usd-2019-0051 | Dolibarr ERP/CRM ver. 3.0 – 10.0.3
Advisory ID: usd-2019-0051
CVE Number: CVE-2019-19209
Affected Product: Dolibarr ERP/CRM
Affected Version: 3.0 – 10.0.3
Vulnerability Type: Reflected XSS, SQL injection
Security Risk: High
Vendor URL: https://www.dolibarr.org/
Vendor Status: Fixed (not verified)
Description
Multiple vulnerabilites due to insufficent filtering of the HTTP Header „Accept-Language“.
The unfiltered, but modified, variable „$langs->defaultlang“ gets used in multiple locations. This leads to XSS and SQL injection.
An incomplete list of files using this variable:
XSS
– /dolibarr/htdocs/admin/system/dolibarr.php (directly accessing $_SERVER[„HTTP_ACCEPT_LANGUAGE“])
– /dolibarr/htdocs/admin/mails_templates.php
– /dolibarr/htdocs/main.inc.php
SQL Injection
– /dolibarr/htdocs/admin/mails_templates.php
No exploit found to exfiltrate data due to the preprocessing of the value
Proof of Concept (PoC)
XSS: Submit a GET request to the given URL and intercept the request. Change the Accept-Language header as stated below and forward the request. A popup should occur displaying the cookie.
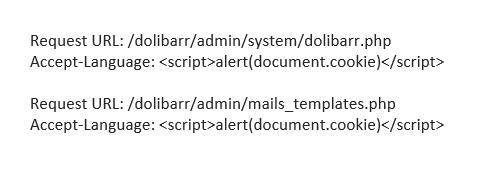
<html>SQL injection: Submit a GET request to the given URL and intercept the request. Change the Accept-Language header as stated below and forward the request. An error message should be displayed revealing the query.
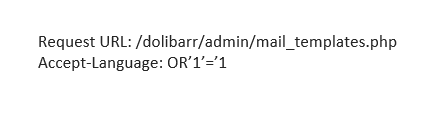
Fix
Validate the HTTP Header Accept-Language and ignore invalid values. Furthermore filter the value, according to its usage.
Timeline
- 2019-09-06 Vulnerability discovered by Daniel Hoffmann
- 2019-09-11 First contact with vendor
- 2019-10-30 Vendor released version 10.0.3 which fixes the vulnerability (not verified)
- 2020-02-05 Security advisory released
Credits
This security vulnerability was discovered by Daniel Hoffmann of usd AG.