usd-2021-0020 | Microsoft Exchange Server ECP
Advisory ID: usd-2021-0020
Affected Product: Microsoft Exchange Server
Affected Version: Latest (Exchange Server 2016, Version 15.1 (Build 2242.4))
Vulnerability Type: CWE-918: Server-Side Request Forgery (SSRF)
Security Risk: Medium
Vendor URL: https://microsoft.com
Vendor Status: Not fixed / Disputed
The following behavior was reported to Microsoft in May 2021. After finishing their investigations, Microsoft informed us that this issue does not meet their bar for servicing in a security update.
Description
The application can be made to perform requests to other services. From the perspective of those other services it looks like the requests originated from the vulnerable application. By issuing such server-side requests, an attacker may be able to access services that are bound to the local interface of the vulnerable system and would therefore normally not be reachable over the network. In addition, an SSRF attack can provide access to the local network in which the server is located.
The Exchange Server’s ECP component allows to manage Add-Ins. In doing so, users may install Add-ins using multiple mechanisms, including installation by URL. The Exchange Server does not sufficiently validate the provided URL, resulting in SSRF to localhost.
Proof of Concept (PoC)
1. Login to the ECP interface at https://mail.example.com/ecp
2. Go to "Organization" > "Add-ins".
3. Choose "Add from URL" and enter `http://localhost:22` as URL.
The following request aims to add a new Add-In by URL:
Host: mail.example.com
Connection: close
Content-Length: 138
User-Agent: Mozilla/5.0 [...]
Referer: https://mail.example.com/ecp/Extension/InstallFromPrivateUrl.aspx?pwmcid=2&ReturnObjectType=1
Cookie: [REDACTED]
{"properties":{"Parameters":{"__type":"JsonDictionaryOfanyType:#Microsoft.Exchange.Management.ControlPanel","Url":"http://localhost:22"}}}
4. By testing multiple ports at localhost as `Url` parameter, clear timing differences can be observed:
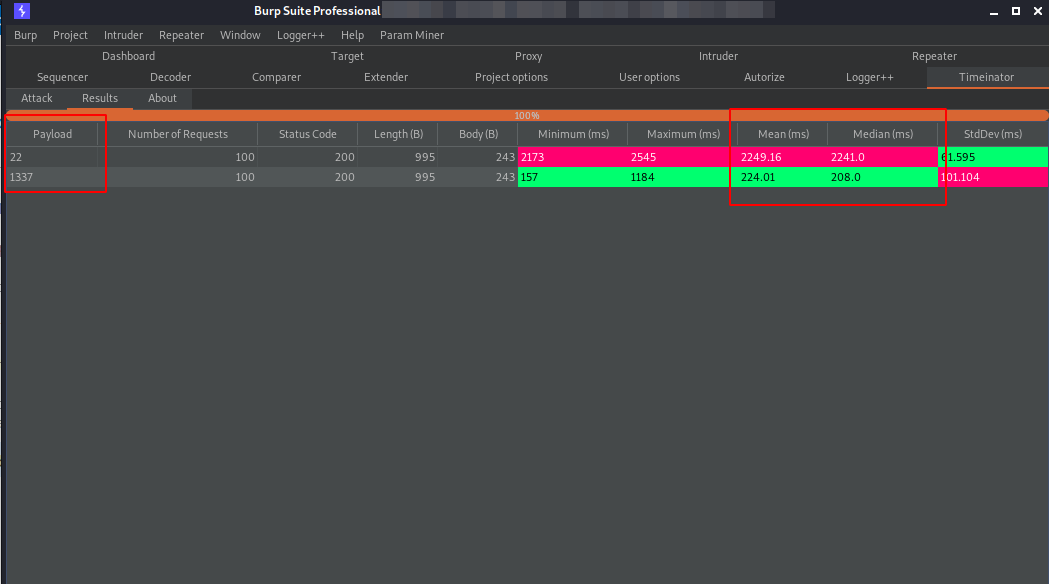
Impact
A malicious actor could utilize the aforementioned different response times to perform port scans of localhost or the local network.
Fix
It is recommended to evaluate the need to make server-side requests. If server-side requests are absolutely necessary, the corresponding function should be restricted by a whitelisting approach.
References
- https://cwe.mitre.org/data/definitions/918.html
- https://owasp.org/www-community/attacks/Server_Side_Request_Forgery
- MSRC Case 65226 - usd20210021: Comparable issue in MS Exchange's OWA component
Timeline
- 2021-05-03: This vulnerability was identified by Lauritz Holtmann.
- 2021-05-07: Advisory submitted to vendor via e-mail.
-
2021-05-17: Vendor states he is unable to reproduce finding.
- 2021-05-19: Additional information provided by usd AG.
- 2021-07-20: Vendor issues statement: "Upon investigation, we have determined that this submission does not meet the definition of a security vulnerability for servicing. This report does not appear to identify a weakness in a Microsoft product or service that would enable an attacker to compromise the integrity, availability, or confidentiality of a Microsoft offering."
-
2021-10-30: Advisory is published by usd AG.
Credits
This security vulnerability was found by Lauritz Holtmann of usd AG.