usd-2025-40 | PRTG Network Monitor 25.2.108 - Reflected XSS
Product: PRTG Network Monitor
Affected Version: <25.2.108
Vulnerability Type: Cross-Site Scripting (CWE-79)
Security Risk: High
Vendor: Paessler
Vendor URL: https://www.paessler.com/de
Vendor acknowledged vulnerability: Yes
Vendor Status: Yes
CVE Number: CVE-2025-67834
CVE Link: https://www.cve.org/CVERecord?id=CVE-2025-67834
Advisory ID: usd-2025-40
Description
The application does not properly encode or filter user-supplied data, which allows reflective injection of JavaScript code.
This occurs when the web server embeds input containing JavaScript into HTTP responses without sufficient encoding.
The input is not persistently stored but only temporarily reflected and executed within the browsing context of the user.
To perform a reflected XSS attack, an attacker has to induce the victim to issue a malicious request, for example by providing a prepared link.
A reflected XSS vulnerability can be exploited in various ways.
A common attack is to steal sensitive information from the user and secretly transmit it to the attackers.
Alternatively, attackers can perform actions with the rights of the user.
Proof of Concept
The filters of tables are vulnerable to reflected Cross-Site Scripting (XSS) attacks.
This allows attackers to inject arbitrary JavaScript code into the website by manipulating the URL.
This can be exploited to craft malicious links that when clicked on, will execute the attacker's JavaScript code in the browser of the user.
As the session cookie does not have the HTTPOnly flag set, attackers can steal the user's session cookie and perform administrative actions.
The following payload injects JavaScript code into the webpage that opens a popup with the user's session cookie as soon as their mouse enters the browser window.
The payload must be inserted into one of the filters in the URL's query parameter filters.
%20onmouseover=alert(document.cookie)%20style='position:absolute;width:100%25;height=100%25;left:0;top:0'
The following example shows a malicious link with the payload above.
[https://[REDACTED]/controls/table.htm?tableid=sensortable&content=sensors&columns=sensor%2Cprobegroupdevice%2Cstatus%2Clastvalue%2Cmessage%2Cminigraph%2Cpriority%2Cfavorite%2Csize%3Dhtmllong%2Ccheckbox&tools=pause%2Cacknowledge%2Cfave%2Cprio%2Cscan%2Cdelete%2Cedit&sortby=priority&sortable=true&refreshable=true&tabletitle=AUTO&varexpand=filters&filters=words!sensors%2Cobjects!data-filtername%3Dxss%20onmouseover=alert(document.cookie)%20style='position:absolute;width:100%25;height=100%25;left:0;top:0'&id=24264]()
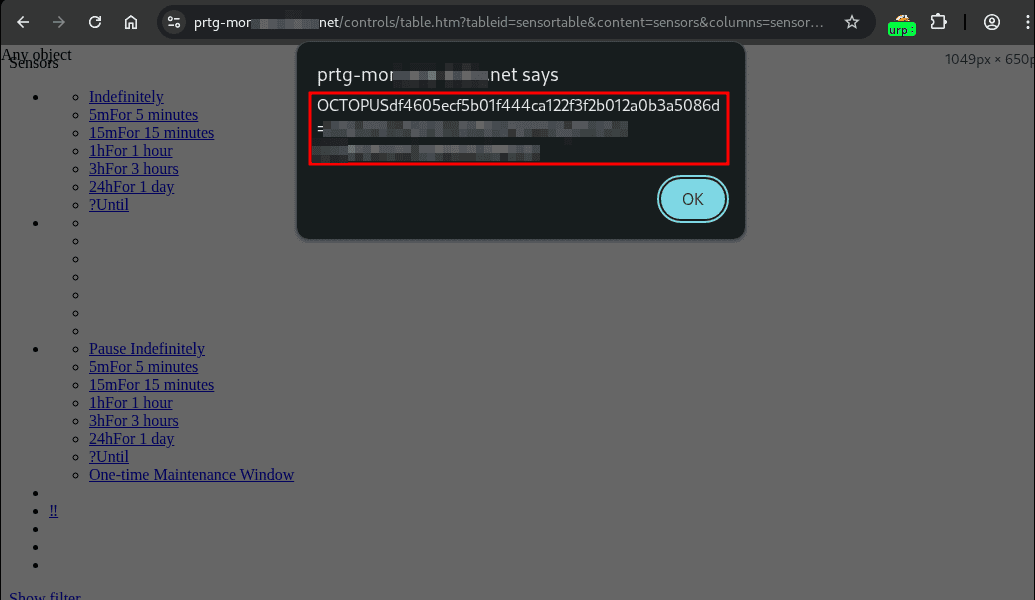
When a user clicks on the link, the injected JavaScript code is executed in their browser.
By utilizing phishing, attackers could persuade an administrator to click on the link, steal their session cookie and perform critical administrative actions with it.
The following screenshot shows the user's view after they click on the malicious link shown above.
Fix
It is recommended to treat all input on the website as potentially dangerous.
Invalid values should not be sanitized and forwarded to the application, but instead rejected.
To achieve this, all input should be validated on the server-side.
Where possible, a list of allowed characters should be defined.
The more restrictive a filter can be specified, the better the protection it provides.
Allowlists are especially recommended if input values have a well defined format or a list of valid input values exists.
Additionally, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
The majority of programming languages support standard procedures for encoding meta characters.
Further details on how to prevent XSS vulnerabilities can be obtained in the XSS Prevention Cheat Sheet by OWASP.
References
- https://owasp.org/www-community/attacks/xss/
- https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet
Timeline
- 2025-09-12: Vulnerabilities reported to Paessler.
- 2025-11-29: Release of PRTG version 25.4.114.1032.
- 2025-12-17: PRTG Hosted Monitor is upgraded to PRTG version 25.4.114.1032.
- 2026-01-13: Public disclosure of this vulnerability.
Credits
This security vulnerability was identified by Simon Kurz and Tobias Hennhoefer of usd AG.