usd-2023-0048 | Gambio 4.9.2.0 - Server-Side Template Injection
Product: Gambio
Affected Version: 4.9.2.0
Vulnerability Type: CWE-1336 - Improper Neutralization of Special Elements Used in a Template Engine
Security Risk: High
Vendor URL: https://www.gambio.de/
Vendor Status: Not fixed
CVE number: CVE-2024-23761
Description
Gambio is software designed for running online shops.
It provides various features and tools to help businesses manage their inventory, process orders, and handle customer interactions.
According to their homepage, the software is used by more than 25.000 shops.
The email templates are using the Smarty template engine, which can be used to execute arbitrary commands on the underlying system.
Note: Upon discovery, our team immediately initiated the responsible disclosure process by contacting the vendor behind Gambio.
Unfortunately, despite multiple attempts, our attempts to engage the vendor in resolving this issue have been met with silence.
The vulnerability is still unfixed.
Proof of Concept
The email templates are using the Smarty template engine.
Its possible to receive code execution using a SSTI vulnerability.
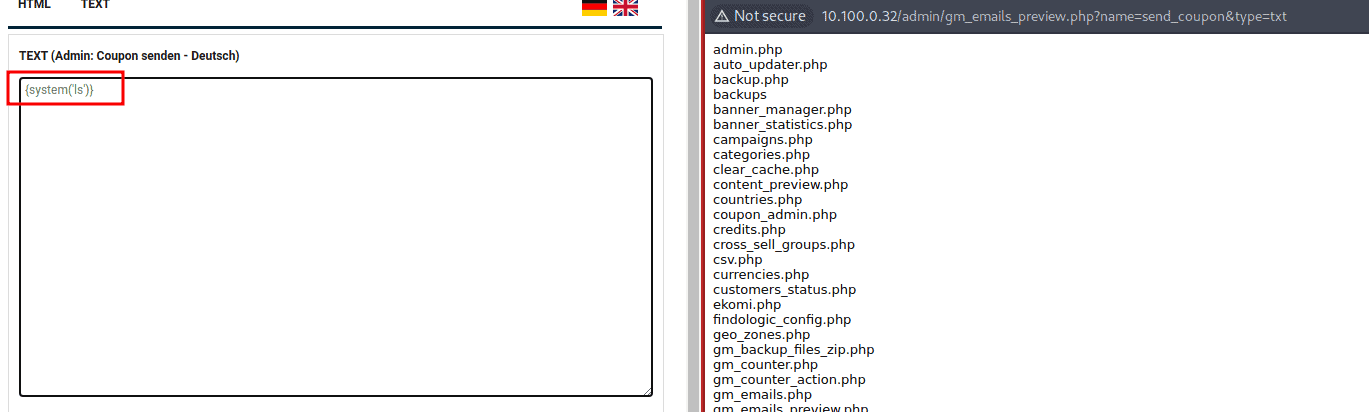
Fix
It is recommended to define templates statically wherever possible.
If templates are generated dynamically based on user input, it must be ensured that attackers cannot inject any template commands or meta characters.
For this purpose, user input should be masked before it is inserted into the template.
References
Timeline
- 2023-12-08: First contact request via email.
- 2023-12-21: Second contact request via email.
- 2024-01-17: This advisory is published.
Credits
This security vulnerability was identified by Christian Poeschl and Lukas Schraven of usd AG.