usd-2019-0057 | Userlike Chat
Advisory ID: usd-2019-0057
CVE Number: CVE-2019-19213
Affected Product: Userlike Chat
Vulnerability Type: Cross-Site Scripting
Security Risk: Critical
Vendor URL: https://userlike.com
Vendor Status: Fixed
Description
Userlike does not handle data received via websockets requests correctly, thus a malicious client may inject JavaScript that is run in the browser context of a chat operator.
Introduction
Companies that want to use userlike.com need to register first. In order to install the chat on their website, there is a JavaScript Widget that can be downloaded and embedded. Once the chat is setup correctly, users may start a chat session with chat operators. Therefore operators need to login at https://userlike.com/de/ and open the chat panel.
In this chat panel, chat operators may create screenshots of the customer’s browser using the „$screenshot“ command. In the following the screenshot is then uploaded from the client (customer) to the userlike server. The server responds with the URL where the uploaded image may be found. This URL is sent to the chat operator using a websocket and finally embedded in an <img>-tag. Because of insufficient filtering, the URL may contain special characters enabling an attacker to escape the source of this <img>-tag and insert her own markup and XSS payload.
Even though the interaction of the chat operator is required to perform this attack, this vulnerability is considered critical. Performing a social engineering attack an attacker may easily convince a chat operator to take a screenshot of the attacker’s browser.
Proof of Concept (PoC)
1. [Operator] type „$screenshot“
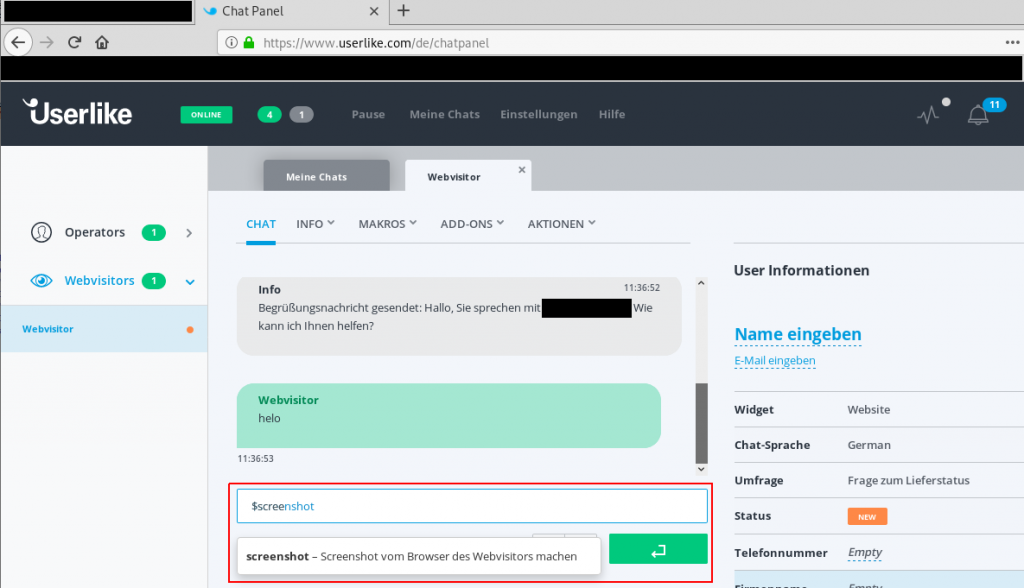
2. [Customer] start intercepting traffic (including websocket requests)
3. [Operator] send message
4. [Customer] forward websocket requests up to the message containing the screenshot URL:
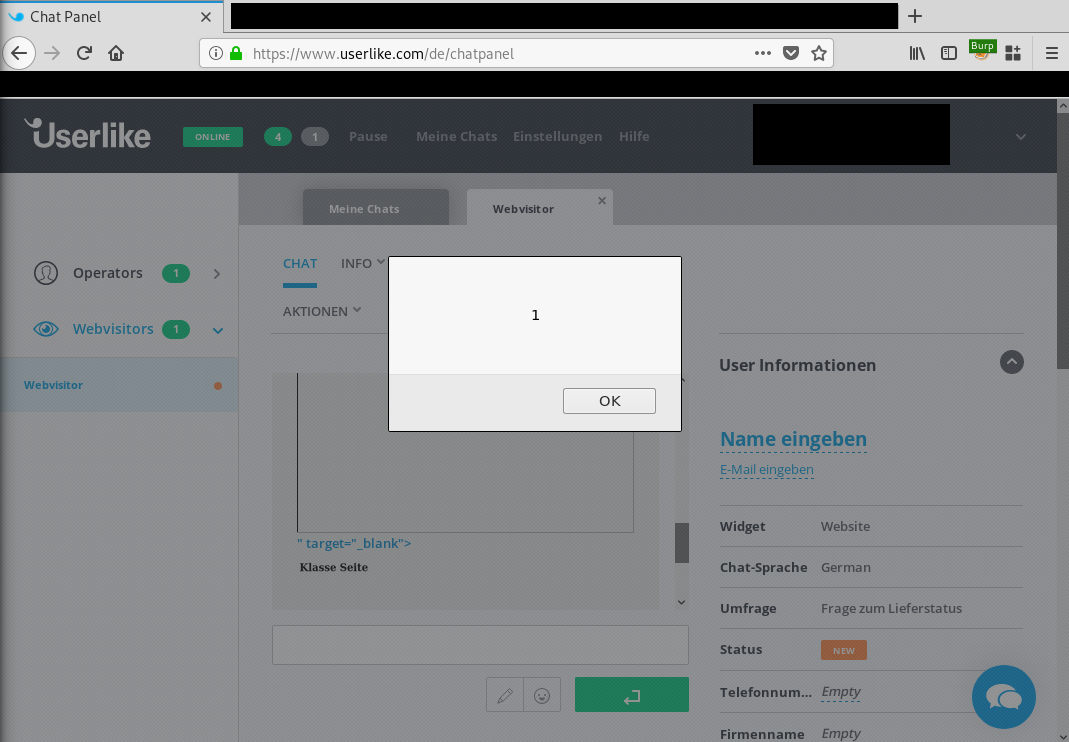
4.1. [Customer] extend the URL such that it contains the XSS payload and then forwa
5. The XSS Payload is run in the operator’s browser:
Fix
Treat websocket-requests that are sent by the client as regular user controlled data. Make sure to encode or filter user controlled content before embedding and replaying it.
Timeline
- 2019-09-18 This vulnerability was found by Konstantin Samuel during a pentest
- 2019-11-14 Vendor schedules update for this date
- 2019-11-25 Vendor fixed the issue
- 2020-04-29 Security advisory released
Credits
This security vulnerabilities were found by Konstantin Samuel of usd AG.