usd-2021-0031 (CVE-2022-22689) | CA Harvest Software Change Manager
Advisory ID: usd-2021-0031
CVE ID: CVE-2022-22689
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-22689
Affected Product: CA Harvest Software Change Manager
Affected Versions: v13.0.3, v13.0.4, v14.0.0, v14.0.1, see vendor advisory
Vulnerability Type: CWE-1236: Improper Neutralization of Formula Elements in a CSV File
Security Risk: High
Vendor URL: https://www.broadcom.com/products/software/business-management/ca-service-management/harvest-software-change-manager
Vendor Status: Fixed
Description
The client allows to export peer review lists. There is no filtering, so that an Office formula can be used as a name for a package. This formula can then be exported to a CSV file and will be evaluated once the CSV file is opened in a spreadsheet program. This vulnerability can only be exploited by users with higher privileges.
A CSV injection occurs if data containing office formulas is exported unfiltered to CSV files. If the exported files are opened in a spreadsheet program, such as Microsoft Excel, these formulas is evaluated on the users computer.
The Harvest Software Change Manager allows users with higher privileges to create packages. As package names office formulas can be used. This package then must be sent to review using the functionality in the context menu "Request for Peer Review".
Another user is able to export a PendingReviewsList where this package name is contained if sent to peer review. If this exported CSV file is then opened in a spreadsheet program the formulas are evaluated.
Proof of Concept (PoC)
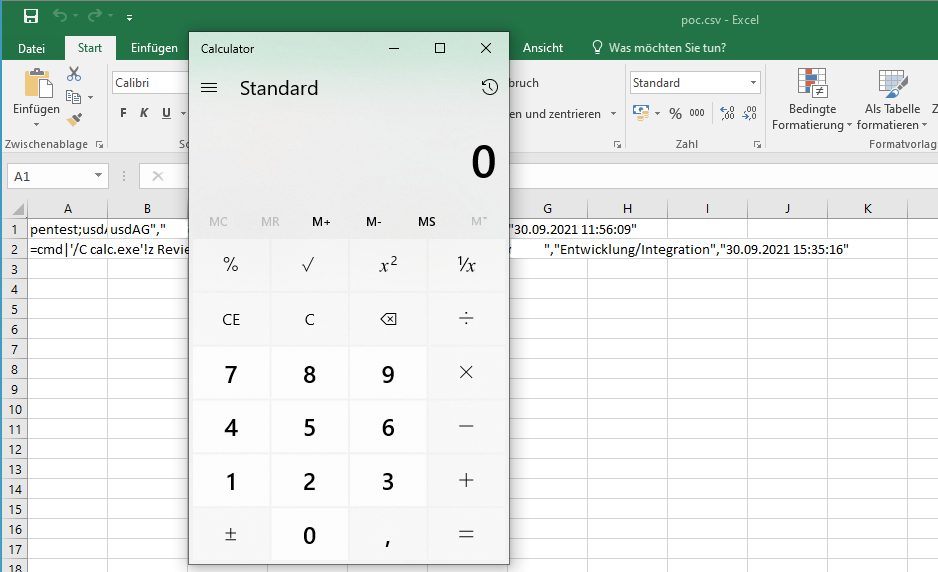
1. Create a package with the following name: =cmd | '/C calc.exe' !z
2. Send this package to peer review using context menu "Request for Peer Review".
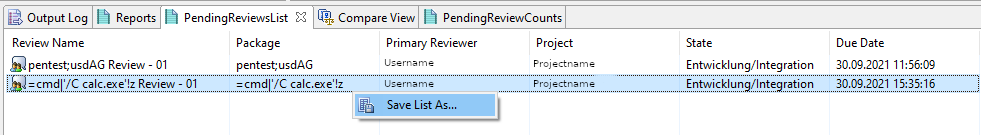
3. Visit the PendingReviewsList.
4. Right click on any item and use the option "Save List As...":
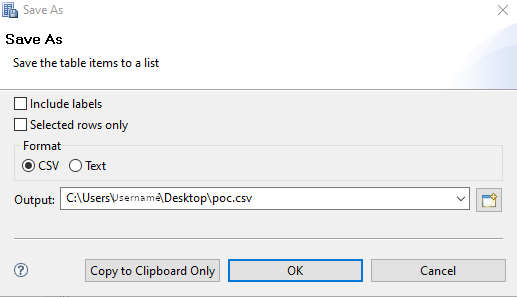
5. Select CSV and export the file:
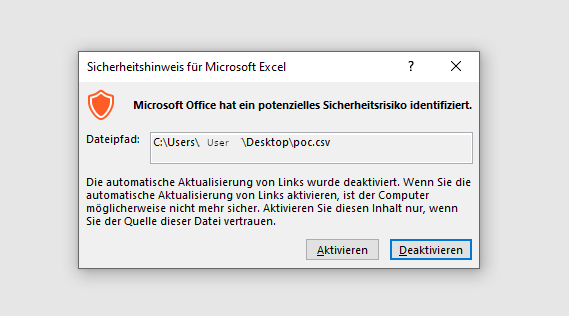
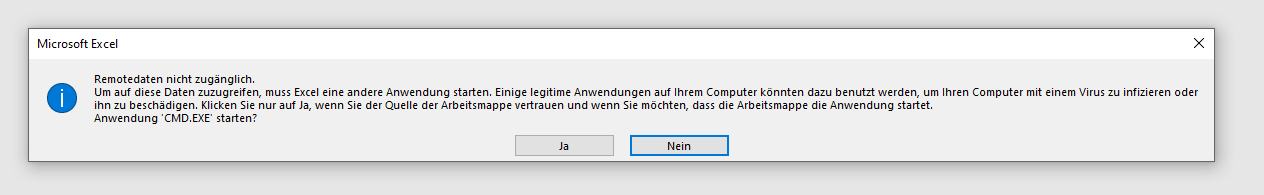
6. Open the file and accept the security risk warnings (two are shown in MS Excel):
6. Calc.exe is executed:
Fix
It is recommended to restrict the set of allowed characters as much as possible for all user input. This can, for example, be realized with a whitelist. Additionally, every cell that starts with an equal- (=), a plus- (+), a minus- (-) or an at-sign (@), or contains a comma (,) or a semicolon (;) should be prepended with a single quote and embedded in double quotes (") when generating spreadsheets, such as .csv, .xls or .xlsx files, automatically (https://owasp.org/www-community/attacks/CSV_Injection). Furthermore, every double quote occurring within the content of a cell should be preceded by another double quote to avoid an early termination of the quoted string. In order to achieve this, a suitable library can be used.
References
- https://cwe.mitre.org/data/definitions/1236.html
- https://owasp.org/www-community/attacks/CSV_Injection
Timeline
-
2021-11-04: vulnerability identified by Merten Nagel.
-
2021-11-09: advisory submitted via e-mail (https://www.broadcom.com/support/resources/product-security-center).
- 2022-01-29: CVE-2022-22689 is assigned by vendor.
- 2022-02-03: The vendor releases updates for all affected and supported versions, the following advisory is published: https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/security-advisories/CA20220203-01-Security-Notice-for-CA-Harvest-Software-Change-Manager/ESDSA20297
- 2022-07-04: This advisory is published.
Credits
This security vulnerability was identified by Merten Nagel of usd AG.