usd-2021-0015 | Password Manager Pro
Advisory ID: usd-2021-0015
CVE Number: CVE-2021-33617
Affected Product: Password Manager Pro
Affected Version: < Version 11.2 Build 11200 (Major)
Vulnerability Type: User Enumeration (CWE-203: Observable Discrepancy)
Security Risk: Low
Vendor URL: https://www.manageengine.com/products/passwordmanagerpro/
Vendor Status: Fixed
Description
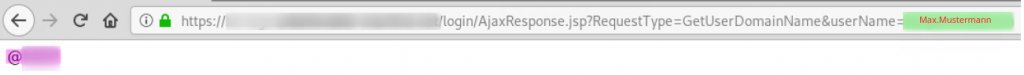
The ManageEngine Password Manager Pro web application allows the determination of valid logon names. This can be achieved by passing either an existing or non-existing user name to the application and view its corresponding response.
User Enumeration vulnerabilities occur if observable discrepancies of an application’s behavior allow to determine whether an user account is existent within an application. Such vulnerabilities can be often exploited to generate a list of valid logon names, potentially acting as foothold for further attacks.
The Password Manager Pro exposes an endpoint that enables an unauthenticated malicious actor to determine whether an userName is existent within the application.
Proof of Concept (PoC)
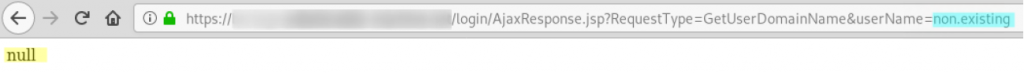
The Password Manager Pro exposes an endpoint that responds with different contents if a userName parameter at https://example.com/login/AjaxResponse.jsp?RequestType=GetUserDomainName&userName=[VALUE] holds an existing user name or not.
1. Non-existent user: https://example.com/login/AjaxResponse.jsp?RequestType=GetUserDomainName&userName=non.existent
Fix
It is recommended to use generic error messages that do not allow to draw conclusions about logon names.
References
- https://cwe.mitre.org/data/definitions/203.html
- https://www.gnucitizen.org/blog/username-enumeration-vulnerabilities/
Timeline
- 2021-04-01: This vulnerability was identified by Marcus Nilsson.
- 2021-04-15: Advisory submitted to vendor via e-mail.
- 2021-05-28: CVE-2021-33617 is assigned
- 2021-07-07: Security fix is released with Version 11.2 Build 11200: „A user enumeration issue has been fixed“.
- 2021-07-30: Security advisory released by usd AG.
Credits
This security vulnerability was found by Marcus Nilsson of usd AG.