usd-2020-0023 (CVE-2020-14170) | Bitbucket Server 7.3
Advisory ID: usd-2020-0023
CVE Number: CVE-2020-14170
Affected Product: Bitbucket Server
Affected Version: 5.4.0 <= version < 7.3.1
Vulnerability Type: Server Side Request Forgery
Security Risk: Medium
Vendor URL: https://www.atlassian.com/de/software/bitbucket
Vendor Status: Fixed
Description
A server side request forgery (SSRF) vulnerability was discovered in the „Webhooks“ section if the repository settings page. An authenticated attacker can set the URL field to internal IP addresses and retrieve data using the „Test connection“ feature.
Proof of Concept (PoC)
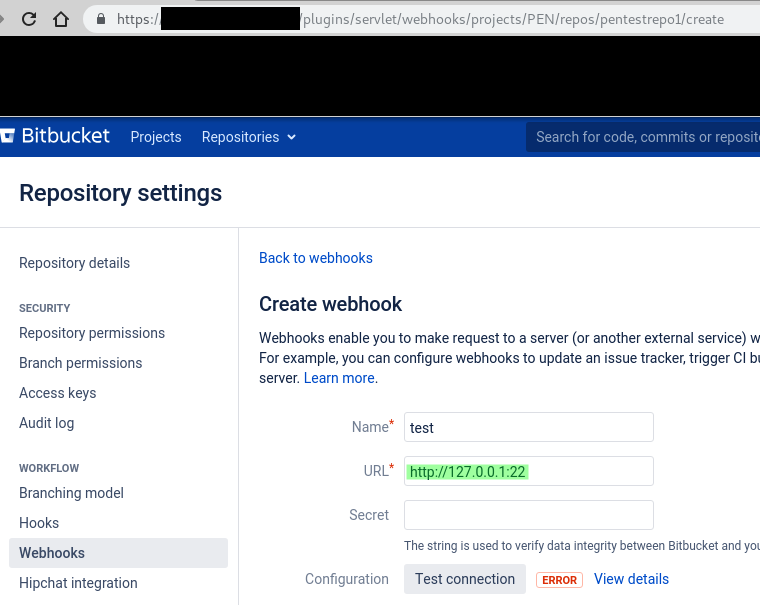
1. A new webhook is created under „Repositoy settings -> Webhooks“ with a URL pointing to an internal IP / port combination. URL of the page is /plugins/servlet/webhooks/projects/PROJECT_NAME/repos/REPO_NAME/create.In our example we use a URL value of „http://127.0.0.1:22“ to connect to the local SSH daemon:
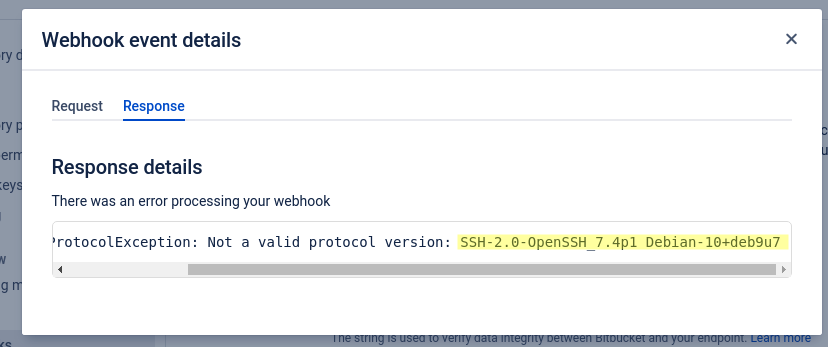
2. The attacker uses the „Test Connection“ feature. There will be a link titled „View details“. Clicking it reveals the SSH version banner:
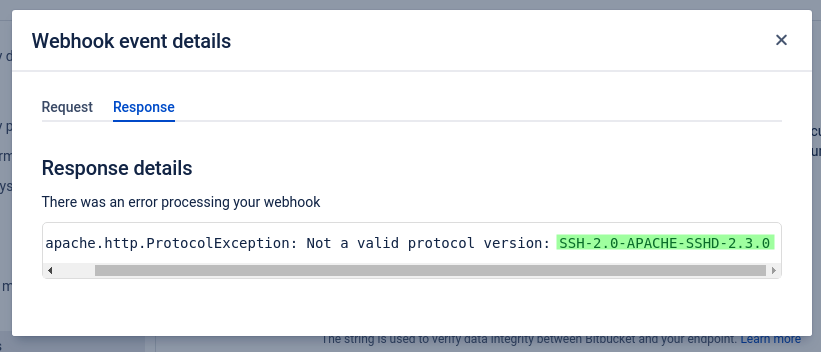
The last image shows the Apache MINA SSHD banner on port 15998 that we found running on this instance of Bitbucket Server.
Fix
Consider adding an instance-wide whitelisting feature or deploy a comprehensive filtering of local and internal IP addresses.
References
https://owasp.org/www-community/attacks/Server_Side_Request_Forgery
Timeline
- 2020-03-12 First contact request via security@atlassian.com
- 2020-05-20 Contact request via Support forum
- 2020-07-08 Vendor publishes advisory: https://jira.atlassian.com/browse/BSERV-12433
- 2020-07-15 Security advisory released
Credits
This security vulnerability was found by Marcus Nilsson of usd AG.