usd-2024-0004 | Stored XSS in SAP Business Connector
Advisory ID: usd-2024-0004
Product: SAP Business Connector
Affected Version: 4.8.1 SR4 & CF2
Vulnerability Type: Improper Neutralization of Input During Web Page Generation (CWE-79 'Stored Cross-site Scripting')
Security Risk: Medium CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:N
Vendor URL: https://support.sap.com/en/product/connectors/bc.html
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed
CVE number: CVE-2024-30215
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2024-30215
Description
SAP Business Connector is an application developed by SAP SE, a German software corporation specializing in enterprise software solutions.
SAP Business Connector is an integration tool that allows businesses to connect various systems and applications, both within and outside the organization.
It enables seamless data exchange and interoperability between different systems, enabling businesses to automate processes, streamline operations, and improve productivity.
The application provides a platform for integrating diverse systems, such as ERP (Enterprise Resource Planning) systems, databases, web services, and legacy systems.
It supports a wide range of communication protocols, including HTTP, FTP, SOAP, and XML.
Version 4.8.1 with Patch SR4 and CF2 was found to be vulnerable to a stored XSS vulnerability in the "User-Agent field" of the "Outbound HTTP Settings".
Proof of Concept
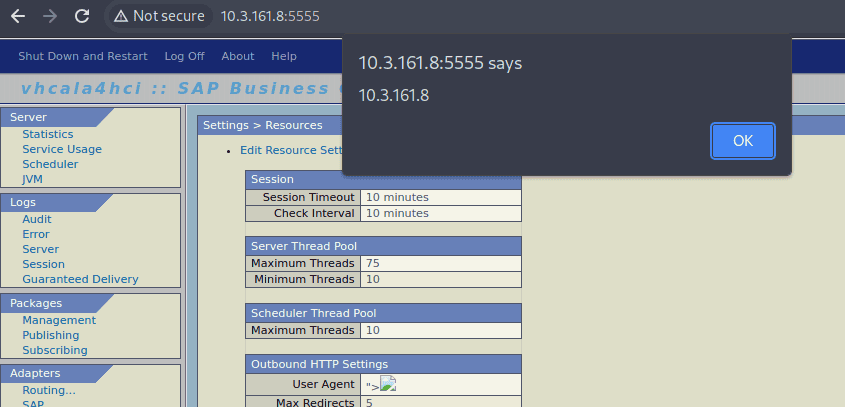
Navigate to "Settings" > "Resources" and hit "Edit Resource Settings".
Enter the payload "><img src=/X onerror=alert(document.domain)> into the "User-Agent" field of the "Outbound HTTP Settings".
The payload is stored and reflected whenever a user visits the Resource Settings page:
Fix
It is recommended to treat all input on the website as potentially dangerous.
Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
The majority of programming languages support standard procedures for encoding meta characters.
References
https://owasp.org/www-community/attacks/xss/
Timeline
- 2023-12-15: Vulnerability identified by Ole Wagner and Christian Poeschl.
- 2024-01-08: Initial contact request via SAP's Vulnerability Disclosure Form.
- 2024-02-05: SAP confirmed that the finding is a valid vulnerability.
- 2024-03-26: Received status update stating that fixes for confirmed vulnerabilities are currently in development/already released. Further information will be provided by SAP.
- 2024-04-09: Patch released as SAP Note 3421453.
Credits
This security vulnerability was found by Christian Poeschl and Ole Wagner of usd AG.