usd-2021-0002 | EgoSecure Agent
Advisory ID: usd-2021-0002
Affected Product: EgoSecure Agent
Affected Version: 14.3.937.4
Vulnerability Type: Symlink Vulnerability
Security Risk: High
Vendor URL: https://www.egosecure.com/
Vendor Status: Fixed (21.0.1)
Description
Privileged file write vulnerabilities allow low privileged users to create or overwrite files in arbitrary locations of the file system.
The impact of these attacks depends largely on the content that is written to the files. If the content is user controlled,
privilege escalations are usually possible. Otherwise, the vulnerability can be used to perform Denial of Service attacks.
Proof of Concept (PoC)
The EgoSecure Agent service allows users to request a compacted collection of log files using the EgoSecure tray icon. When invoking this operation,
the EgoSecure Agent collects log data and compacts everything into a single .zip file. The corresponding folder, where the compressed .zip file
is created, is user controlled, but can only be set to a user writable location. However, by using symbolic links, this restriction can be circumvented
and the .zip file can be written to arbitrary locations of the file system. As the write operations is done with the high privileged service account,
no write access is required for the invoking user.
In the following screenshot, a low privileged user starts the log compression via the EgoSecure tray icon and sets the output folder to a user controlled
area of the file system:
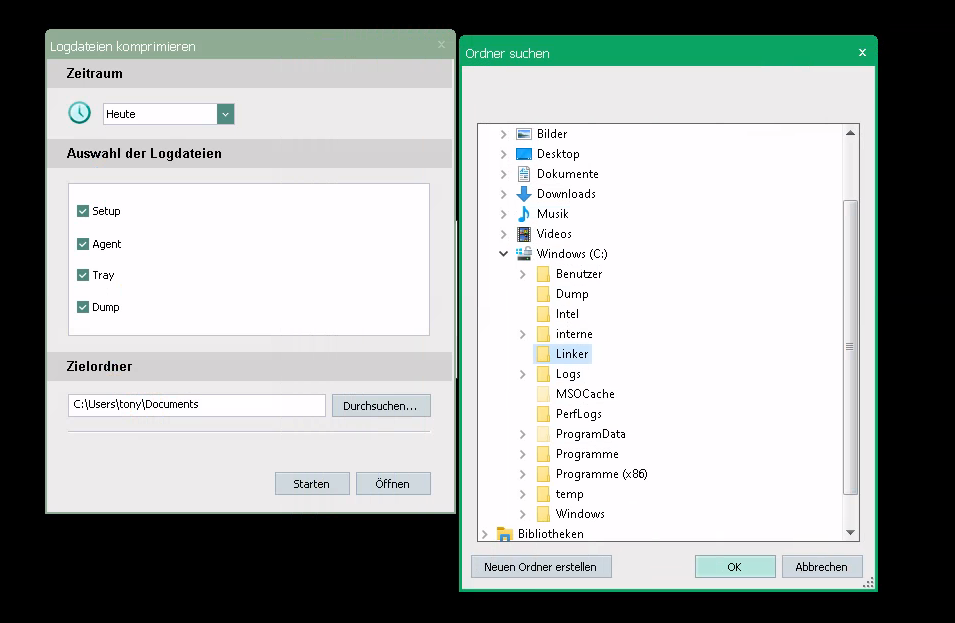
Afterwards, the user creates a symbolic link that points to the desired location of the file system. During our tests, only non existing paths could be
chosen. For the symbolic link creation, we use the symboliclink-testing-tools by James Forshaw.
C:\>C:\ProgramData\CreateSymlink.exe C:\Linker\LogFiles_20210131.zip C:\Windows\this_should_not_be_here.dll
Opened Link \RPC Control\LogFiles_20210131.zip -> \??\C:\Windows\this_should_not_be_here.dll: 00000184
Press ENTER to exit and delete the symlink
After starting the export, the .zip file is created in the requested destination:
C:\>dir C:\Windows\this_should_not_be_here.dll
Volume in drive C is Windows
Volume Serial Number is F653-D506
Directory of C:\Windows
31.01.2021 11:53 384.182 this_should_not_be_here.dll
1 File(s), 384.182 bytes
0 Dir(s), 461.815.877.632 bytes free
Fix
References
Timeline
- 2021-01-31: This vulnerability was identified by Tobias Neitzel.
- 2021-02-13: Initial contact to vendor.
- 2021-02-14: Vulnerability information transmitted to vendor.
- 2021-02-15: Vendor informs about upcoming fix.
- 2021-09-27: Vulnerability was fixed in release 21.0.1.
- 2021-09-30: Security advisory released by usd AG.
Credits
This security vulnerability was found by Tobias Neitzel of usd AG.