usd-2023-0033 | Cross-Site Scripting in hugocms
Advisory ID: usd-2023-0033
Product: hugocms
Affected Version: (latest as of 25.09.2023; commit 77443d6)
Vulnerability Type: CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
Security Risk: HIGH
Vendor URL: https://hugoeditor.com/
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
Advisory Status: Published
CVE Number: CVE-2023-49324
First Published: 2024-07-18
Last Update: 2024-07-18
Desciption
The application hugocms, developed by Inter-Data, provides a frontend for the static site generator hugo to manage posts and other aspects of the site. The application does not provide any access-control mechanism and recommends to restrict access via a web server's basic auth capabilities.
Attackers that are able to create files can trigger an XSS vulnerability by creating a file that contains an XSS payload in its filename. Since the application supports versioning via git in its paid version, the vulnerability might be exploitable by an attacker with access to the remote git repository.
Proof of Concept
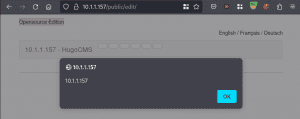
Use the "New file" button to create a file named:
The XSS is triggered in the file listing, as shown in the following screenshot.
Timeline
- 2023-09-25: Vulnerability identified by Florian Dewald.
- 2023-10-02: Sent first contact request.
- 2023-10-16: Sent reminder email mentioning disclosure deadline.
- 2023-10-25: Sent another reminder stressing that vulnerabilities will be publicly disclosed.
- 2023-11-13: Sent another reminder stressing our deadline and that vulnerabilities will be publicly disclosed if we receive no answer.
- 2023-11-22: Reached vendor via phone, sent vulnerability information.
- 2023-12-04: Sent status update request to info@inter-data.de
- 2023-12-06: Inter-Data reports that a fix is being worked on.
- 2024-01-03: According to Inter-Data a fix is in the works and should be finished soon.
- 2024-01-24: Reached out to Inter-Data for another status update.
- 2024-01-26: Inter-Data reports that the vulnerability is fixed.
- 2024-07-18: This advisory is published.
Credits
This security vulnerability was identified by Florian Dewald of usd AG.