usd-2020-0024 (CVE-2020-14171) | Bitbucket Server 7.2.3
Advisory ID: usd-2020-0024
CVE Number: CVE-2020-14171
Affected Product: Bitbucket Server
Affected Version: 4.9.0 <= version < 7.2.4
Vulnerability Type: Unencrypted Service
Security Risk: Medium
Vendor URL: https://www.atlassian.com/de/software/bitbucket
Vendor Status: Fixed
Description
Bitbucket allows the import of external repositories. A username and personal access token must be provided when importing repositories from GitHub Enterprise. These credentials get base64 encoded and sent in an import request with Basic Auth.
It is possible to send such import requests using the unencrypted HTTP protocol. In this case, base64 offers no protection to the credentials and an attacker who performs a man-in-the-middle attack can capture the Basic Auth string and convert it into plain text.
Proof of Concept (PoC)
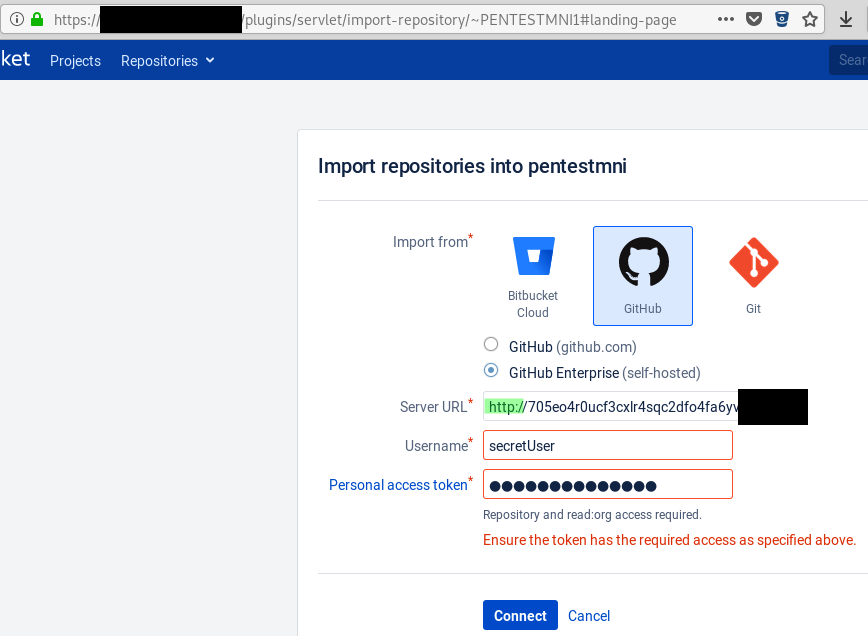
1. Go to the repository import page („/plugins/servlet/import-repository/~USERNAME#landing-page“) and enter a URL starting with „http://“ into the „Server URL“ field and enter your credentials into the „Username“ and „Personal access token“ fields:
2. The MitM attacker can see the unencrypted HTTP request sent by the Atlassian HttpClient:
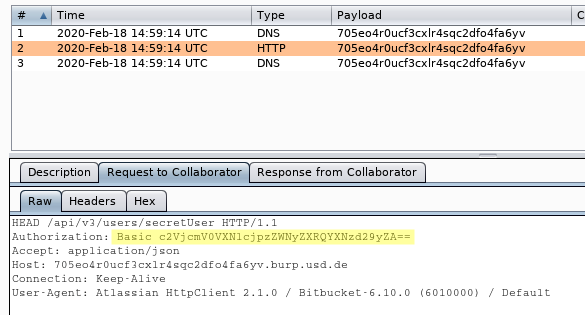
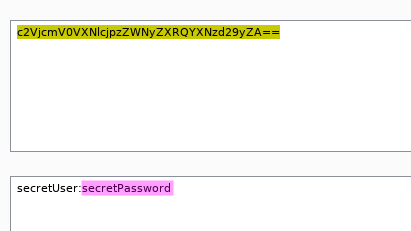
Fix
Consider to only allow encrypted (HTTPS) connections for the Github Enterprise importing feature. If this is not possible, it might still be an added benefit to warn the end-user about the possible risks before sending the credentials unencrypted.
Timeline
- 2020-03-12 First contact request via security@atlassian.com
- 2020-05-20 Contact request via Support forum
- 2020-07-08 Vendor publishes advisory: https://jira.atlassian.com/browse/BSERV-12434
- 2020-07-15 Security advisory released
Credits
This security vulnerability was found by Marcus Nilsson of usd AG.