usd-2021-0032 | SUSE CVE Database (suse.com)
Advisory ID: usd-2021-0032
Affected Product: SUSE CVE database
Vulnerability Type: CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
Security Risk: High
Vendor URL: https://www.suse.com/security/cve/
Vendor Status: Fixed
Description
Suse's CVE database embedded third-party contents without sufficient filtering and/or encoding. Multiple incidents have been identified where Suse embedded untrusted <script> tags, resulting in stored Cross-Site-Scripting (XSS).
SUSE's CVE database is a website which displays information on public CVEs. The description part of CVE records is included into the website without filtering or escaping of the respective content. A malicious actor could have included JavaScript code in the description text of a CVE. This code would then have been included within a page of the SUSE CVE database and could have been be misused for a stored cross-site scripting attack.
Proof of Concept (PoC)
In order to exploit the vulnerability, a new CVE record must be published officially. This CVE record can contain arbitrary text as a "description". Here, JavaScript code can injected. The SUSE CVE database imports this data automatically and displays the information on a website. The injected code will be executed automatically.
An example CVE containing an HTML <script> tag is CVE-2021-32718 (https://www.suse.com/security/cve/CVE-2021-32718.html). Here, the HTML tag was interpreted and potentially malicious JavaScript code which could follow here would have been executed.
The following screenshots illustrate that the <script> tag is embedded without any encoding or filtering and interpreted as markup by the browser accordingly:
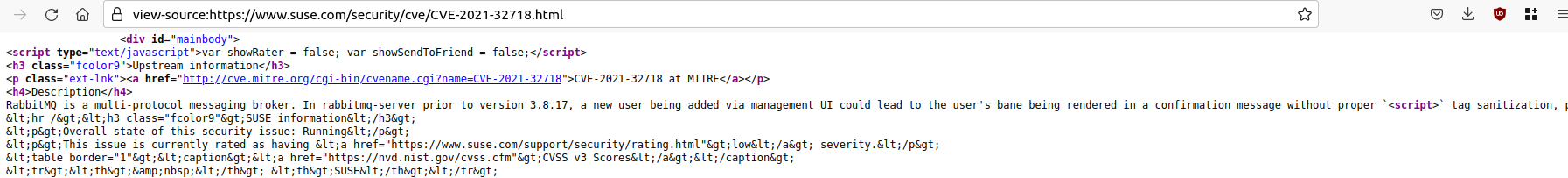
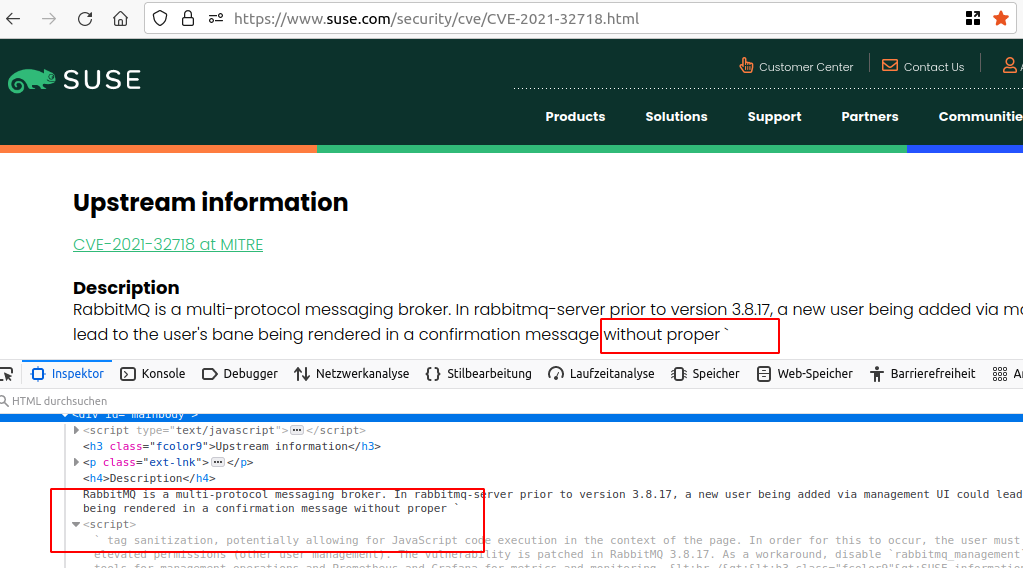
Fix
It is recommended to treat all input on the website as potentially dangerous. Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context. The majority of programming languages supports standard procedures for encoding meta characters.
References
Timeline
-
2021-11-10: The vulnerability is identified by Christian Rellmann.
-
2021-11-10: The vulnerability is submitted via e-mail to security@suse.com and security@suse.de at 15:09 CET.
- 2021-11-10: Suse acknowledges vulnerability and informs us that a fix was deployed at 17:06 CET.
- 2021-11-30: Security advisory released by usd AG.
Credits
This security vulnerability was found by Christian Rellmann of usd AG.