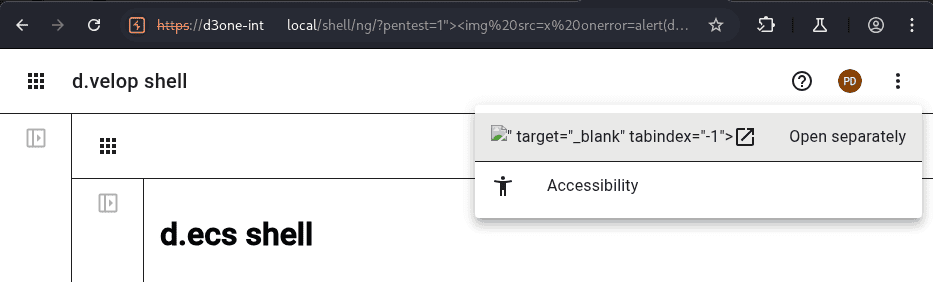
After opening the above URL in the application, you can also see where the payload was embedded, as this has changed the HTML.
The Mozilla documentation on the vulnerable function points out that no user input that has not been cleared should be used: <https://developer.mozilla.org/de/docs/Web/API/Element/insertAdjacentHTML#sicherheitshinweise>
Fix
The use of insecure functions should be prevented.
References
- https://owasp.org/www-community/attacks/xss/
- https://developer.mozilla.org/de/docs/Web/API/Element/insertAdjacentHTML#sicherheitshinweise
Timeline
- 2025-04-15: First contact request via mail
- 2025-04-15: Response from d.velop
- 2025-04-22: Vulnerability details sent to d.velop
- 2025-04-22: d.velop confirmed the delivery and begun investigating the matter.
- 2025-04-30: d.velop fixed the vulnerability.
- 2025-05-13: d.velop released fixed versions 7.30.13 and 7.33.3
Credits
This security vulnerability was identified by Konstantin Samuel of usd AG.