usd-2019-0058 | Userlike Chat
Advisory ID: usd-2019-0058
CVE Number: CVE-2019-19214
Affected Product: Userlike Chat
Vulnerability Type: Insufficient Filtering
Security Risk: Low
Vendor URL: https://userlike.com
Vendor Status: Fixed (not verified)
Description
Userlike does not handle data received via websockets requests correctly, thus a malicious client may inject content (including links) that is embedded in the operator’s chat view.
Introduction
Userlike’s chat software contains an insufficient filtering vulnerability, enabling Customers to send information to chat operators, that may appear to be service messages from the chat system. These spoofed messaged may contain links that are rendered correctly.
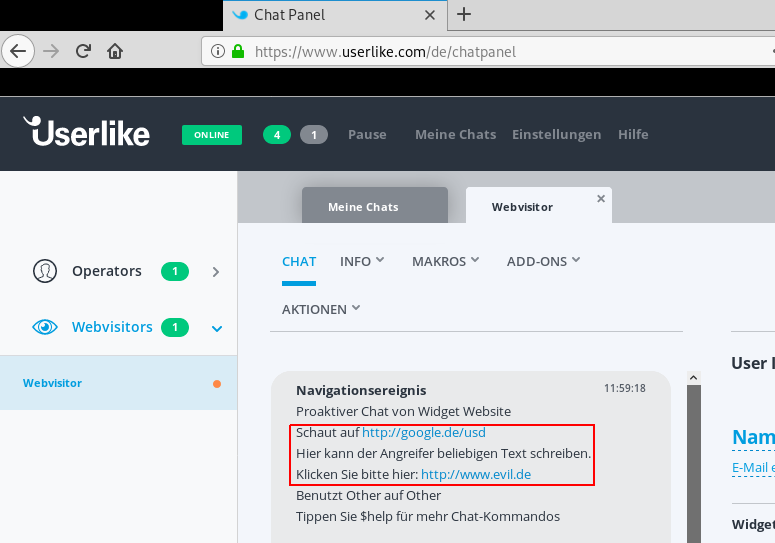
Proof of Concept (PoC)
1. [Customer] Start a chat session at the companie’s website
2. [Customer] Intercept traffic including websocket-requests but forward it until the following websocket-request should be sent:
2.1 [Customer] Edit the request’s „url“ parameter and forward the request:
Hier kann der Angreifer beliebigen Text schreiben.
Klicken Sie bitte hier: http://www.evil.de","page_impressions":3}},"context":4}]
3. [Operator] In the operator’s chat view the service message is rendered, including the spoofed content:
Hier" target="_blank">http://google.de/usd
Hier</a> kann der Angreifer beliebigen Text schreiben.
Klicken Sie bitte hier: <a class="Link" href="http://www.evil.de" target="_blank">http://www.evil.de</a></span>
Fix
Treat websocket-requests that are sent by the client as regular user controlled data. Make sure to encode or filter user controlled content before embedding and replaying it.
Timeline
- 2019-09-18 This vulnerability was found by Konstantin Samuel during a pentest
- 2019-11-14 Vendor schedules update for this date
- 2020-04-29 Security advisory released
Credits
This security vulnerabilities were found by Konstantin Samuel of usd AG.