usd-2019-0001 | Adobe Experience Manager (AEM)/6.3.2.2
Advisory ID: usd-2019-0001
CVE Number: N/A
Affected Product: Experience Manager
Affected Version: 6.3.2.2
Vulnerability Type: Code Injection
Security Risk: High
Vendor URL: https://www.adobe.com/
Vendor Status: Won’t fix
Description
The attacker can create a site with a malicious title, which contains an Excel formula. When the list of sites is exported by another user and opened in Microsoft Excel, the formula is evaluated. In the PoC, this is used to launch the Windows calculator.
Proof of Concept (PoC)
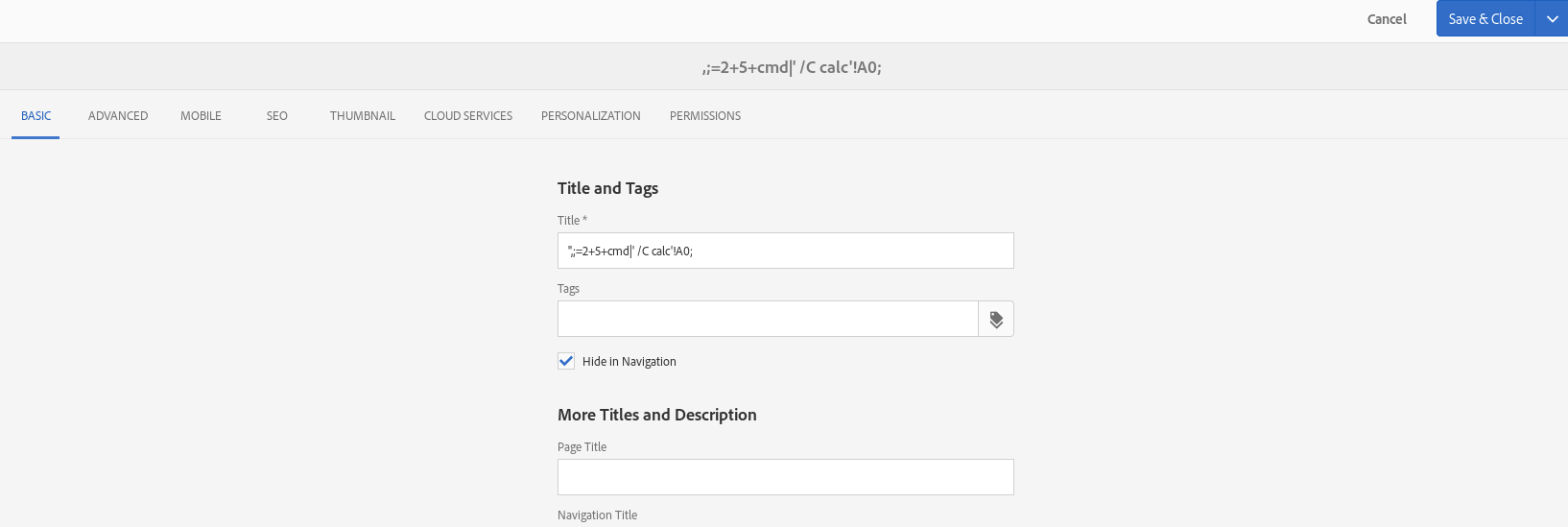
1) A site is created with the payload as title.
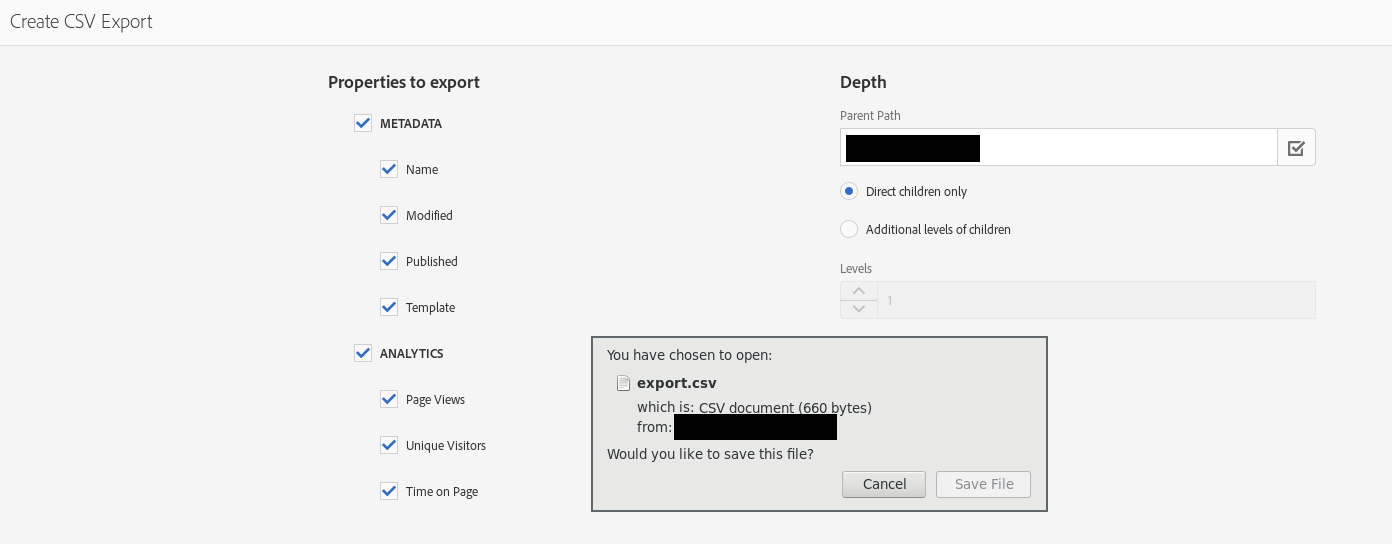
2) Then the path with the page is getting exported as CSV.
3) The title will be written into the CSV as it is, therefore making the injection possible.
Payload: „,;=2+5+cmd|‘ /C calc‘!A0;
This will result with the following row in the csv:
„‚“,;=2+5+cmd|‘ /C calc‘!A0;“,“/content/rsb/de/sureroute1″,“sureroute1″,[…] The ; will be interpreted as new column and therefore place the payload in an own column. This will lead to the execution of calc.exe.
Fix
Escape special characters in CSV / prevent escape from „“
Timeline
- 2019-01-16 Advisory sent to PSIRT@adobe.com
- 2019-02-14 Adobe PSIRT respond they won’t fix it.
- 2019-07-31 Security advisory released
Credits
This security vulnerabilities were found by Markus Schader of usd AG.