usd-2023-0038 | Broken Access Control in SAP Fiori Sample Shop
Advisory ID: usd-2023-0038
Product: SAP Fiori Sample Shop
Affected Version: Docker Image sapse/abap-platform-trial:1909
Vulnerability Type: CWE-284 (Improper Access Control)
Security Risk: MEDIUM - CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:L
Vendor URL: https://www.sap.com/
Vendor Status: Fixed
CVE number: Not assigned
Last Update: 2024-03-18
Affected Component
SAP Trial docker container with pre-configured SAP Fiori Sample Shop
Description
SAP Fiori is the SAP webfrontend which can host various applications from an application store or custom applications, which can be built with SAP ABAP.
When using the application, backend requests are sent to an OData API.
If API permissions differ from the configuration applied to the frontend component, attackers may execute backend functionality without authorization granted in the frontend.
Proof of Concept
The preconfigured shop contains several pieces of sample data. For our PoC we pick a random product from the shop. In the product overview in the upper right corner, we can write a review, as can be seen in the following screenshot: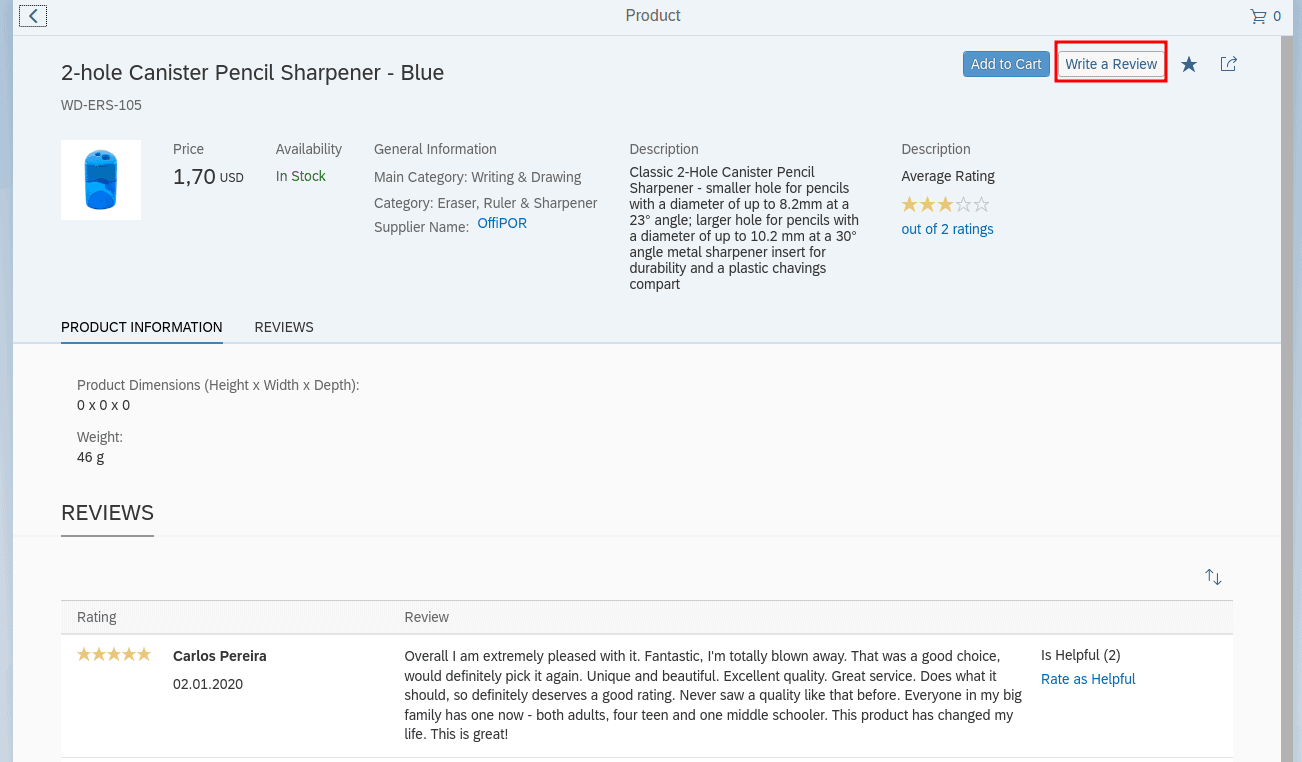
At the bottom all reviews are displayed. As can be seen in the following screenshot, only our own reviews have an associated delete button:
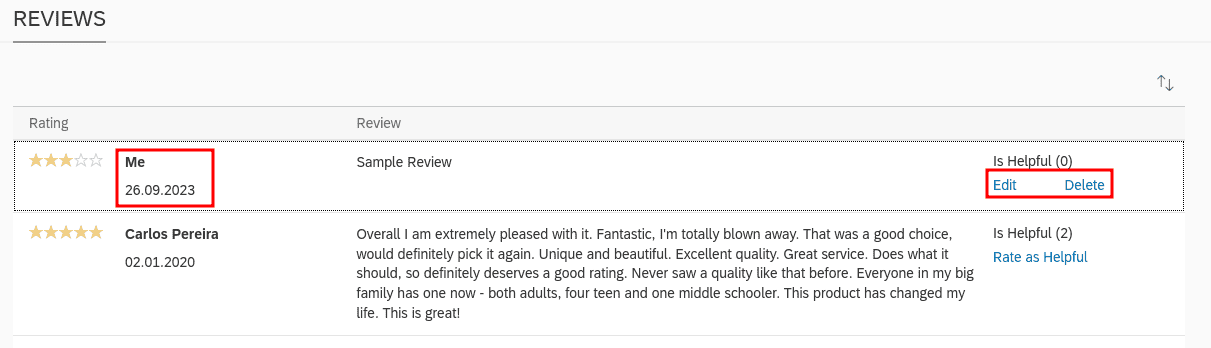
The following request will be sent to the OData backend API by clicking the frontend's delete button on our own review:
DELETE /sap/opu/odata/sap/SEPMRA_SHOP/Reviews(guid'0242ac11-0002-1eee-9792-6efba254d650')?sap-client=001 HTTP/1.1sap-contextid-accept: headerAccept: application/jsonAccept-Language: enDataServiceVersion: 2.0MaxDataServiceVersion: 2.0x-csrf-token: nK8sL23VXwnBlSOaso7TXg==
Intercepting this requst allows us to resend it with other guids placed in the request. Thereby we can delete other user's reviews.
The necessary guids can be enumerated by sending the following request:
GET /sap/opu/odata/sap/SEPMRA_SHOP/Reviews?sap-client=001 HTTP/1.1sap-contextid-accept: headerAccept: application/jsonAccept-Language: enDataServiceVersion: 2.0MaxDataServiceVersion: 2.0
Fix
It is recommended to restrict access to sensitive functions or information by default.
Required access privileges should be granted explicitly by a global access control mechanism, which should be consistent regardless whether the backend is accessed via the application's frontend or API.
References
https://cwe.mitre.org/data/definitions/284.html
https://owasp.org/Top10/A01_2021-Broken_Access_Control/
Timeline
- 2023-10-04: Vulnerability identified by Ole Wagner of usd AG.
- 2023-10-05: First contact request via SAP's vulnerability disclosure form.
- 2023-10-25: Received an update by SAP that the incident is in internal review.
- 2023-11-14: The vulnerability was confirmed by SAP's security team and the vulnerable sample application was removed from the trial version.
- 2024-03-26: This advisory is released by usd AG.
Credits
This security vulnerability was identified by Ole Wagner of usd AG.