usd-2024-0007 | CSV Injection in Jira Cloud
Advisory ID: usd-2024-0007
Product: Jira Cloud
Affected Version: v1001.0.0-SNAPSHOT#100247 (and prior versions)
Vulnerability Type: Improper Neutralization of Formula Elements in a CSV File (CWE 1236)
Security Risk: HIGH
(CVSS 3.1: 8.0 - AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:H) (CVSS 4.0: 8.5 - AV:N/AC:L/AT:N/PR:L/UI:A/VC:H/VI:H/VA:H/SC:N/SI:N/SA:N)
Vendor URL: https://www.atlassian.com/
Vendor acknowledged vulnerability: Yes
Vendor Status: Closed as Finding was deemed 'Informational'
CVE Number: Not Assigned
Desciption
Jira Cloud by Atlassian is a web-based tool for bug and issue tracking and agile project management. According to the vendor's website, over 100,000 customers worldwide use Jira.
Jira Cloud is affected by a CSV injection vulnerability, potentially leading to the execution of arbitrary code via a crafted Excel file. A low-privileged remote attacker can create Jira issues containing the malicious payload that will be included in the exported CSV file.
Proof of Concept
Low-privileged users can create Jira issues containing spreadsheet formulas in the summary field that becomes the title of the issue:
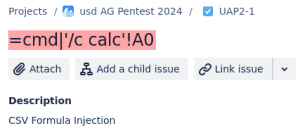
Jira issues can be exported in various formats, including CSV. The excerpt of the exported CSV file below shows that the injected formula =cmd|'/c calc'!A0 is not properly sanitized:
## Summary,Issue key,Issue id,Issue Type,Status,Project key,Project name,[...]
cmd|'/c calc'!A0,UAP2-1,44279,Task,To Do,UAP2,usd AG Pentest 2024,[...]
Opening the file in Microsoft Excel leads to the execution of the formula that will invoke the calculator application as a proof of concept, if Excel is configured to allow data connections or if the user confirms the corresponding warning message: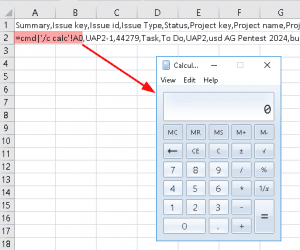
Fix
Where possible, the set of allowed characters for user input should be restricted using an allowlist.
Additionally, in the generation of spreadsheets, such CSV files, the following sanitization rules should be applied:
- every cell starting with an equal (=), plus (+), minus (-) or at-sign (@) should be prepended by a single quote (') and embedded in double quotes (")
- every cell containing a comma (,) or semicolon (;) should be prepended by a single quote (') and embedded in double quotes (")
- every double quote (") in a cell's content should be escaped by another double quote (")
References
Timeline
- 2024-03-18: Vulnerability disclosed via security@atlassian.com.
- 2024-03-20: Re-submission of the Finding via https://www.bugcrowd.com/.
- 2024-04-22: Report closed and classified informational.
Credits
This security vulnerability was identified by Dominique Dittert and Markus Arnold of usd AG.