usd-2020-0053 | Gophish v0.10.1
Advisory ID: usd-2020-0053
CVE Number: CVE-2020-24713
Affected Product: Gophish
Affected Version: v0.10.1
Vulnerability Type: Insufficient Session Expiration
Security Risk: High
Vendor URL: https://getgophish.com/
Vendor Status: Fix scheduled
Description
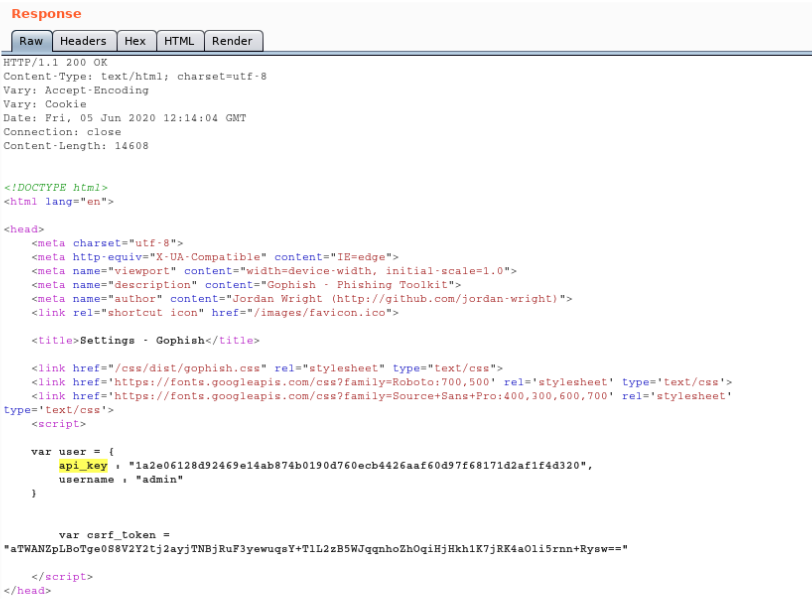
The client’s session cookie “gophish” doesn’t get invalidated on the server side upon logout. A new cookie is sent to the client however the old session cookie can be used for browsing the settings page and to retrieve the API key.
Proof of Concept (PoC)
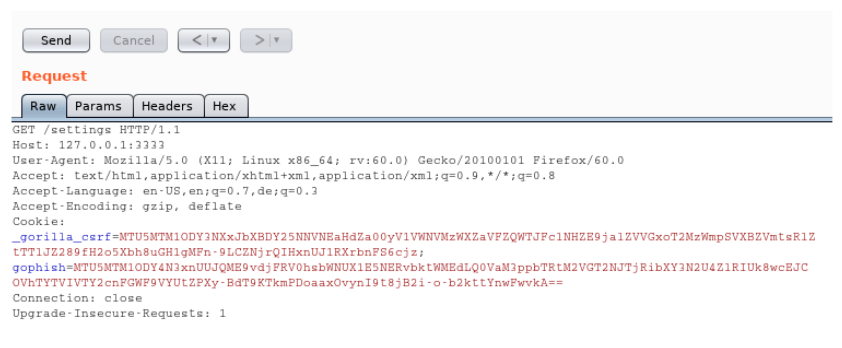
A user’s session is not invalidated on the server-side upon logout. Hence, it is possible to continue browsing pages using the old session and a web application proxy such as Burp. The following screenshot illustrates how an HTTP request containing a logged out session returns the same response as if the session’s owner was still logged in.
- Logout using /logout
- Replay previously captured request to
/settings(including old cookie) – observe that the session was not invalidated server-side
Fix
Upon logout, user sessions should be terminated both client and server side.
Timeline
- 2020-06-18 First contact request via security@getgophish.com
- 2020-06-22 Vendor responds to initial contact
- 2020-08-20 Vendor accepts the risk of publication while waiting for the underlying authentication library to fix the issue
- 2020-09-29 Security advisory released
Credits
This security vulnerability was found by Marcus Nilsson of usd AG.