usd-2021-0005 | CheckPoint Identity Agent < R81.018.0000
Advisory ID: usd-2021-0005
CVE Number: CVE-2021-30356
Affected Product: CheckPoint Identity Agent
Affected Version: < R81.018.0000
Vulnerability Type: Symlink Vulnerability
Security Risk: High
Vendor URL: https://www.checkpoint.com
Vendor Status: Fixed
Description
The CheckPoint Identity Agent allows low privileged users to write files to protected locations of the file system.
Privileged file write vulnerabilities allow low privileged users to create or overwrite files in arbitrary locations of the file system. The impact of these attacks largely depends on the content that is written to the files. If the content is user controlled, privilege escalations are usually possible. Otherwise, the vulnerability can be used to perform Denial of Service attacks.
Proof of Concept (PoC)
The CheckPoint Identity Agent allows users to collect information for the technical support. This information is collected to a Windows Cabinet file and stored within a user defined location. During the write operation that creates the Cabinet file, the service uses the permissions of the SYSTEM account, which allows low privileged users to create the Cabinet file in arbitrary locations of the file system. By using a symbolic link, the file name is also fully user controlled and the write operation can also be redirected to already existing files.
In the following screenshot, a low privileged user account sets the log folder of the CheckPoint Identity Agent to a user controlled path on the file system. This is possible within the tray menu of the agent.
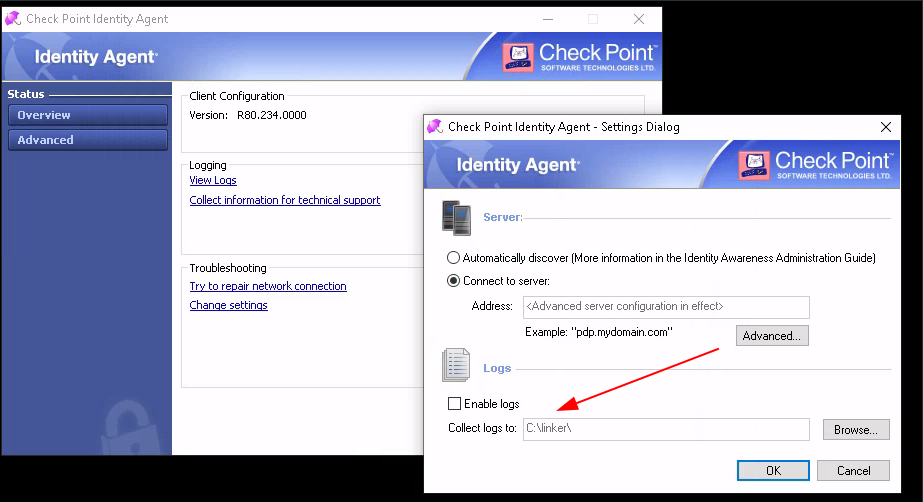
The Cabinet file that we will create soon has a naming scheme of CP_Identity_Agent_Logs_25-01-2021_17.07.11.cab. As the name contains the current time and the export takes a while, an reliable attack requires multiple symbolic links. For our demonstration, we use the following simple script to create these:
C:\ProgramData\CreateSymlink.exe -p C:\Linker\CP_Identity_Agent_Logs_31-01-2021_12.13.00.cab C:\Windows\win.ini
C:\ProgramData\CreateSymlink.exe -p C:\Linker\CP_Identity_Agent_Logs_31-01-2021_12.13.01.cab C:\Windows\win.ini
C:\ProgramData\CreateSymlink.exe -p C:\Linker\CP_Identity_Agent_Logs_31-01-2021_12.13.02.cab C:\Windows\win.ini
C:\ProgramData\CreateSymlink.exe -p C:\Linker\CP_Identity_Agent_Logs_31-01-2021_12.13.03.cab C:\Windows\win.ini
C:\ProgramData\CreateSymlink.exe -p C:\Linker\CP_Identity_Agent_Logs_31-01-2021_12.13.04.cab C:\Windows\win.ini
[...]
Within the script, we make obviously use of the symboliclink-testing-tools by James Forshaw.
After invoking the script, all possible file system locations for the to be generated Cabinet file point now to C:\Windows\win.ini, which is not writable for low privileged user accounts. Now we can request technical support information within the agents tray menu:
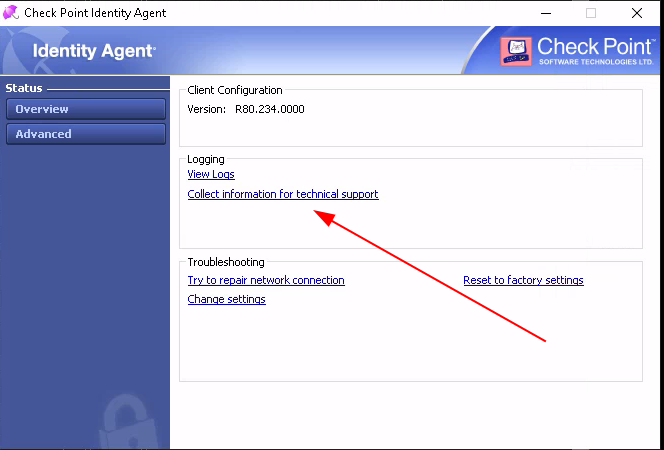
When the export finished, the C:\Windows\win.ini file should be overwritten with the contents of the Cabinet file. The following listing shows the original and the new content of the file:
; for 16-bit app support
[fonts]
[extensions]
[mci extensions]
[files]
[Mail]
MAPI=1
C:\› type C:\Windows\win.ini
MSCF [...]
Fix
Whenever high privileged services write data into user controlled parts of the file system, they should make sure to impersonate the corresponding user during the operation.
Additionally, protection mechanisms can be implemented to avoid following symlinks during write operations.
Timeline
- 2021-02-12 Vulnerability discovered by Tobias Neitzel
- 2021-02-13 Initial contact with vendor
- 2021-03-02 Vendor provides patch for retest
- 2021-03-18 Patch published by vendor in release R81.018.0000
- 2021-03-31 Security Advisory released
Credits
This security vulnerability was discovered by Tobias Neitzel of usd AG.