usd-2023-0040 | Missing Authorization in SAP Fiori Travel and Expenses
Advisory ID: usd-2023-0040
Product: SAP Fiori - My Travel and Expenses
Affected Version: Component Version: EA-HR 608 0117, Support Package: SAPK-608B7INEAHR
Vulnerability Type: CWE-862: Missing Authorization
Security Risk: Medium CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:U/C:L/I:L/A:L
Vendor URL: https://www.sap.com
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE number: CVE-2024-32731
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2024-32731
Affected Component(s)
SAP Fiori - My Travel and Expenses https://fioriappslibrary.hana.ondemand.com/sap/fix/externalViewer/#/detail/Apps('F0584')/W10
Desciption
In business trip requests, there is the option to upload attachments. Through the OData backend, users have access to all attachments as long as they are aware of the respective attachment IDs.
If arbitrary file formats are accepted, for instance, HTML files with embedded JavaScript code can be uploaded. If a malicious user manages to persuade another person to click on the attachment link, it could lead to a reflected XSS, causing the JavaScript code within it to execute in the context of the invoking user.
Proof of Concept
Uploaded files can be retrieved with the following server request:
GET /sap/opu/odata/sap/ZTV_TRQ_SRV/Attachments('002049130000050945__FOL32000000000004EXT48000000004962______')/$value HTTP/2
Host: <sap-fiori-host>
User-Agent: python-requests/2.31.0
Accept-Encoding: gzip, deflate, br
Accept: */*
Authorization: Basic [REDACTED]
For example, if it's a PDF, the server will return the PDF:
HTTP/2 200 OK[...]%PDF-1.4[...]
As seen in line 6 of the request, Basic Auth can be utilized for user authentication. In this scenario, it is possible for another user, who is not the owner of the file, to access it as long as they know the ID. However, it's worth noting that these IDs are not easily enumerable.
Nevertheless, if the application accepts the upload of various file formats, it is possible to upload an HTML file with embedded JavaScript code and then send the link to any user. If the victim clicks on the link, it may result in the execution of the JavaScript code in the context of the victim.
If the session cookie is not adequately protected, this could additionally lead to the compromise of the active session.
In the following screenshot, a HTML file is being invoked. The file contains the following content:
<html> <body> <script>alert(document.cookie)</script> </body></html>
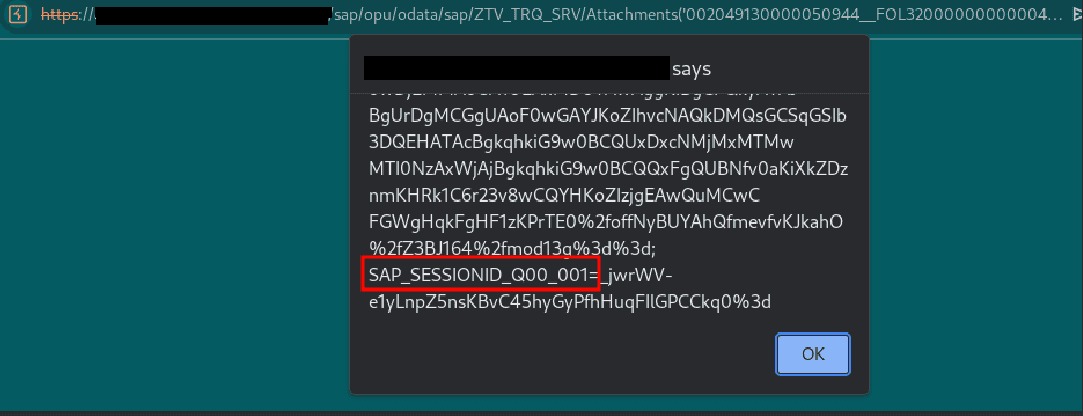
Fix
It is recommended to restrict access to sensitive functions or information by default.
Required access privileges should be granted explicitly by a global access control mechanism.
References
https://cwe.mitre.org/data/definitions/862.html
Timeline
- 2023-12-06: First contact request via vulnerability form.
- 2024-01-24: SAP confirms vulnerability and starts to fix it.
- 2024-05-14: SAP released the patch in SAP Note 3447467.
Credits
This security vulnerability was identified by Ole Wagner of usd AG.