usd-2020-0105 | Themeco Cornerstone Editor
Advisory ID: usd-2020-0105
Affected Product: Themeco Cornerstone Editor
Affected Version: v7.2.3
Vulnerability Type: Stored Cross-Site Scripting (Stored XSS)
Security Risk: High
Vendor URL: https://theme.co/
Vendor Status: Not fixed
Description
The Themeco Cornerstone Editor is a WordPress plugin that offers a HTML WYSIWYG editor with a broad feature set.
Authenticated users may create and edit X Theme frontend articles. In doing so, moderators can embed different content elements, including Classic Text, Text and more.
The text content element suffers from a stored Cross-Site Scripting (XSS) vulnerability, injected JavaScript is executed if a victim enters the "Edit" view of a prepared article as well as published blog posts. As this functionality is available for relatively low-privileged moderators, a malicious user could target higher privileged backend users with this XSS vulnerability.
The described issue probably affects other content elements as well.
Proof of Concept (PoC)
XSS inside Editor:
1. Create a new article at https://vulnerablewebsite.com/x/#/content
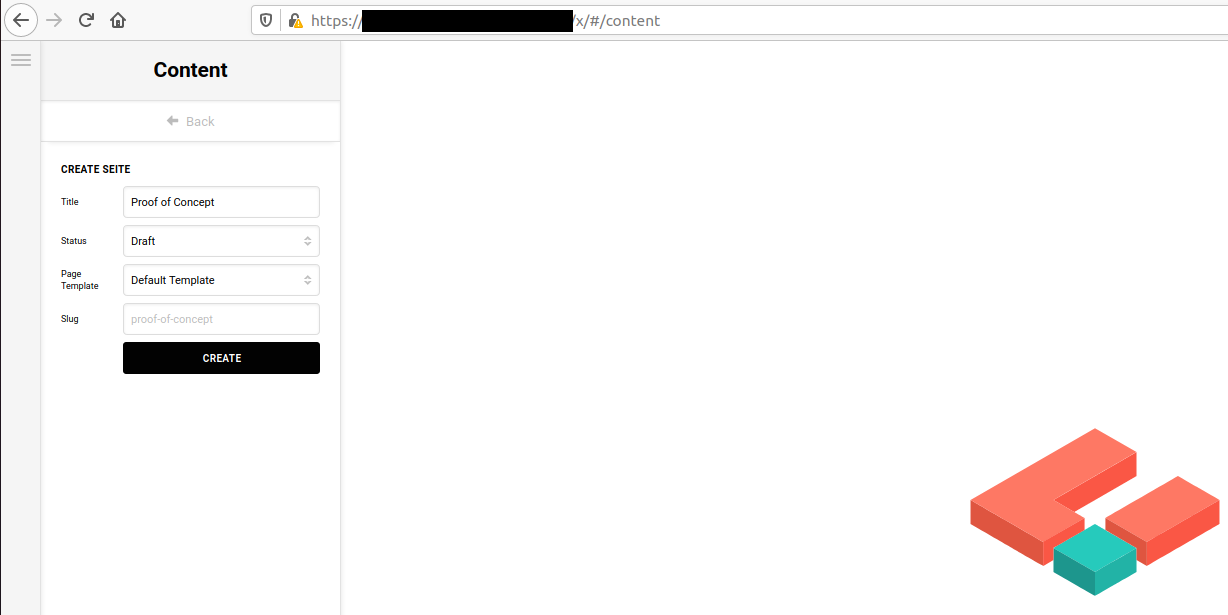
2. Create a Classic Text element
3. Choose "</>" to enter HTML and set the content to of the element to:
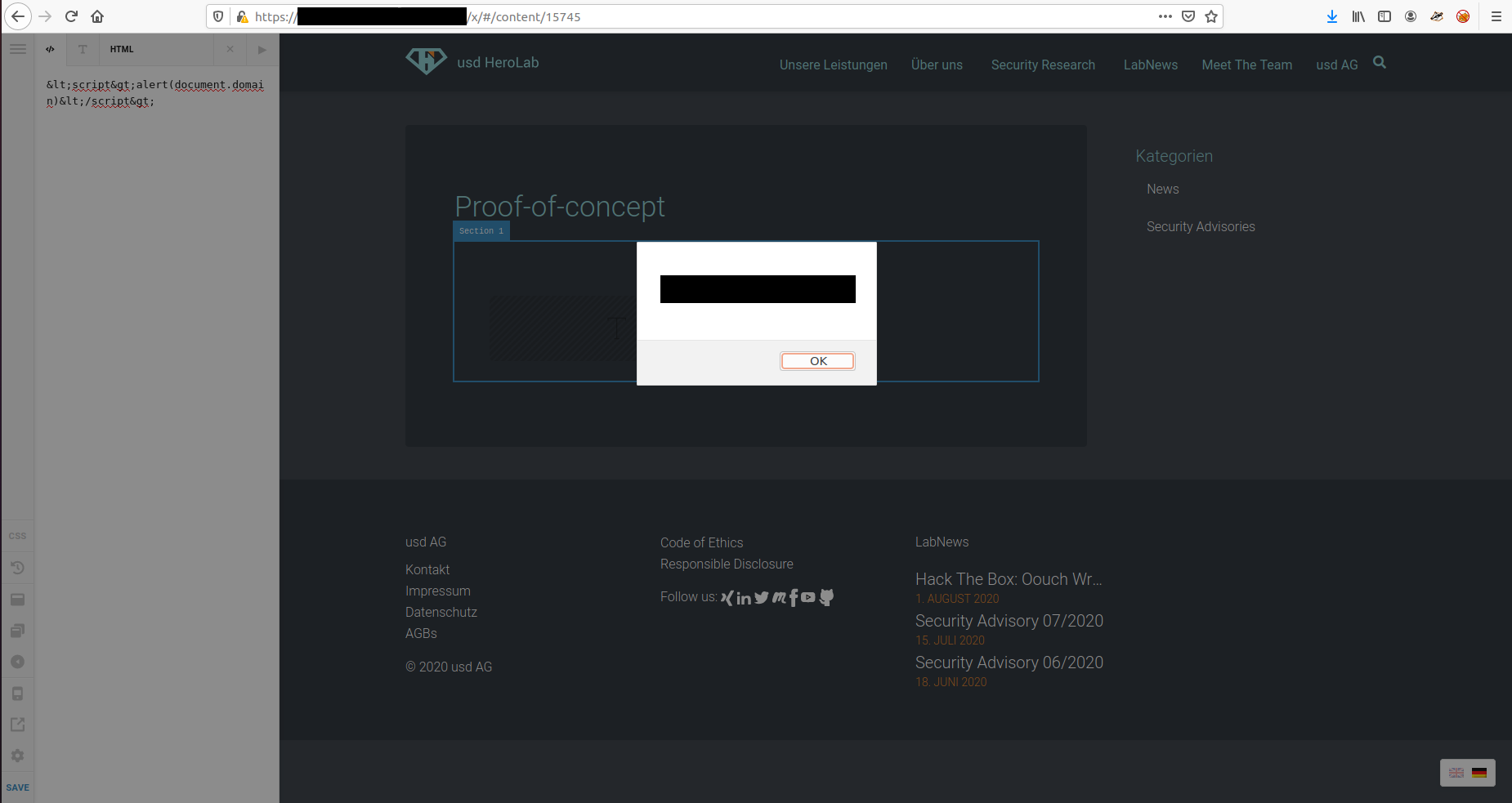
<script>alert(document.domain)</script>
4. Observe that the JavaScript is executed
