usd-2022-0032 | Seafile 9.0.6 - Cross-Site Scripting
Advisory ID: usd-2022-0032
Product: Seafile
Affected Version: 9.0.6
Vulnerability Type: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') (CWE-79)
Security Risk: Medium
Vendor URL: https://seafile.com
Vendor Status: fixed
CVE number: requested
Description
The Seafile application allows to set up a self-hosted cloud storage system. It supports common functions such as synchronization of files between server and client, as well as group sharing.
In addition to the basic functions, Seafile also provides it's users with a wiki and a discussion feature. The markdown editor, provided by the application, does not properly filter javscript URIs from the `href` attribute, which results in stored XSS.
Proof of Concept
The markdown editor allows an attacker to inject a javascript payload in the *href* attribute of the *a* tag.
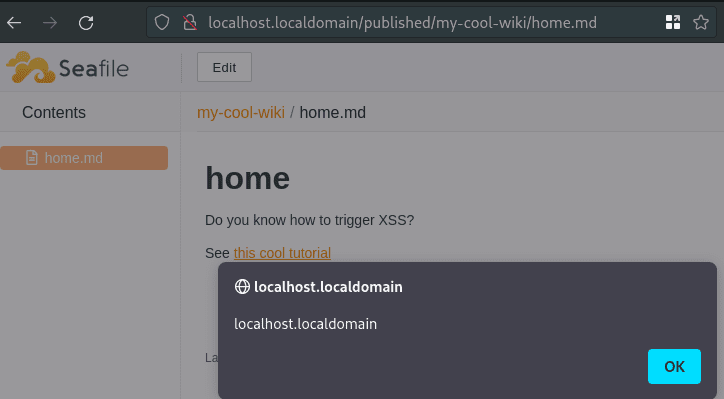
The payload is executed if a user visits and clicks on the link on the wiki page (or the file somewhere else).
Fix
It is recommended to treat all input on the website as potentially dangerous.
Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
The majority of programming languages support standard procedures for encoding meta characters.
References
- https://owasp.org/www-community/attacks/xss/
- https://manual.seafile.com/changelog/server-changelog/#908-2022-09-07
Timeline
- 2022-07-15: First contact request via info@seafile.com
- 2022-08-02: Second contact request via info@seafile.com
- 2022-08-11: Third contact request via info@seafile.com and seafile@datamate.org
- 2022-09-02: Vendor reports vulnerability as fixed (usd-2022-0032). Second advisory still in triage(usd-2022-0033)
- 2022-10-31: Both advisories fixed in new release 9.0.7
- 2023-02-14: The advisory is published
Credits
This security vulnerability was found by Christian Pöschl of usd AG.