usd-2019-0002 | feeling4design Super Forms – Drag & Drop Form Builder/1.0.0 – 4.4.8
Advisory ID: usd-2019-0002
CVE Number: N/A
Affected Product: Super Forms
Affected Version: 1.0.0 – 4.4.8
Vulnerability Type: Path Traversal
Security Risk: Critical
Vendor URL:
https://github.com/RensTillmann/super-forms
http://codecanyon.net/user/feeling4design
Vendor Status: Not fixed
Description
The attacker can upload files to arbitrary locations by manipulating the [userid] stored in the session cookie. This vulnerability when combined with the vulnerability „Arbitrary File Upload“ described in usd-2019-0003 can lead to Remote Code Execution.
Proof of Concept (PoC)
The upload of arbitrary file extension was tested on a customers instance of wordpress + super forms.
To reproduce:
1) Setup wordpress with super forms and create a form containing an upload form
2) Before submitting this form, set a cookie PHPSESSID to the path relative to the upload directory, e.g. PHPSESSID=../
As a consequence, we used the generation of the [userid] for the subfolder to upload the file to a different path. The source code in /uploads/php/UploadHandler.php:
@session_start();
return session_id();
}
The session_id() can be changed by the PHPSESSID cookie. We set it to value ../ which changes the upload path to: uploads/php.
File execution:
Usually, the uploaded files were copied to a subfolder with a random [userid] on the server: wpcontent/plugins/super-forms/uploads/php/files/[userid]/[filename]. In the folder php/files/ there is a .htaccess file that denies the execution of php files:
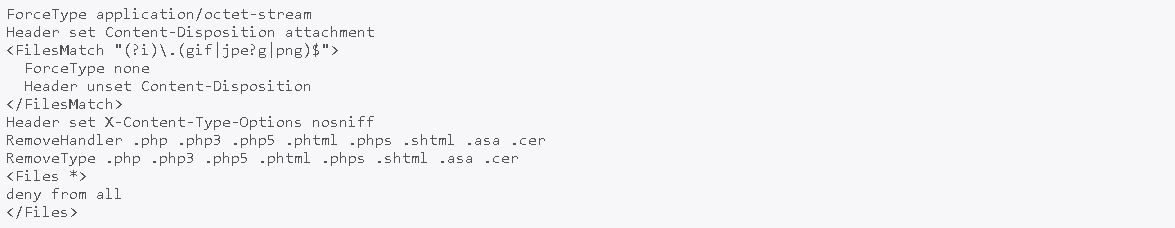
Since the directory uploads/php is not restricted in php code execution by the mentioned .htaccess file, a php reverse shell is possible.
Fix
Disclaimer
The suggested fix is just a temporary workaround and not a final fix that ensures the full security of this wordpress plugin. It is intended to support the developers to close this vulnerability.
The vulnerabilities we found are not yet fixed by the latest version of this plugin. One option is to turn it off.
Another option is to apply the following temporary fixes:
In /uploads/php/UploadHandler.php replace the function get_user_id() to return a value an attacker cannot tamper with.
Timeline
- 2019-01-25 First Contact request via contact form to: https://codecanyon.net/item/super-forms-drag-drop-form-builder/13979866/support
- 2019-02-05 Vendor releases version 4.5.3 with a supposed fix. We could still exploit the vulnerability. (related: Changelog on https://codecanyon.net/item/super-forms-drag-drop-form-builder/13979866)
- 2019-07-31 Security advisory released
Credits
This security vulnerabilities were found by Tim Kranz and Matthias Göhring of usd AG.