XSS in published article:
1. Create a new article at https://vulnerablewebsite.com/x/#/content
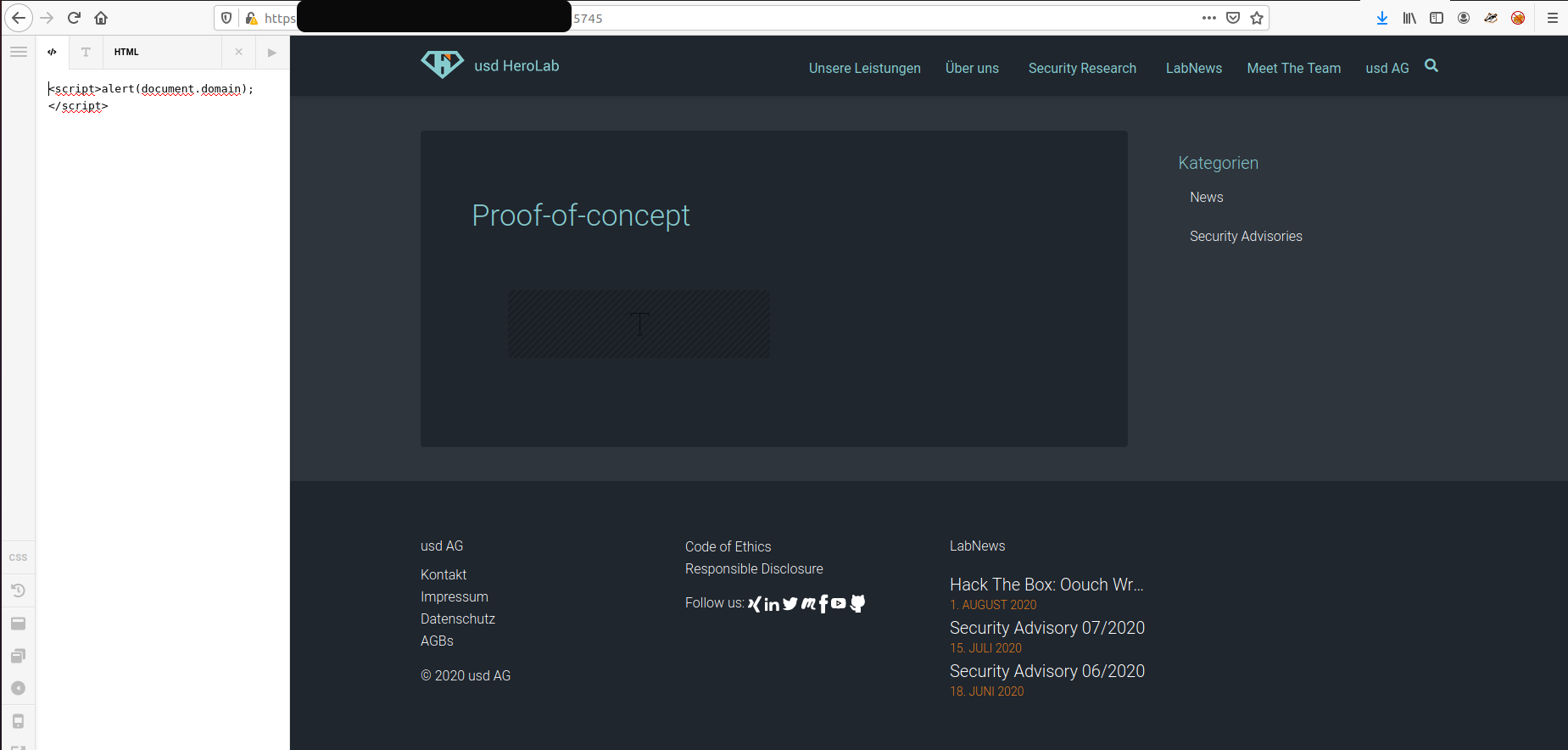
2. Create a Classic Text element
3. Choose "</>" to enter HTML and set the content to of the element to:
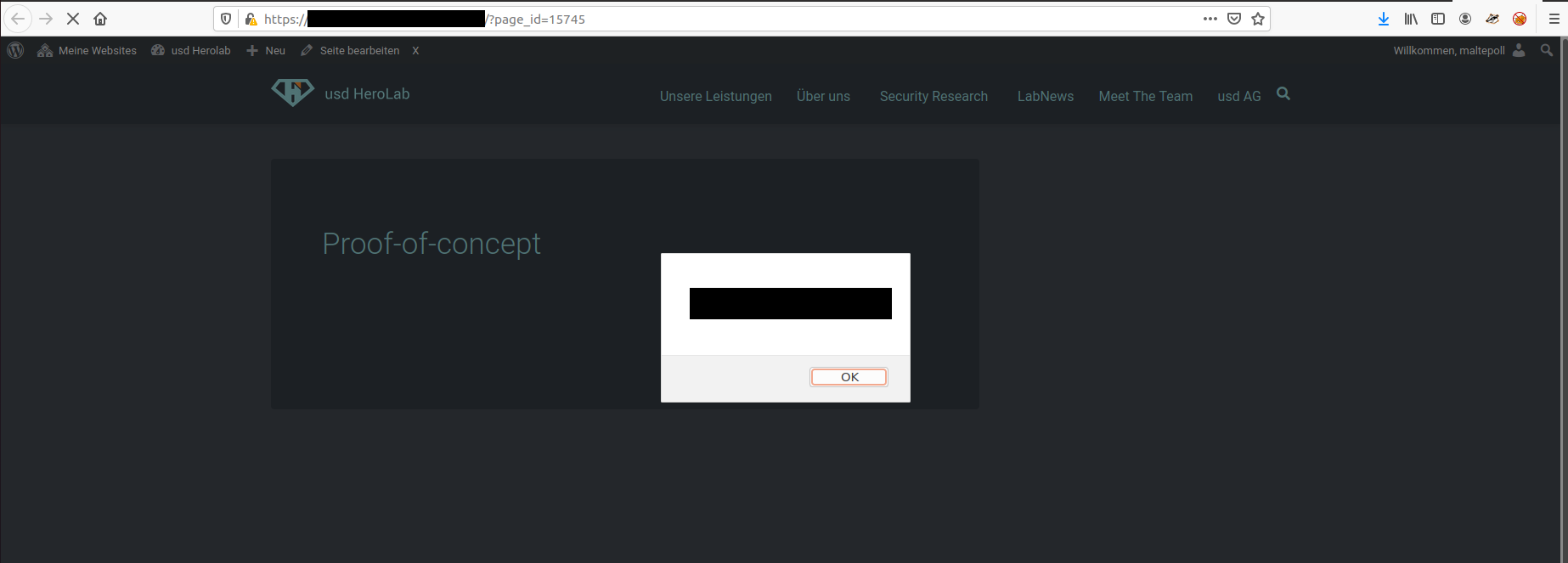
<script>alert(document.domain)</script>
4. Observe that the JavaScript is executed
Fix
References
Timeline
- 2020-08-28: Vulnerability identified by Lauritz Holtmann of usd AG.
- 2020-08-28: First contact attempt via https://theme.co/contact.
- 2020-08-28: Vendor asks for details, a secure communication channel is established.
- 2020-10-01: Vulnerability details transmitted to vendor.
- 2021-02-18: Follow up e-mail on triage/remediation status.
- 2021-02-24: Vulnerability details are transmitted to vendor, as Theme.co claims the details were not received.
- 2021-03-10: Vendor acknowledges that they received the vulnerability details.
- 2021-04-15: Follow up e-mail on triage/remediation status.
- 2021-05-06: Follow up e-mail on triage/remediation status.
- 2021-05-07: The vendor provides a statement on the submitted issues including details on future releases.
- 2021-07-14: Status update requested from vendor.
- 2021-09-21: Status update requested from vendor, release date set for end of September.
- 2021-09-30: Security Advisory released by usd AG.
Credits
This security vulnerability was found by Lauritz Holtmann of usd AG.